Last Update 22 hours ago Total Questions : 118
The CompTIA DataSys+ Certification Exam content is now fully updated, with all current exam questions added 22 hours ago. Deciding to include DS0-001 practice exam questions in your study plan goes far beyond basic test preparation.
You'll find that our DS0-001 exam questions frequently feature detailed scenarios and practical problem-solving exercises that directly mirror industry challenges. Engaging with these DS0-001 sample sets allows you to effectively manage your time and pace yourself, giving you the ability to finish any CompTIA DataSys+ Certification Exam practice test comfortably within the allotted time.
Which of the following indexes stores records in a tabular format?
(A healthcare company relies on contact forms and surveys on its website to properly communicate with patients. To which of the following attacks is the company’s data most vulnerable?)
(Which of the following best describe a tablespace? Select two.)
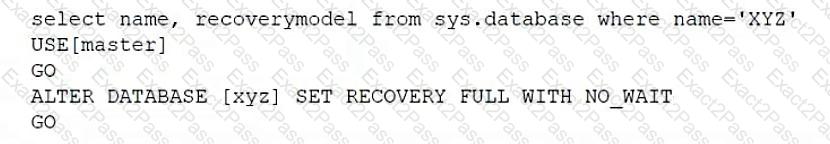
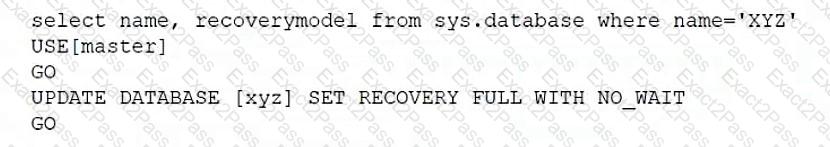
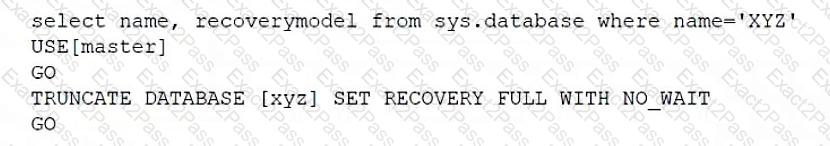
Which of the following scripts would set the database recovery model for sys.database?
A)
B)
C)
D)

(A database manager would like to reduce the overhead caused by log-based recoveries. Which of the following should the manager use to best mitigate the situation?)
(A database administrator has configured a Resource Governor with three resource pools. The first resource pool is assigned a minimum CPU and memory value of 25%. The second resource pool is assigned a minimum CPU and memory value of 35%. The database administrator wants to assign the maximum CPU and the maximum resource pool to the third resource. Which of the following is the maximum the database administrator should assign to the third resource?)
A database administrator needs to ensure that a newly installed corporate business intelligence application can access the company’s transactional data. Which of the following tasks should the administrator perform first?

