Last Update 7 hours ago Total Questions : 60
The CyberArk Sentry Secrets Manager content is now fully updated, with all current exam questions added 7 hours ago. Deciding to include SECRET-SEN practice exam questions in your study plan goes far beyond basic test preparation.
You'll find that our SECRET-SEN exam questions frequently feature detailed scenarios and practical problem-solving exercises that directly mirror industry challenges. Engaging with these SECRET-SEN sample sets allows you to effectively manage your time and pace yourself, giving you the ability to finish any CyberArk Sentry Secrets Manager practice test comfortably within the allotted time.
While installing the first CP in an environment, errors that occurred when the environment was created are displayed; however, the installation procedure continued and finished successfully.
What should you do?
When an application is retrieving a credential from Conjur, the application authenticates to Follower A. Follower B receives the next request to retrieve the credential.
What happens next?
A customer wants to ensure applications can retrieve secrets from Conjur in three different data centers if the Conjur Leader becomes unavailable. Conjur Followers are already deployed in each of these data centers.
How should you architect the solution to support this requirement?
In a 3-node auto-failover cluster, the Leader has been brought down for patching that lasts longer than the configured TTL. A Standby has been promoted.
Which steps are required to repair the cluster when the old Leader is brought back online?
A customer requires high availability in its AWS cloud infrastructure.
What is the minimally viable Conjur deployment architecture to achieve this?
When attempting to retrieve a credential, you receive an error 401 – Malformed Authorization Token.
What is the cause of the issue?
You are diagnosing this log entry:
From Conjur logs:
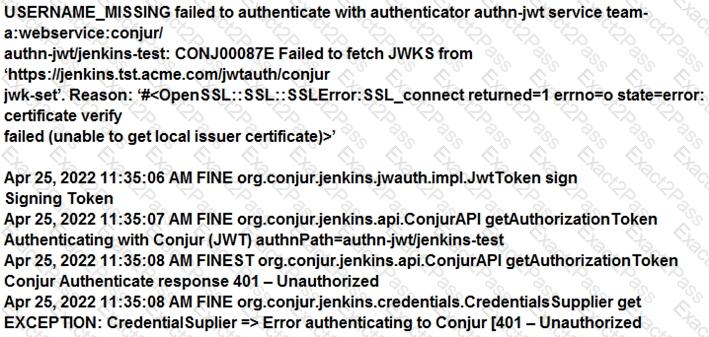
Given these errors, which problem is causing the breakdown?

