Last Update 23 hours ago Total Questions : 411
The Check Point Certified Security Administrator R81.20 CCSA (156-215.81.20) content is now fully updated, with all current exam questions added 23 hours ago. Deciding to include 156-215.81 practice exam questions in your study plan goes far beyond basic test preparation.
You'll find that our 156-215.81 exam questions frequently feature detailed scenarios and practical problem-solving exercises that directly mirror industry challenges. Engaging with these 156-215.81 sample sets allows you to effectively manage your time and pace yourself, giving you the ability to finish any Check Point Certified Security Administrator R81.20 CCSA (156-215.81.20) practice test comfortably within the allotted time.
You can see the following graphic:
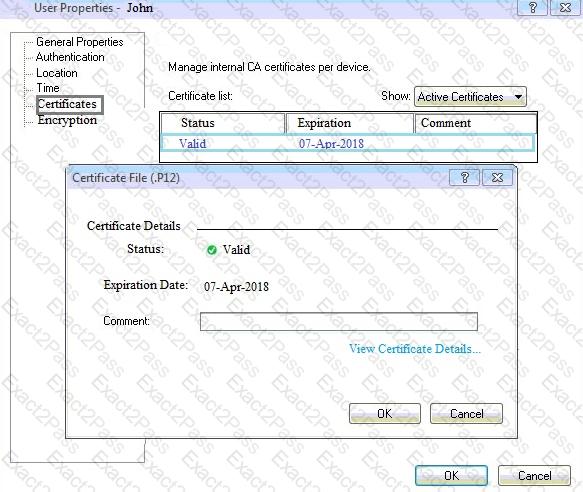
What is presented on it?
Check Point licenses come in two forms. What are those forms?
Which of the following is NOT a role of the SmartCenter:
Which application is used for the central management and deployment of licenses and packages?
Of all the Check Point components in your network, which one changes most often and should be backed up most frequently?
When an Admin logs into SmartConsole and sees a lock icon on a gateway object and cannot edit that object, what does that indicate?
At what point is the Internal Certificate Authority (ICA) created?

