Refer to the exhibits.
Exhibit A
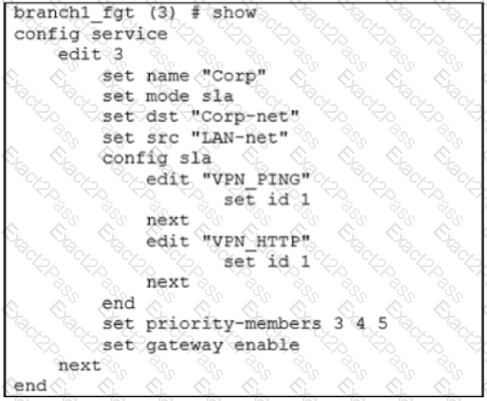
Exhibit B -
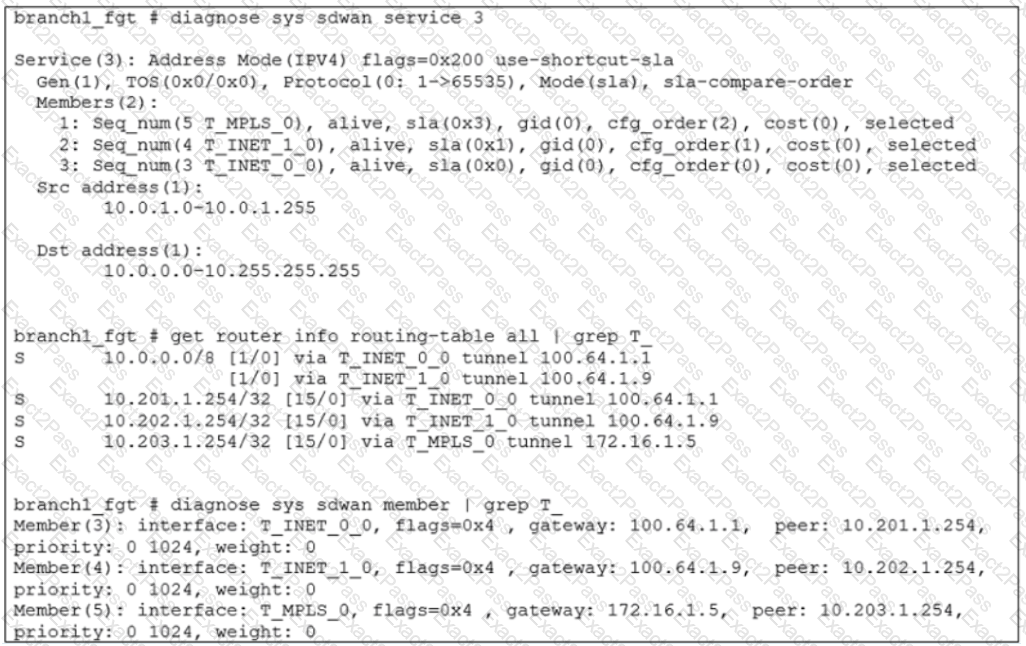
Exhibit A shows the configuration for an SD-WAN rule and exhibit B shows the respective rule status, the routing table, and the member status.
The administrator wants to understand the expected behavior for traffic matching the SD-WAN rule.
Based on the exhibits, what can the administrator expect for traffic matching the SD-WAN rule?
Which are two benefits of using CLI templates in FortiManager? (Choose two.)
Which two statements are true about using SD-WAN to steer local-out traffic? (Choose two.)
Refer to the exhibits.
Exhibit A

Exhibit B

Exhibit A shows the SD-WAN performance SLA configuration, the SD-WAN rule configuration, and the application IDs of Facebook and YouTube. Exhibit B shows the firewall policy configuration and the underlay zone status.
Based on the exhibits, which two statements are correct about the health and performance of port1 and port2? (Choose two.)

Two hub-and-spoke groups are connected through a site-to-site IPsec VPN between Hub 1 and Hub 2. The administrator configured ADVPN on both hub-and-spoke groups.
Which two outcomes are expected if a user in Toronto sends traffic to London? (Choose two.)
Which diagnostic command can you use to show the member utilization statistics measured by performance SLAs for the last 10 minutes?
Refer to the exhibit.

Based on the exhibit, which two statements are correct about the health of the selected members? (Choose two.)
Refer to the exhibit.

FortiGate has multiple dial-up VPN interfaces incoming on port1 that match only FIRST_VPN.
Which two configuration changes must be made to both IPsec VPN interfaces to allow incoming connections to match all possible IPsec dial-up interfaces? (Choose two.)
What are two benefits of using forward error correction (FEC) in IPsec VPNs? (Choose two.)
In a hub-and-spoke topology, what are two advantages of enabling ADVPN on the IPsec overlays? (Choose two.)
Refer to the exhibit.

An administrator is troubleshooting SD-WAN on FortiGate. A device behind branch1_fgt generates traffic to the 10.0.0.0/8 network. The administrator expects the traffic to match SD-WAN rule ID 1 and be routed over T_INET_0_0. However, the traffic is routed over T_INET_1_0.
Based on the output shown in the exhibit, which two reasons can cause the observed behavior? (Choose two.)
Refer to the exhibit.

Based on the exhibit, which two actions does FortiGate perform on sessions after a firewall policy change? (Choose two.)
Refer to the exhibit.

The exhibit shows the SD-WAN rule status and configuration.
Based on the exhibit, which change in the measured packet loss will make T_INET_1_0 the new preferred member?
Refer to the exhibit.

The exhibit shows the BGP configuration on the hub in a hub-and-spoke topology. The administrator wants BGP to advertise prefixes from spokes to other spokes over the IPsec overlays, including additional paths. However, when looking at the spoke routing table, the administrator does not see the prefixes from other spokes and the additional paths.
Based on the exhibit, which three settings must the administrator configure inside each BGP neighbor group so spokes can learn other spokes prefixes and their additional paths? (Choose three.)