Last Update 16 hours ago Total Questions : 119
The LPIC-2 - Exam 202 (part 2 of 2), version 4.5 content is now fully updated, with all current exam questions added 16 hours ago. Deciding to include 202-450 practice exam questions in your study plan goes far beyond basic test preparation.
You'll find that our 202-450 exam questions frequently feature detailed scenarios and practical problem-solving exercises that directly mirror industry challenges. Engaging with these 202-450 sample sets allows you to effectively manage your time and pace yourself, giving you the ability to finish any LPIC-2 - Exam 202 (part 2 of 2), version 4.5 practice test comfortably within the allotted time.
Which option within a Nginx server configuration section defines the file system path from which the content of the server is retrieved?
Which option in named.conf specifies which host are permitted to ask for domain name information from the server?
It has been discovered that the company mail server is configured as an open relay. Which of the following actions would help prevent the mail server from being used as an open relay while maintaining the possibility to receive company mails? (Choose two.)
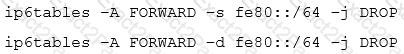
Which of the statements below are correct regarding the following commands, which are executed on a Linux router? (Choose two.)
Which of the following are logging directives in Apache HTTPD? (Choose two.)
Select the Samba option below that should be used if the main intention is to setup a guest printer service?
Which of the following Samba services handles the membership of a file server in an Active Directory domain?

