Last Update 15 hours ago Total Questions : 125
The Certified Implementation Specialist - Discovery content is now fully updated, with all current exam questions added 15 hours ago. Deciding to include CIS-Discovery practice exam questions in your study plan goes far beyond basic test preparation.
You'll find that our CIS-Discovery exam questions frequently feature detailed scenarios and practical problem-solving exercises that directly mirror industry challenges. Engaging with these CIS-Discovery sample sets allows you to effectively manage your time and pace yourself, giving you the ability to finish any Certified Implementation Specialist - Discovery practice test comfortably within the allotted time.
When is the Extension section in a horizontal pattern executed?
Which choice represents the three best ways of extending Discovery?
In IT environments, what is the purpose of horizontal discovery?
Which of the below choices are needed for Quick Discovery? (Choose two.)
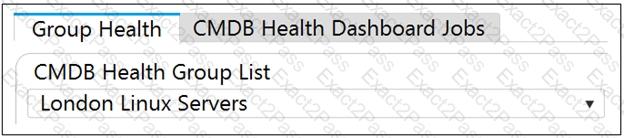
Based on the following image, which of the following choices is also true about London Linux Servers?
Which of the following best describes the relationship between the Tomcat [cmdb_ci_app_server_tomcat] table and the Application Server [cdmb_ci_app_server] table? (Choose two.)
Which of the following does the ECC Queue provide? (Choose two.)

