Last Update 21 hours ago Total Questions : 99
The Fortinet NSE 7 - SD-WAN 7.2 content is now fully updated, with all current exam questions added 21 hours ago. Deciding to include NSE7_SDW-7.2 practice exam questions in your study plan goes far beyond basic test preparation.
You'll find that our NSE7_SDW-7.2 exam questions frequently feature detailed scenarios and practical problem-solving exercises that directly mirror industry challenges. Engaging with these NSE7_SDW-7.2 sample sets allows you to effectively manage your time and pace yourself, giving you the ability to finish any Fortinet NSE 7 - SD-WAN 7.2 practice test comfortably within the allotted time.
What is the route-tag setting in an SD-WAN rule used for?
Refer to the exhibit.
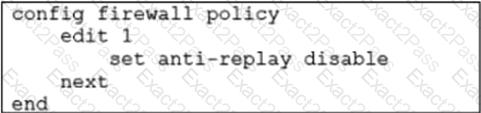
In a dual-hub hub-and-spoke SD-WAN deployment, which is a benefit of disabling theanti-replaysetting on the hubs?
Which diagnostic command can you use to show the configured SD-WAN zones and their assigned members?
Refer to the exhibit.

Which configuration change is required if the responder FortiGate uses a dynamic routing protocol to exchange routes over IPsec?
Refer to the exhibit.
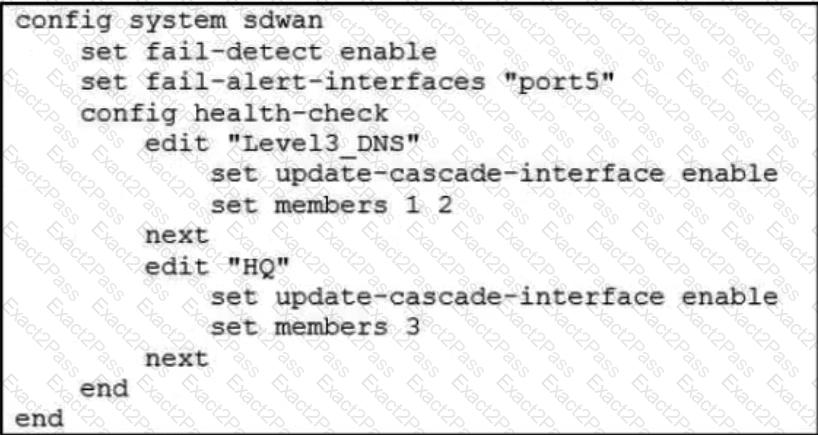
Based on the exhibit, which action does FortiGate take?
Refer to the Exhibits:
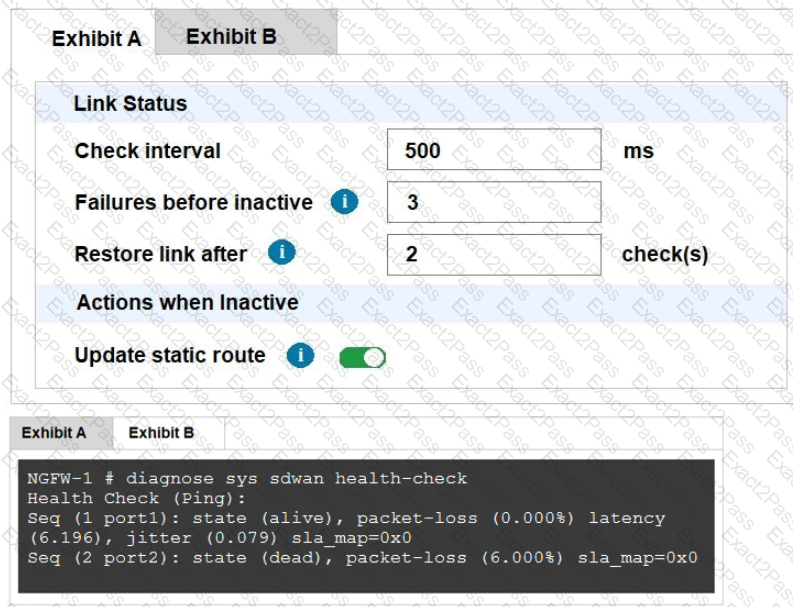
Exhibit A, which shows the SD-WAN performance SLA and exhibit B shows the health of the participating SD-WAN members.
Based on the exhibits, which statement is correct?
Which are two benefits of using CLI templates in FortiManager? (Choose two.)

