Last Update 23 hours ago Total Questions : 36
The Oracle Cloud Infrastructure 2025 Security Professional content is now fully updated, with all current exam questions added 23 hours ago. Deciding to include 1z0-1104-25 practice exam questions in your study plan goes far beyond basic test preparation.
You'll find that our 1z0-1104-25 exam questions frequently feature detailed scenarios and practical problem-solving exercises that directly mirror industry challenges. Engaging with these 1z0-1104-25 sample sets allows you to effectively manage your time and pace yourself, giving you the ability to finish any Oracle Cloud Infrastructure 2025 Security Professional practice test comfortably within the allotted time.
Challenge 2
In deploying a new application, a cloud customer needs to reflect different security postures. If a security zone is enabled with the Maximum Security Zone recipe, the customer will be unable to create or update a resource in the security zone if the action violates the attached Maximum Security Zone policy.
As an application requirement, the customer requires a compute instance in the public subnet. You therefore, need to configure Custom Security Zones that allow the creation of compute instances in the public subnet.
Review the architecture diagram, which outlines the resoures you'll need to address the requirement:
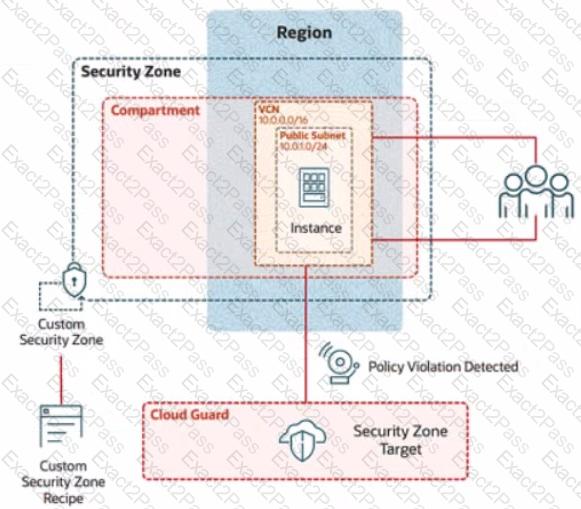
Preconfigured
To complete this requirement, you are provided with the following:
Access to an OCI tenancy, an assigned compartment, and OCI credentials
Required IAM policies
Task 5: Provision a Compute Instance
Provision a compute instance in the IAD-SP-PBT-PUBSNET-01 public subnet, where:
Name IAD-SP-PBT-1-VM-01
image: Oracle Linux 8
Shape VM: Standard, A1, Flex
Enter the OCID of the created compute instance in the text box below.
Challenge 2 -Task 1
In deploying a new application, a cloud customer needs to reflect different security postures. If a security zone is enabled with the Maximum Security Zone recipe, the customer will be unable to create or update a resource in the security zone if the action violates the attached Maximum Security Zone policy.
As an application requirement, the customer requires a compute instance in the public subnet. You therefore, need to configure Custom Security Zones that allow the creation of compute instances in the public subnet.
Review the architecture diagram, which outlines the resoures you'll need to address the requirement:
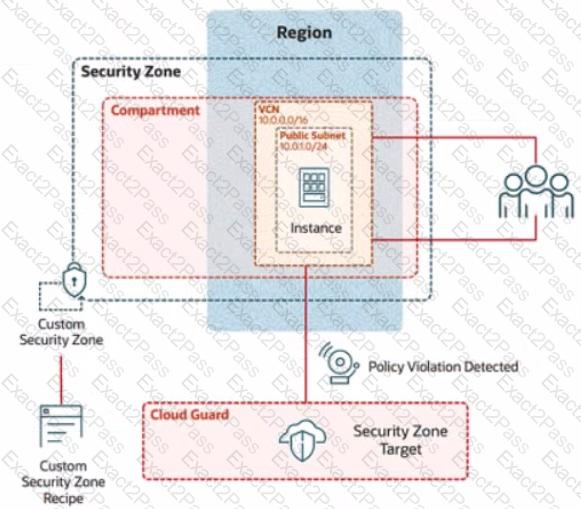
Preconfigured
To complete this requirement, you are provided with the following:
Access to an OCI tenancy, an assigned compartment, and OCI credentials
Required IAM policies
Task3: Create and configure a Virtual Cloud Network and Private Subnet
Createand configure virtual cloud Network (VCN) named IAD SP-PBT-VCN-01, with an internet Gateway and configure appropriate route rules to allow external connectivity.
Enter the OCID of the created VCN in the text box below.
Based on the provided diagram, you have a group of critical compute instances in a private subnet that require vulnerability using the Oracle Cloud Infrastructure(OCI) Vulnerability Scanning Service (VSS).
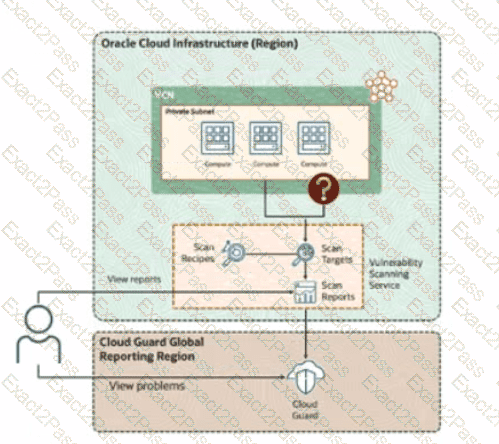
"What additional configuration is required to enable VSS to scan instances in the private subnet
"You are part of the security operations of an organization with thousands of users accessing Oracle Cloud Infrastructure (OCI). It is reported that an unknown user action was executed resulting in configuration errors. You are tasked with identifying the details of all users who were active in the last six hours along with any REST API calls that were executed.
Which OCI feature should you use?
A company has implemented OCI IAM policies with multiple levels of compartments. A policy attached to a parent compartment grants "manage virtual-network-family" permissions. A policy attached to a child compartment grants "use virtual-network-family" permissions.
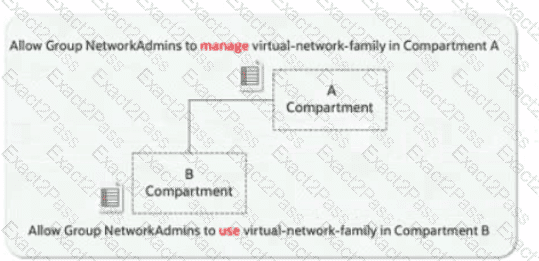
According to OCI IAM policy inheritance, how does the OCI IAM policy engine resolve the permissions for a user attempting to perform an operation that requires 'manage' permissions in the child compartment?
A company is securing its compute instances (VMs and Bare Metal Machines) in Oracle Cloud infrastructure (OCI) using a network firewall. As shown in the diagram, traffic flows from the internet Gateway (IGW) to the firewall in the Public DMZ Subnet, and then to the compute instances in the Public Subnet.
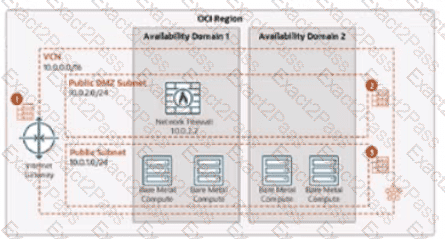
When configuring security lists and network security groups (NSGs) in this setup, what should they consider?
"A programmer is developing a Node.js application which will run on a Linux server on their on-premises data center. This application will access various Oracle Cloud Infrastructure (OCI) services using OCI SDKs.
What is the secure way to access OCI services with OCI Identity and Access Management (IAM)?

