Last Update 22 hours ago Total Questions : 40
The Nokia IP Networksand Services Fundamentals content is now fully updated, with all current exam questions added 22 hours ago. Deciding to include 4A0-100 practice exam questions in your study plan goes far beyond basic test preparation.
You'll find that our 4A0-100 exam questions frequently feature detailed scenarios and practical problem-solving exercises that directly mirror industry challenges. Engaging with these 4A0-100 sample sets allows you to effectively manage your time and pace yourself, giving you the ability to finish any Nokia IP Networksand Services Fundamentals practice test comfortably within the allotted time.
Which of the following is required if devices on different VLANs wish to communicate with each other?
Which of the following statements about a physical router interface is FALSE?
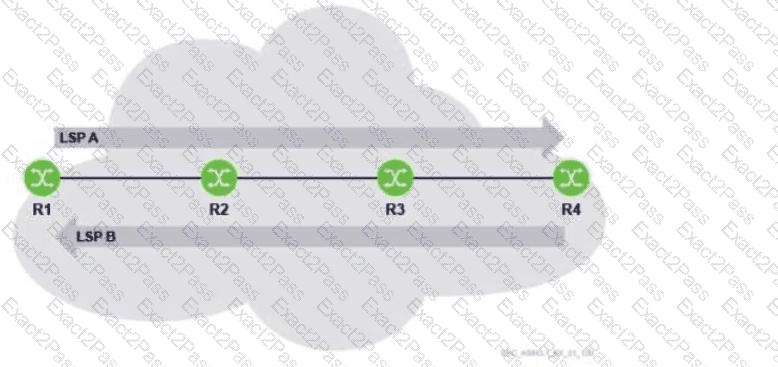
Which of the MPLS routers is responsible for pushing new labels for LSP A and LSP B?
Which tier of Internet service providers provides transit services to other ISPs?
In which of the following types of network would STP be used?
Which of the following is a characteristic of a subnet created with a /31 prefix?
Which of the following statements best describes BGP route selection?

