Last Update 2 hours ago Total Questions : 108
The SailPoint Certified IdentityNow Engineer content is now fully updated, with all current exam questions added 2 hours ago. Deciding to include IdentityNow-Engineer practice exam questions in your study plan goes far beyond basic test preparation.
You'll find that our IdentityNow-Engineer exam questions frequently feature detailed scenarios and practical problem-solving exercises that directly mirror industry challenges. Engaging with these IdentityNow-Engineer sample sets allows you to effectively manage your time and pace yourself, giving you the ability to finish any SailPoint Certified IdentityNow Engineer practice test comfortably within the allotted time.
Review the current identity model and scenario below.
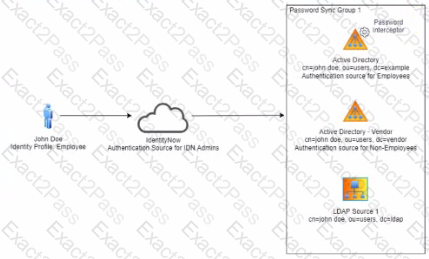
Scenario
John Doe requests "Sales" access on Salesforce for himself. In the approval process, John Doe's manager approves. The access request is tils the expected provisioning action sent to the source connectors?
Solution: Expected Provisioning No provisioning is sent out.
An IdentityNow engineer has the following problem:
IdentityNow shows status failed on a virtual appliance (VA).
Is this one of the steps that should be taken troubleshoot the issue?
Solution: Review the log files in /home/sailpoint/log for errors.
When preparing for a manager certification campaign is this a step that is considered a best practice before the campaign preview is generated?
Solution: Evaluate available campaign administration filters
An IdentityNow engineer needs to find identities with disabled AD accounts by using IdentityNow's search features. Is this the correct search syntax to perform this task?
Solution:
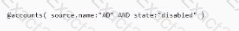
Is the following true about custom connectors in IdentityNow?
Solution: Custom connector configurations can have account correlation settings defined.
Is this an item that an IdentityNow engineer should configure when implementing a source that uses a JDBC connector?
Solution: Use a query select statement with a clause to match the incoming account to an existing account for the Single Account SQL Query configuration item
Is the following true about the web-services connector in IdentityNow?
Solution: The connector supports SAML authentication.

