Last Update 11 hours ago Total Questions : 47
The Certified Application Security Engineer (CASE) JAVA content is now fully updated, with all current exam questions added 11 hours ago. Deciding to include 312-96 practice exam questions in your study plan goes far beyond basic test preparation.
You'll find that our 312-96 exam questions frequently feature detailed scenarios and practical problem-solving exercises that directly mirror industry challenges. Engaging with these 312-96 sample sets allows you to effectively manage your time and pace yourself, giving you the ability to finish any Certified Application Security Engineer (CASE) JAVA practice test comfortably within the allotted time.
According to secure logging practices, programmers should ensure that logging processes are not disrupted by:
Which of the following is used to mapCustom Exceptions to Statuscode?
In which phase of secure development lifecycle the threat modeling is performed?
Sam, an application security engineer working in INFRA INC., was conducting a secure code review on an application developed in Java. He found that the developer has used a piece of code as shown in the following screenshot. Identify the security mistakes that the developer has coded?
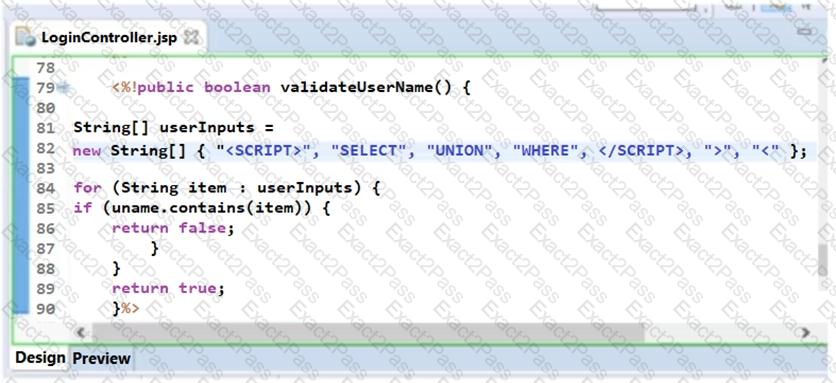
Which of the following method will help you check if DEBUG level is enabled?
Alice, a security engineer, was performing security testing on the application. He found that users can view the website structure and file names. As per the standard security practices, this can pose a serious security risk as attackers can access hidden script files in your directory. Which of the following will mitigate the above security risk?
Which of the following state management method works only for a sequence of dynamically generated forms?

