Last Update 13 hours ago Total Questions : 139
The Performing CyberOps Using Core Security Technologies (CBRCOR) content is now fully updated, with all current exam questions added 13 hours ago. Deciding to include 350-201 practice exam questions in your study plan goes far beyond basic test preparation.
You'll find that our 350-201 exam questions frequently feature detailed scenarios and practical problem-solving exercises that directly mirror industry challenges. Engaging with these 350-201 sample sets allows you to effectively manage your time and pace yourself, giving you the ability to finish any Performing CyberOps Using Core Security Technologies (CBRCOR) practice test comfortably within the allotted time.
Refer to the exhibit.
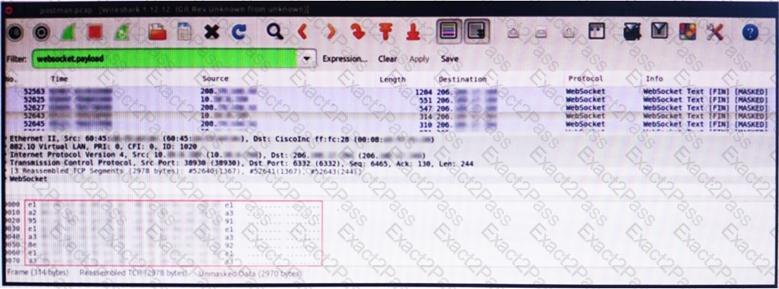
An engineer is analyzing this Vlan0386-int12-117.pcap file in Wireshark after detecting a suspicious network activity. The origin header for the direct IP connections in the packets was initiated by a google chrome extension on a WebSocket protocol. The engineer checked message payloads to determine what information was being sent off-site but the payloads are obfuscated and unreadable. What does this STIX indicate?
Which command does an engineer use to set read/write/execute access on a folder for everyone who reaches the resource?
Refer to the exhibit.
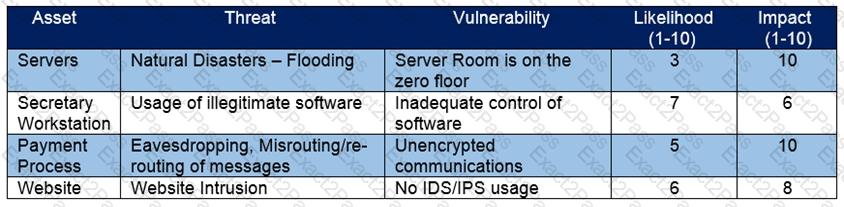
Which asset has the highest risk value?
Refer to the exhibit.
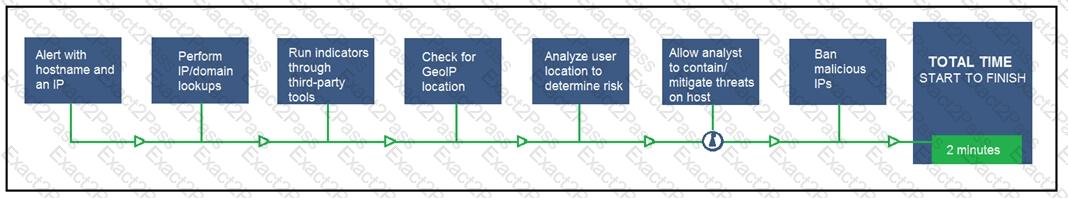
An engineer configured this SOAR solution workflow to identify account theft threats and privilege escalation, evaluate risk, and respond by resolving the threat. This solution is handling more threats than Security analysts have time to analyze. Without this analysis, the team cannot be proactive and anticipate attacks. Which action will accomplish this goal?
Refer to the exhibit.
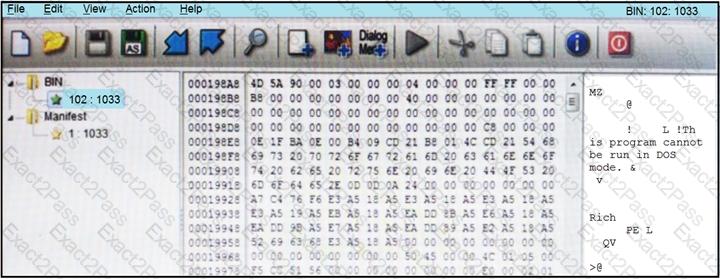
An engineer is reverse engineering a suspicious file by examining its resources. What does this file indicate?
Refer to the exhibit.
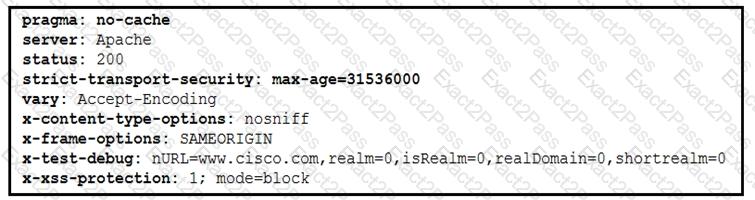
Where are the browser page rendering permissions displayed?