Last Update 22 hours ago Total Questions : 221
The CyberArk CDE Recertification content is now fully updated, with all current exam questions added 22 hours ago. Deciding to include PAM-CDE-RECERT practice exam questions in your study plan goes far beyond basic test preparation.
You'll find that our PAM-CDE-RECERT exam questions frequently feature detailed scenarios and practical problem-solving exercises that directly mirror industry challenges. Engaging with these PAM-CDE-RECERT sample sets allows you to effectively manage your time and pace yourself, giving you the ability to finish any CyberArk CDE Recertification practice test comfortably within the allotted time.
What is the purpose of a linked account?
Which of these accounts onboarding methods is considered proactive?
Which of the following are secure options for storing the contents of the Operator CD, while still allowing the contents to be accessible upon a planned Vault restart? (Choose three.)
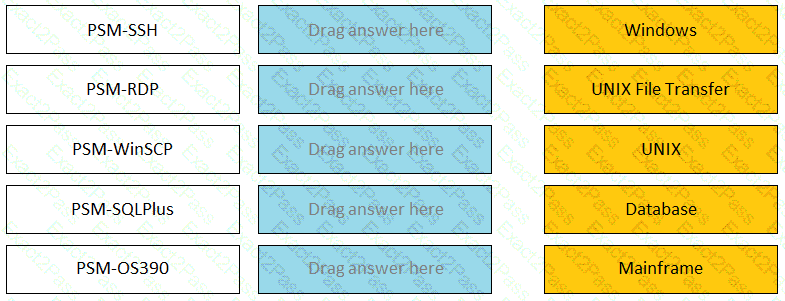
Match the connection component to the corresponding OS/Function.
You are installing PSM for SSH with AD-Bridge in CyberArkSSHD mode for your customer. ACME Corp What do you need to install to meet your customer's needs? (Choose 2)
When a group is granted the 'Authorize Account Requests' permission on a safe Dual Control requests must be approved by
Secure Connect provides the following. Choose all that apply.

