Last Update 18 hours ago Total Questions : 318
The Google Cloud Certified - Professional Cloud Security Engineer content is now fully updated, with all current exam questions added 18 hours ago. Deciding to include Professional-Cloud-Security-Engineer practice exam questions in your study plan goes far beyond basic test preparation.
You'll find that our Professional-Cloud-Security-Engineer exam questions frequently feature detailed scenarios and practical problem-solving exercises that directly mirror industry challenges. Engaging with these Professional-Cloud-Security-Engineer sample sets allows you to effectively manage your time and pace yourself, giving you the ability to finish any Google Cloud Certified - Professional Cloud Security Engineer practice test comfortably within the allotted time.
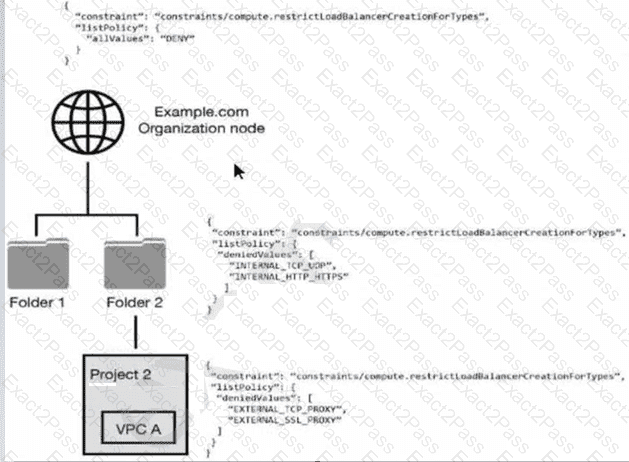
You have the following resource hierarchy. There is an organization policy at each node in the hierarchy as shown. Which load balancer types are denied in VPC A?
You are on your company's development team. You noticed that your web application hosted in staging on GKE dynamically includes user data in web pages without first properly validating the inputted data. This could allow an attacker to execute gibberish commands and display arbitrary content in a victim user's browser in a production environment.
How should you prevent and fix this vulnerability?
You need to use Cloud External Key Manager to create an encryption key to encrypt specific BigQuery data at rest in Google Cloud. Which steps should you do first?
Your organization needs to restrict the types of Google Cloud services that can be deployed within specific folders to enforce compliance requirements. You must apply these restrictions only to the designated folders without affecting other parts of the resource hierarchy. You want to use the most efficient and simple method. What should you do?
An organization is starting to move its infrastructure from its on-premises environment to Google Cloud Platform (GCP). The first step the organization wants to take is to migrate its current data backup and disaster recovery solutions to GCP for later analysis. The organization’s production environment will remain on- premises for an indefinite time. The organization wants a scalable and cost-efficient solution.
Which GCP solution should the organization use?
You are setting up Cloud Identity for your company's Google Cloud organization. User accounts will be provisioned from Microsoft Entra ID through Directory Sync and there will be a single sign-on through Entra ID. You need to secure the super administrator accounts for the organization. Your solution must follow the principle of least privilege and implement strong authentication. What should you do?
You are part of a security team investigating a compromised service account key. You need to audit which new resources were created by the service account.
What should you do?

