Last Update 1 hour ago Total Questions : 393
The Implementing Cisco Enterprise Network Core Technologies (350-401 ENCOR) content is now fully updated, with all current exam questions added 1 hour ago. Deciding to include 350-401 practice exam questions in your study plan goes far beyond basic test preparation.
You'll find that our 350-401 exam questions frequently feature detailed scenarios and practical problem-solving exercises that directly mirror industry challenges. Engaging with these 350-401 sample sets allows you to effectively manage your time and pace yourself, giving you the ability to finish any Implementing Cisco Enterprise Network Core Technologies (350-401 ENCOR) practice test comfortably within the allotted time.
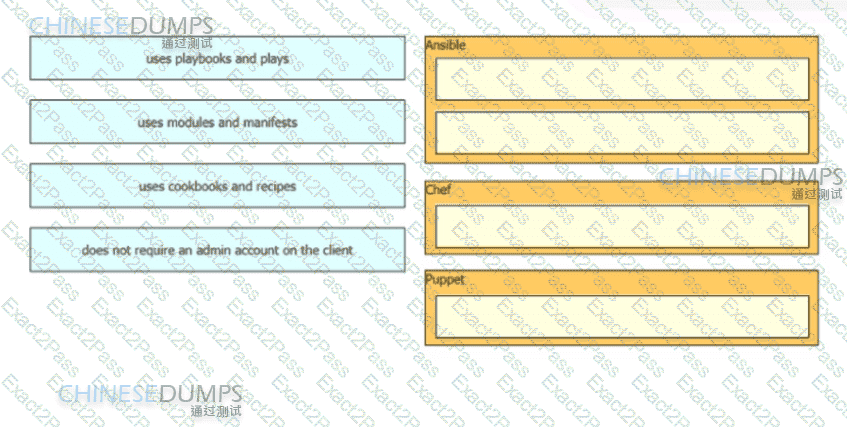
Drag and drop the automation characteristics from the left to the corresponding tools on the right.
Which two pieces of information are necessary to compute SNR? (Choose two.)
What is the name of the numerical relationship of the wireless signal compared to the noise floor?
An engineer must construct an access list for a Cisco Catalyst 9800 Series WLC that will redirect wireless guest users to a splash page that is hosted on a Cisco ISE server. The Cisco ISE servers are hosted at 10.9.11.141 and 10.1.11.141. Which access list meets the requirements?
Which type of roaming event occurs when a client roams across multiple mobility groups?

Refer to the exhibit. Which HTTP request produced the REST API response that was returned by the Cisco Catalyst Center (formerly DNA Center) platform?
What is the data policy in a Cisco SD-WAN deployment?

