Last Update 9 hours ago Total Questions : 107
The Junos - Associate (JNCIA-Junos) 2025 Exam content is now fully updated, with all current exam questions added 9 hours ago. Deciding to include JN0-105 practice exam questions in your study plan goes far beyond basic test preparation.
You'll find that our JN0-105 exam questions frequently feature detailed scenarios and practical problem-solving exercises that directly mirror industry challenges. Engaging with these JN0-105 sample sets allows you to effectively manage your time and pace yourself, giving you the ability to finish any Junos - Associate (JNCIA-Junos) 2025 Exam practice test comfortably within the allotted time.
You want to find out the chassis serial number of a Junos device.
Which command would display this information?
Your router has a route to the 10.1.1.0/24 network with a next hop of r jet.
In this scenario, which action will your router perform when traffic destined to the 10.1.1.0/24 network is received?
What will the request system configuration rescue save command do?
What information would you find using the CLI help command?
What is a benefit of using J-Web?
You received a new Junos device and are configuring the system-related settings. You must configure this device for the current date and time on the US West coast. You have set the time zone to America/Los_Angeies. however the time and date did not change.
In this scenario, which two additional actions would satisfy this requirement? (Choose two.)
Click the Exhibit button.
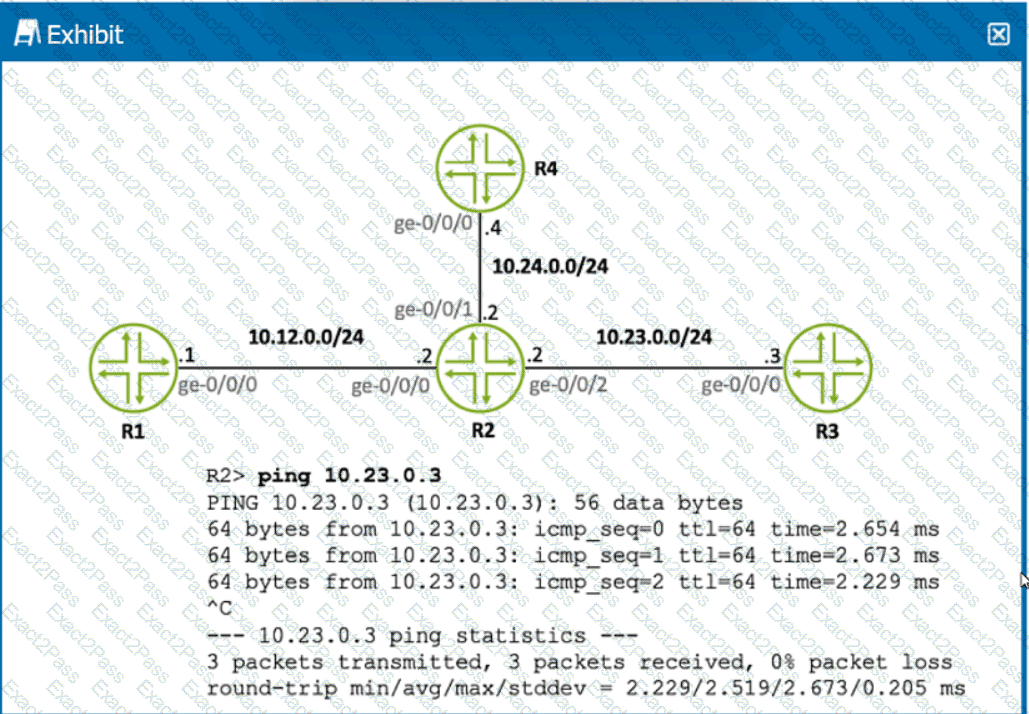
Referring to the exhibit, what is the source IP address of the ping that was executed?

