Last Update 23 hours ago Total Questions : 115
The Security, Professional (JNCIP-SEC) content is now fully updated, with all current exam questions added 23 hours ago. Deciding to include JN0-636 practice exam questions in your study plan goes far beyond basic test preparation.
You'll find that our JN0-636 exam questions frequently feature detailed scenarios and practical problem-solving exercises that directly mirror industry challenges. Engaging with these JN0-636 sample sets allows you to effectively manage your time and pace yourself, giving you the ability to finish any Security, Professional (JNCIP-SEC) practice test comfortably within the allotted time.
You configured a chassis cluster for high availability on an SRX Series device and enrolled this HA cluster with the Juniper ATP Cloud. Which two statements are correct in this scenario? (Choose two.)
Exhibit
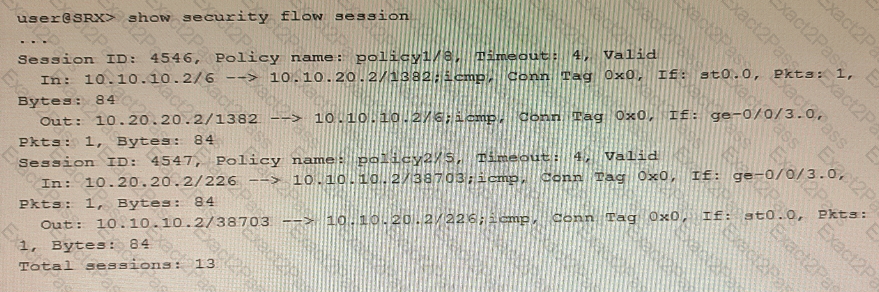
You are validating bidirectional traffic flows through your IPsec tunnel. The 4546 session represents traffic being sourced from the remote end of the IPsec tunnel. The 4547 session represents traffic that is sourced from the local network destined to the remote network.
Which statement is correct regarding the output shown in the exhibit?
What are two valid modes for the Juniper ATP Appliance? (Choose two.)
Exhibit
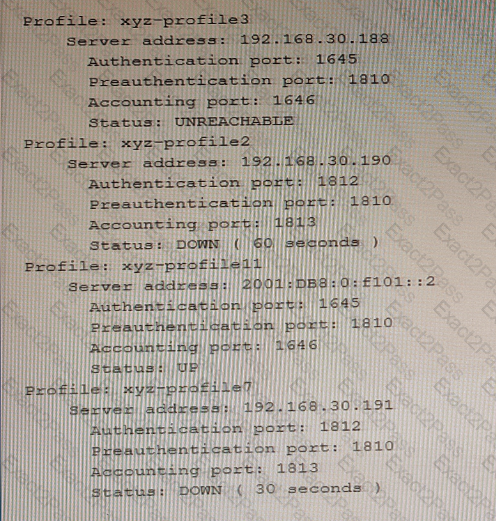
The show network-access aaa radius-servers command has been issued to solve authentication issues.
Referring to the exhibit, to which two authentication servers will the SRX Series device continue to send requests? (Choose TWO)
You want to enforce I DP policies on HTTP traffic.
In this scenario, which two actions must be performed on your SRX Series device? (Choose two )
You are asked to share threat intelligence from your environment with third party tools so that those
tools can be identify and block lateral threat propagation from compromised hosts.
Which two steps accomplish this goal? (Choose Two)
Exhibit
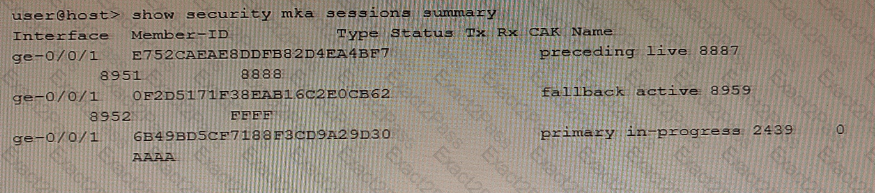
Referring to the exhibit, which two statements are true about the CAK status for the CAK named "FFFP"? (Choose two.)

