Last Update 9 hours ago Total Questions : 68
The Netskope Certified Cloud Security Architect Exam content is now fully updated, with all current exam questions added 9 hours ago. Deciding to include NSK300 practice exam questions in your study plan goes far beyond basic test preparation.
You'll find that our NSK300 exam questions frequently feature detailed scenarios and practical problem-solving exercises that directly mirror industry challenges. Engaging with these NSK300 sample sets allows you to effectively manage your time and pace yourself, giving you the ability to finish any Netskope Certified Cloud Security Architect Exam practice test comfortably within the allotted time.
You have multiple networking clients running on an endpoint and client connectivity is a concern. You are configuring co-existence with a VPN solution in this scenario, what is recommended to prevent potential routing issues?
Review the exhibit.
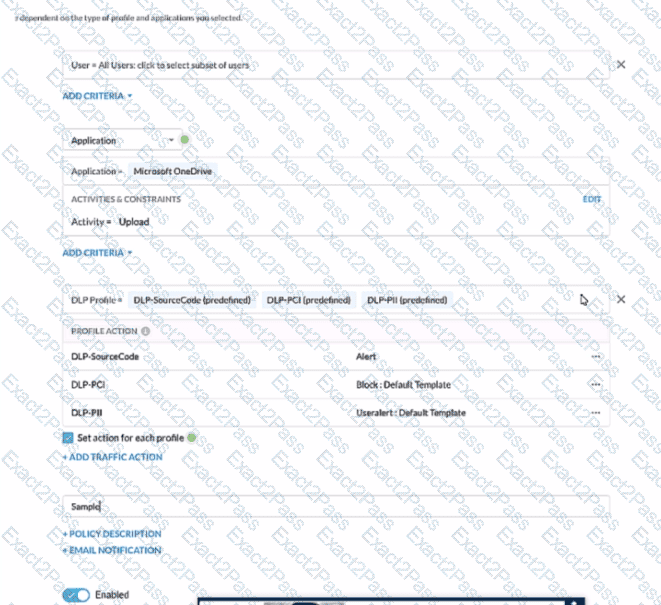
A user has attempted to upload a file to Microsoft OneDrive that contains source code with Pll and PCI data.
Referring to the exhibit, which statement Is correct?
You successfully configured Advanced Analytics to identify policy violation trends Upon further investigation, you notice that the activity is NULL. Why is this happening in this scenario?
Your Netskope Client tunnel has connected to Netskope; however, the user is not receiving any steering or client configuration updates What would cause this issue?
You do not want a scheduled Advanced Analytics dashboard to be automatically updated when Netskope makes improvements to that dashboard. In this scenario, what would you do to retain the original dashboard?
What is a Fast Scan component of Netskope Threat Detection?
Review the exhibit.
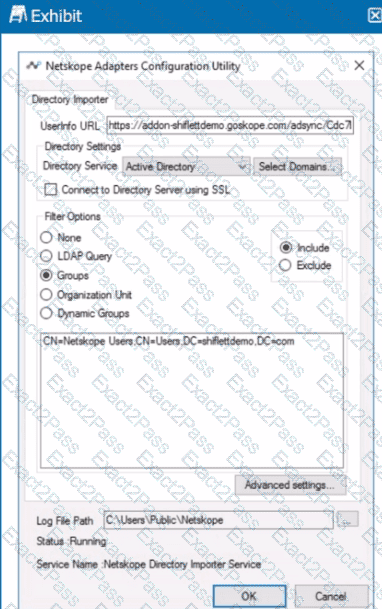
You installed Directory Importer and configured it to import specific groups ot users into your Netskope tenant as shown in the exhibit. One hour after a new user has been added to the domain, the user still has not been provisioned to Netskope.
What are three potential reasons for this failure? (Choose three.)

