Last Update 21 hours ago Total Questions : 481
The DevNet Associate (DEVASC) content is now fully updated, with all current exam questions added 21 hours ago. Deciding to include 200-901 practice exam questions in your study plan goes far beyond basic test preparation.
You'll find that our 200-901 exam questions frequently feature detailed scenarios and practical problem-solving exercises that directly mirror industry challenges. Engaging with these 200-901 sample sets allows you to effectively manage your time and pace yourself, giving you the ability to finish any DevNet Associate (DEVASC) practice test comfortably within the allotted time.
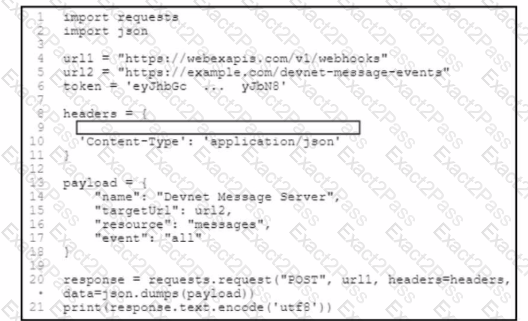
Refer to the exhibit. A developer needs to create a webhook to send all Cisco Webex messages to a third-party tool by using the Cisco Webex API. The developer must Auhenticate with the API before any API calls can be made. To automate the procedure, a Python script is used. Which code snippet must be placed onto the blank in the code?
A)

B)

C)

D)

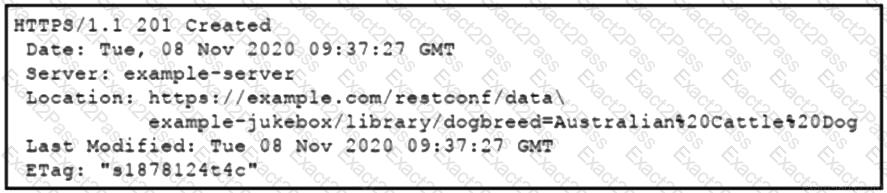
Refer to the exhibit. Which RESTCONF request results in this response?
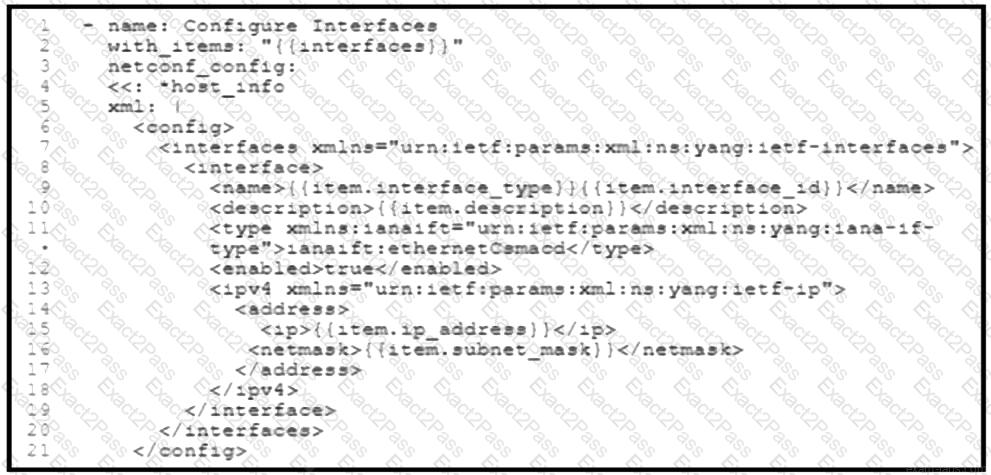
Refer to the exhibit. A network engineer must configure new interfaces on a set of devices and is planning to use an Ansible playbook for the task. All devices support SSH and NETCONF protocol, and the interface variables are unique per device. In which directory are the YAML files including variables hosted to automate the task with the netconf_config module?
How do XML and JSON compare regarding functionality?
Refer to the exhibit.
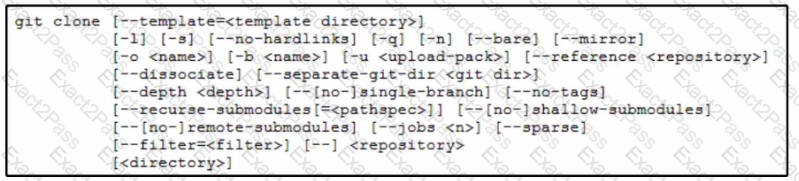
A network engineer must improve the fabric discovery process in a data center. The engineer wants to check current ACI scripts in the myproject repository and clone them to a folder named aci. The engineer will optimize the scripts from the new folder. Which command performs this task on the Git repository?
A)

B)

C)

D)

Which port does HTTPS use by default?
Which type of OWASP threat forges a malicious HTTP request into an application?

