Last Update 5 hours ago Total Questions : 238
The Certified Pega Lead System Architect (CPLSA) Exam 8.8 content is now fully updated, with all current exam questions added 5 hours ago. Deciding to include PEGACPLSA88V1 practice exam questions in your study plan goes far beyond basic test preparation.
You'll find that our PEGACPLSA88V1 exam questions frequently feature detailed scenarios and practical problem-solving exercises that directly mirror industry challenges. Engaging with these PEGACPLSA88V1 sample sets allows you to effectively manage your time and pace yourself, giving you the ability to finish any Certified Pega Lead System Architect (CPLSA) Exam 8.8 practice test comfortably within the allotted time.
BigCo receives complaints from existing customers and new prospects that BigCo representatives contact them with irrelevant offers and products.
Which two Pega solutions do you suggest to help solve this problem? (Choose Two)
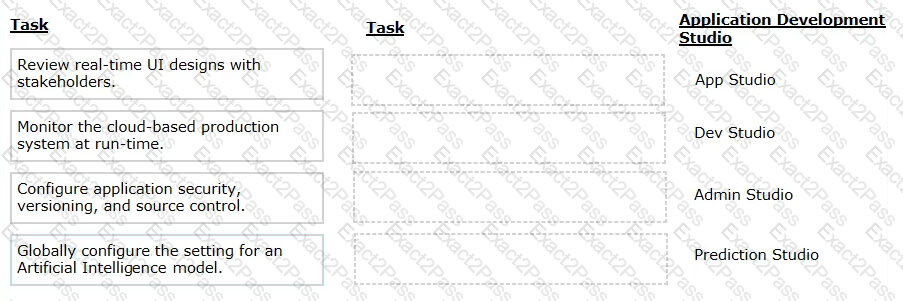
Select each task on the left and drag it to the corresponding Application Development Studio on the right, where the task can be completed.
What is the primary reason for developing a set of unit test cases and automated testing suites in a continuous integration and continuous deployment (CI/CD) model?
your application uses a page type property named customerinfo to store the customer's first and last
names.which two approaches ensure that the customer's first and last names are stored in upper case?(choose two)
you are configuring authentication for a pega web mashup implementation.
how do you ensure the host system origin is trusted?
A shipping case needs to wait for a designated time period before progressing In its flow. The developer considers using either a Wait shape or an assignment with a service-level agreement (SLA) to perform this function.
Identify the use case where an assignment with an SLA is the preferred approach.
The clipboard contains a list of details for all companies on the NASDAQ stock Exchange
select the requirement that indicates you use a page list instead of a page group.

