Last Update 5 hours ago Total Questions : 60
The Aruba Certified Network Security Expert Written Exam content is now fully updated, with all current exam questions added 5 hours ago. Deciding to include HPE6-A84 practice exam questions in your study plan goes far beyond basic test preparation.
You'll find that our HPE6-A84 exam questions frequently feature detailed scenarios and practical problem-solving exercises that directly mirror industry challenges. Engaging with these HPE6-A84 sample sets allows you to effectively manage your time and pace yourself, giving you the ability to finish any Aruba Certified Network Security Expert Written Exam practice test comfortably within the allotted time.
Refer to the exhibit.
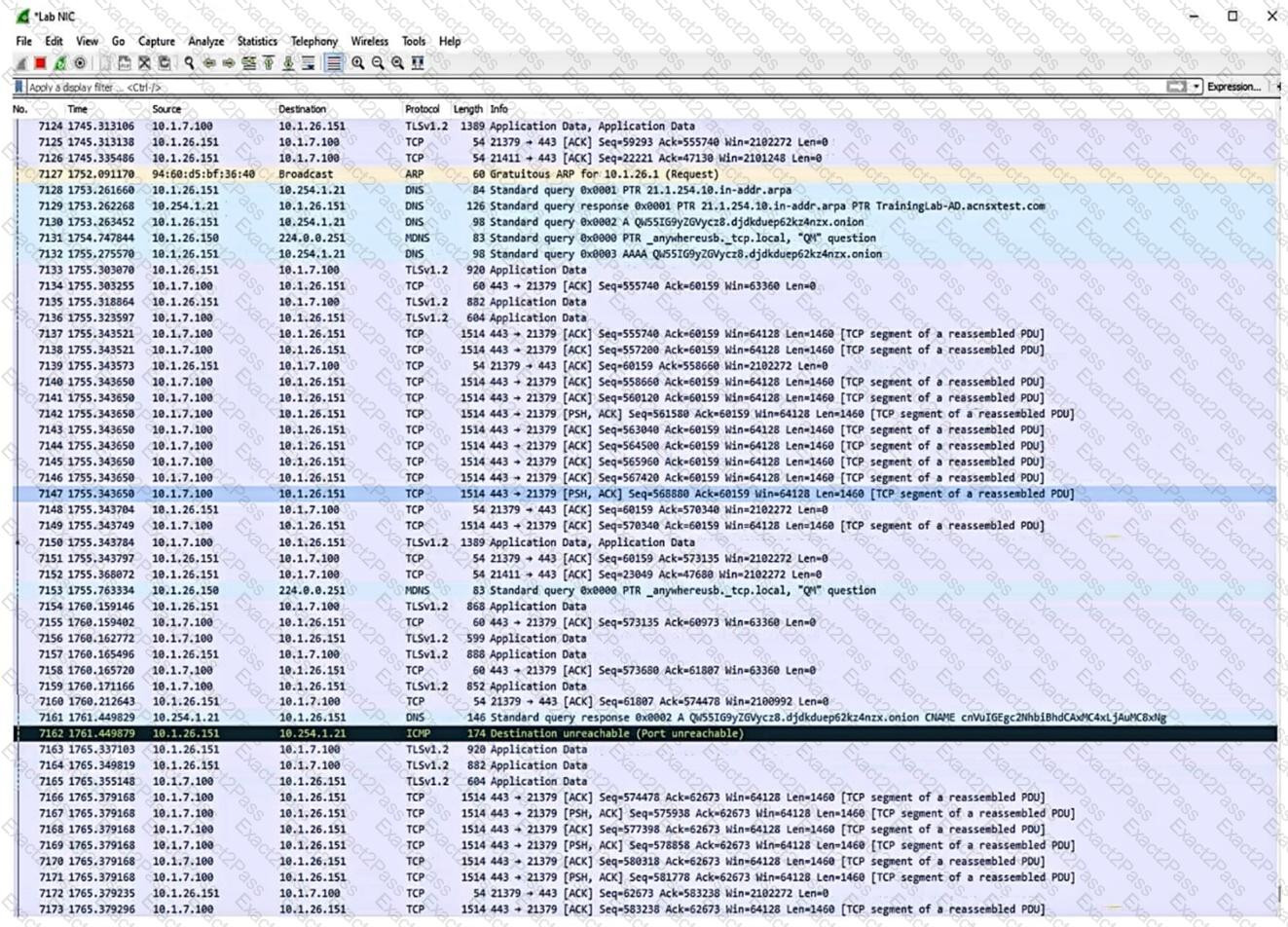
Which security issue is possibly indicated by this traffic capture?
What is a common characteristic of a beacon between a compromised device and a command and control server?
Refer to the scenario.
An organization wants the AOS-CX switch to trigger an alert if its RADIUS server (cp.acnsxtest.local) rejects an unusual number of client authentication requests per hour. After some discussions with other Aruba admins, you are still not sure how many rejections are usual or unusual. You expect that the value could be different on each switch.
You are helping the developer understand how to develop an NAE script for this use case.
You are helping the developer find the right URI for the monitor.
Refer to the exhibit.
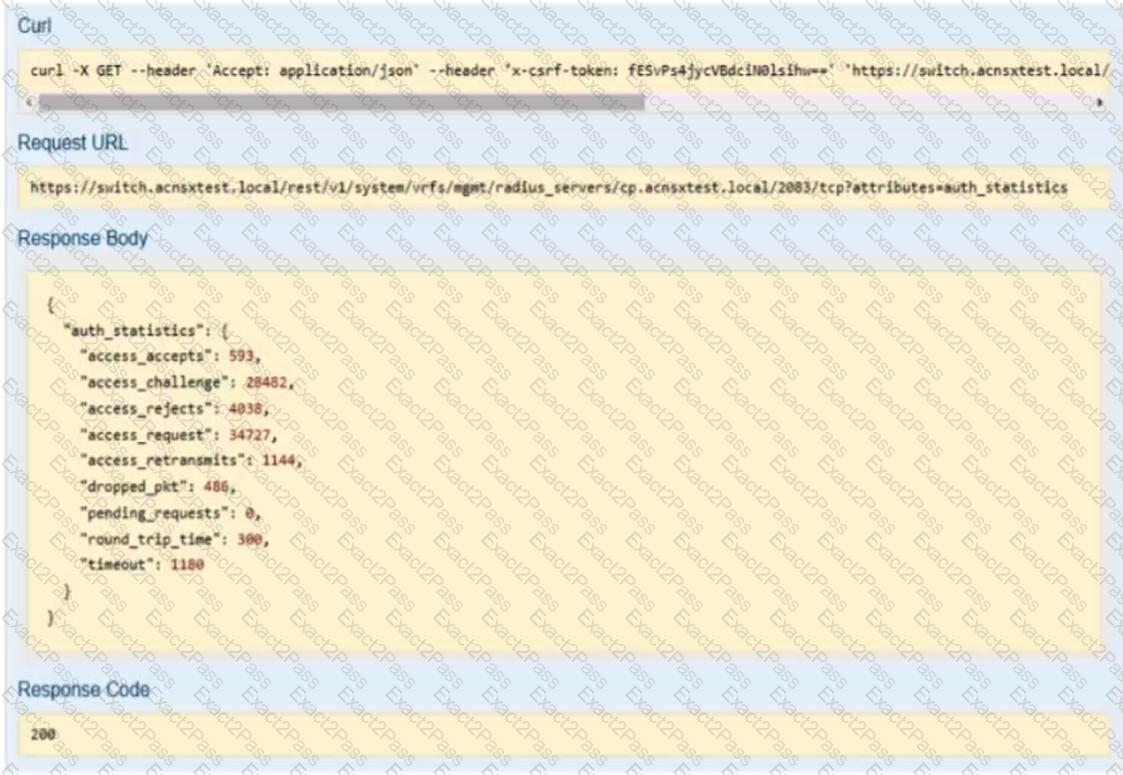
You have used the REST API reference interface to submit a test call. The results are shown in the exhibit.
Which URI should you give to the developer?
Refer to the scenario.
A customer requires these rights for clients in the “medical-mobile” AOS firewall role on Aruba Mobility Controllers (MCs):
 Permitted to receive IP addresses with DHCP
Permitted to receive IP addresses with DHCP
 Permitted access to DNS services from 10.8.9.7 and no other server
Permitted access to DNS services from 10.8.9.7 and no other server
 Permitted access to all subnets in the 10.1.0.0/16 range except denied access to 10.1.12.0/22
Permitted access to all subnets in the 10.1.0.0/16 range except denied access to 10.1.12.0/22
 Denied access to other 10.0.0.0/8 subnets
Denied access to other 10.0.0.0/8 subnets
 Permitted access to the Internet
Permitted access to the Internet
 Denied access to the WLAN for a period of time if they send any SSH traffic
Denied access to the WLAN for a period of time if they send any SSH traffic
 Denied access to the WLAN for a period of time if they send any Telnet traffic
Denied access to the WLAN for a period of time if they send any Telnet traffic
 Denied access to all high-risk websites
Denied access to all high-risk websites
External devices should not be permitted to initiate sessions with “medical-mobile” clients, only send return traffic.
The exhibits below show the configuration for the role.
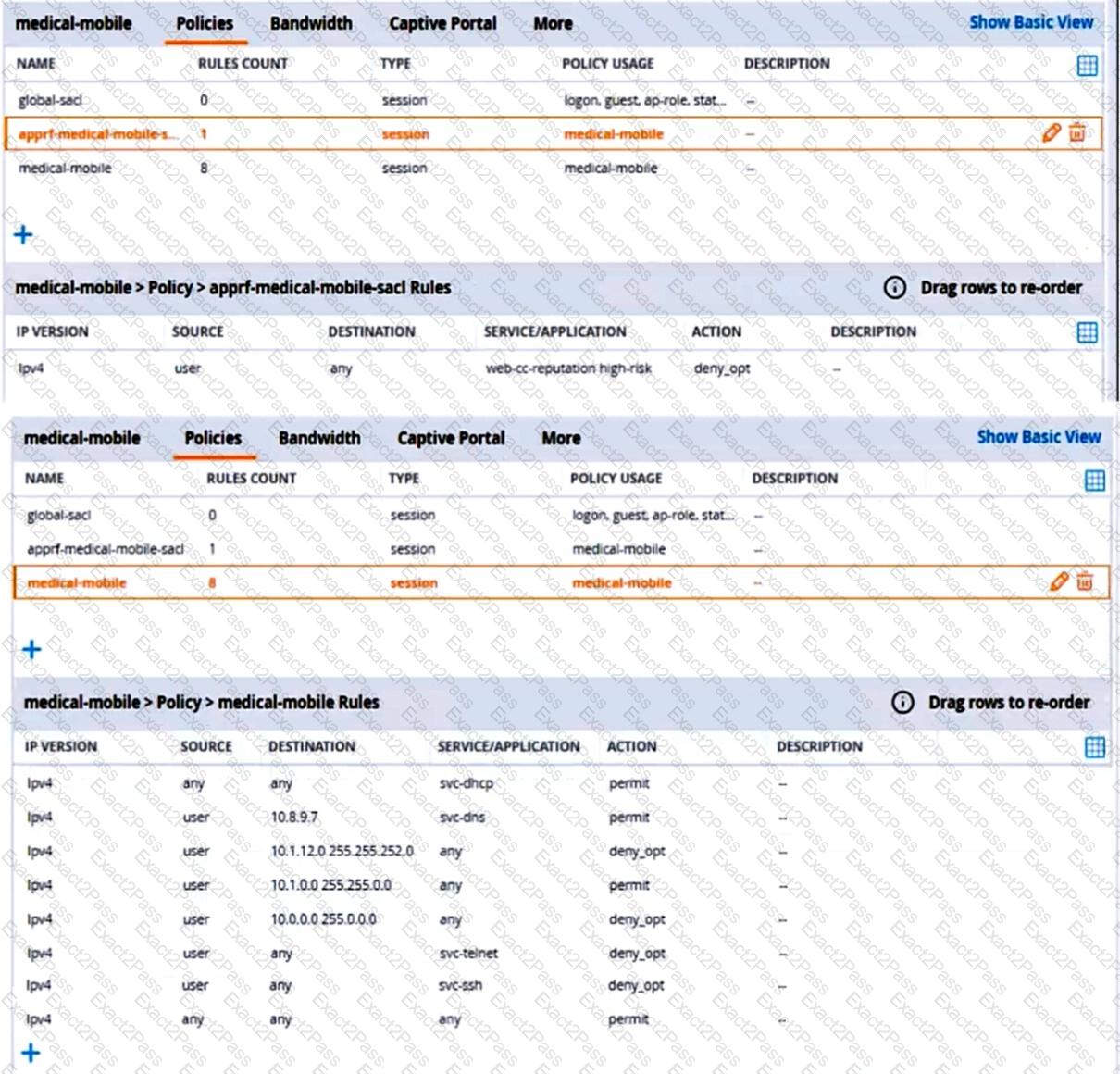
There are multiple issues with the configuration.
What is one of the changes that you must make to the policies to meet the scenario requirements? (In the options, rules in a policy are referenced from top to bottom. For example, “medical-mobile” rule 1 is “ipv4 any any svc-dhcp permit,” and rule 8 is “ipv4 any any any permit’.)
A company has Aruba gateways that are Implementing gateway IDS/IPS in IDS mode. The customer complains that admins are receiving too frequent of repeat email notifications for the same threat. The threat itself might be one that the admins should investigate, but the customer does not want the email notification to repeat as often.
Which setting should you adjust in Aruba Central?
Refer to the scenario.
A customer has an Aruba ClearPass cluster. The customer has AOS-CX switches that implement 802.1X authentication to ClearPass Policy Manager (CPPM).
Switches are using local port-access policies.
The customer wants to start tunneling wired clients that pass user authentication only to an Aruba gateway cluster. The gateway cluster should assign these clients to the “eth-internet" role. The gateway should also handle assigning clients to their VLAN, which is VLAN 20.
The plan for the enforcement policy and profiles is shown below:
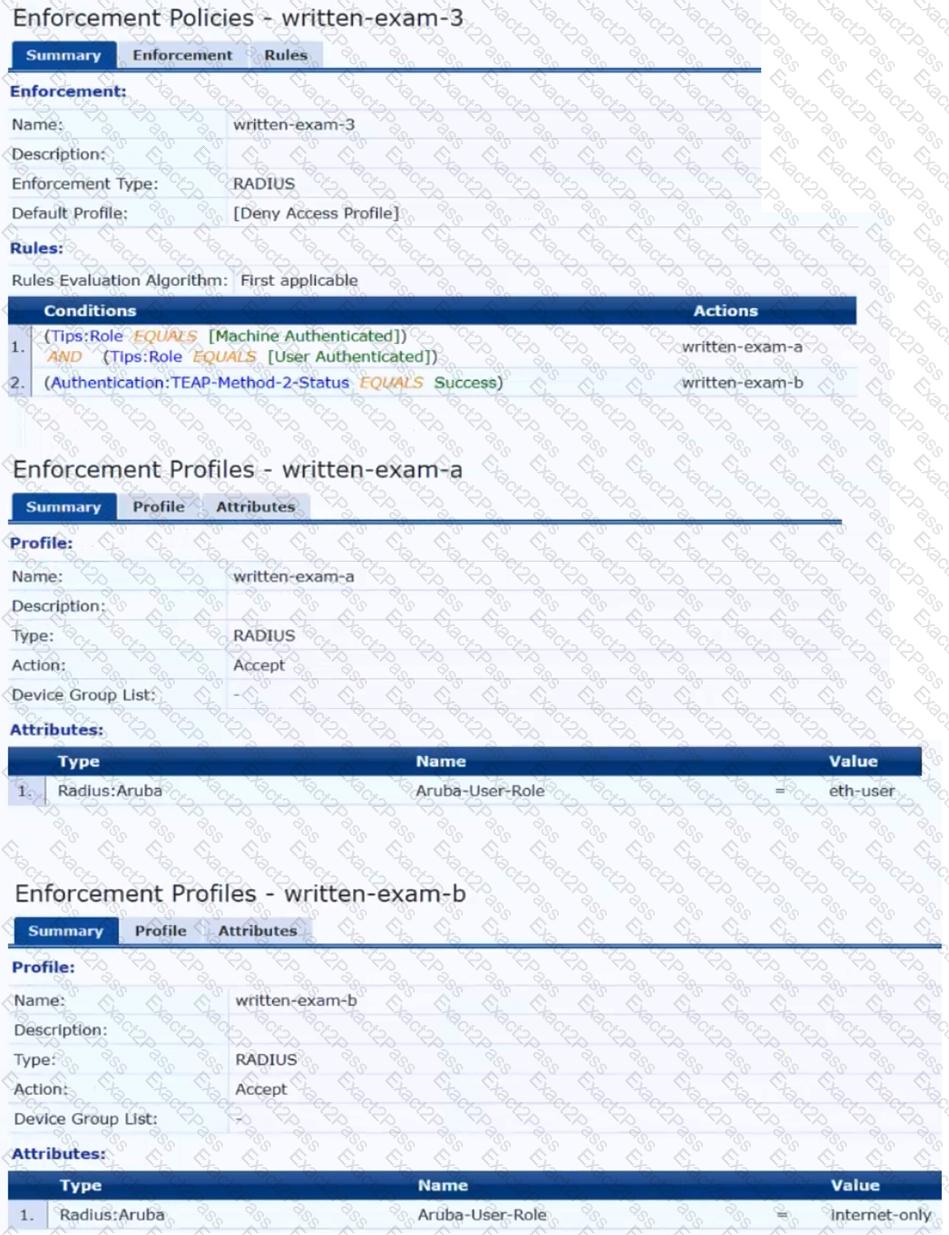
The gateway cluster has two gateways with these IP addresses:
• Gateway 1
o VLAN 4085 (system IP) = 10.20.4.21
o VLAN 20 (users) = 10.20.20.1
o VLAN 4094 (WAN) = 198.51.100.14
• Gateway 2
o VLAN 4085 (system IP) = 10.20.4.22
o VLAN 20 (users) = 10.20.20.2
o VLAN 4094 (WAN) = 198.51.100.12
• VRRP on VLAN 20 = 10.20.20.254
The customer requires high availability for the tunnels between the switches and the gateway cluster. If one gateway falls, the other gateway should take over its tunnels. Also, the switch should be able to discover the gateway cluster regardless of whether one of the gateways is in the cluster.
Assume that you have configured the correct UBT zone and port-access role settings. However, the solution is not working.
What else should you make sure to do?
Refer to the scenario.
A customer requires these rights for clients in the “medical-mobile” AOS firewall role on Aruba Mobility Controllers (MCs):
 Permitted to receive IP addresses with DHCP
Permitted to receive IP addresses with DHCP
 Permitted access to DNS services from 10.8.9.7 and no other server
Permitted access to DNS services from 10.8.9.7 and no other server
 Permitted access to all subnets in the 10.1.0.0/16 range except denied access to 10.1.12.0/22
Permitted access to all subnets in the 10.1.0.0/16 range except denied access to 10.1.12.0/22
 Denied access to other 10.0.0.0/8 subnets
Denied access to other 10.0.0.0/8 subnets
 Permitted access to the Internet
Permitted access to the Internet
 Denied access to the WLAN for a period of time if they send any SSH traffic
Denied access to the WLAN for a period of time if they send any SSH traffic
 Denied access to the WLAN for a period of time if they send any Telnet traffic
Denied access to the WLAN for a period of time if they send any Telnet traffic
 Denied access to all high-risk websites
Denied access to all high-risk websites
External devices should not be permitted to initiate sessions with “medical-mobile” clients, only send return traffic.
The exhibits below show the configuration for the role.
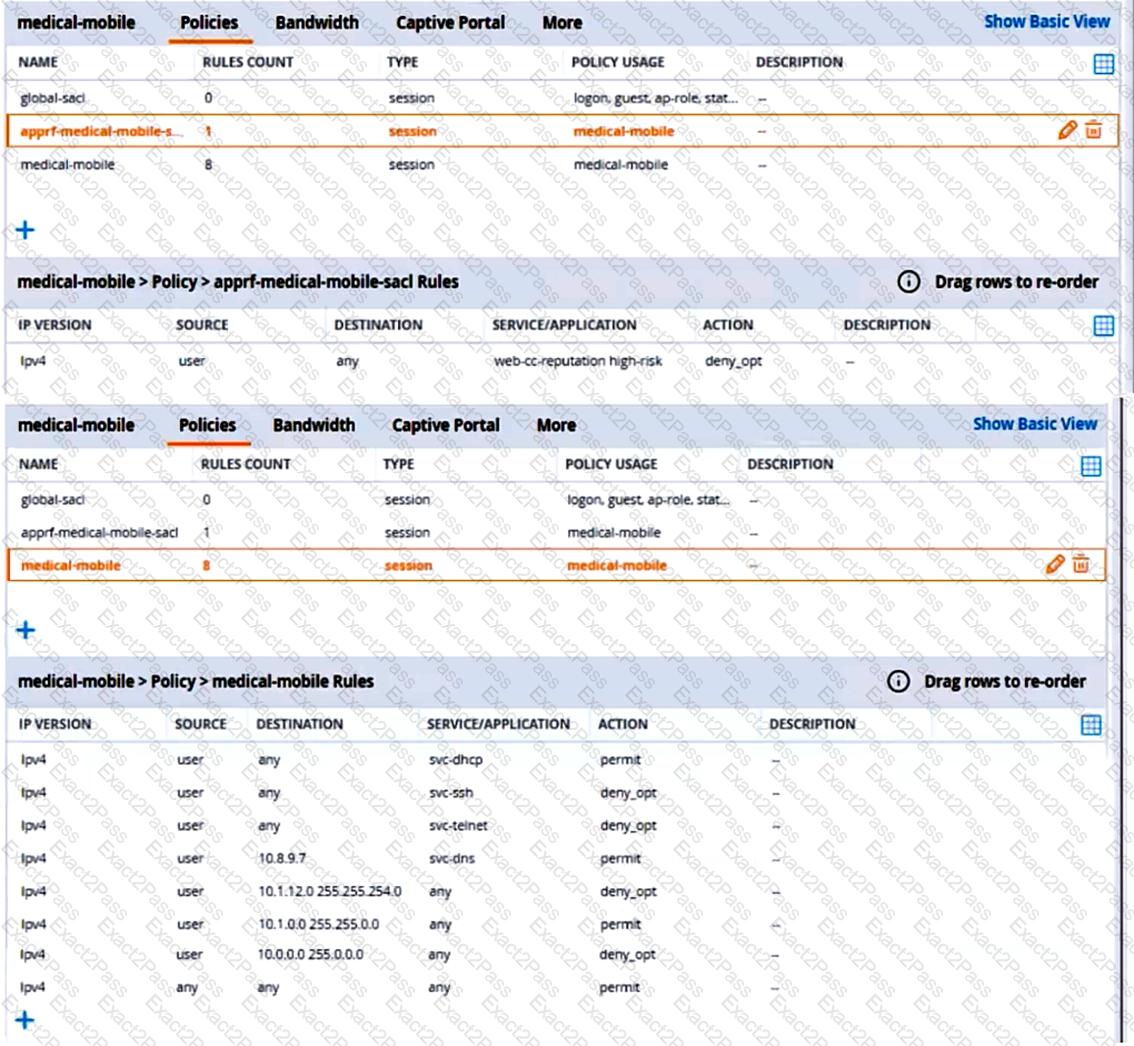
What setting not shown in the exhibit must you check to ensure that the requirements of the scenario are met?

