Last Update 8 hours ago Total Questions : 64
The CyberArk Defender Access (ACC-DEF) content is now fully updated, with all current exam questions added 8 hours ago. Deciding to include ACCESS-DEF practice exam questions in your study plan goes far beyond basic test preparation.
You'll find that our ACCESS-DEF exam questions frequently feature detailed scenarios and practical problem-solving exercises that directly mirror industry challenges. Engaging with these ACCESS-DEF sample sets allows you to effectively manage your time and pace yourself, giving you the ability to finish any CyberArk Defender Access (ACC-DEF) practice test comfortably within the allotted time.
On which operating systems can the CyberArk Authenticator desktop application be installed? (Choose two.)
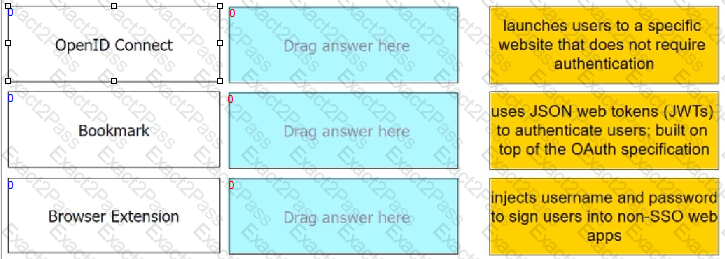
Match each Web App Connector to the phrase that best describes its service offering.
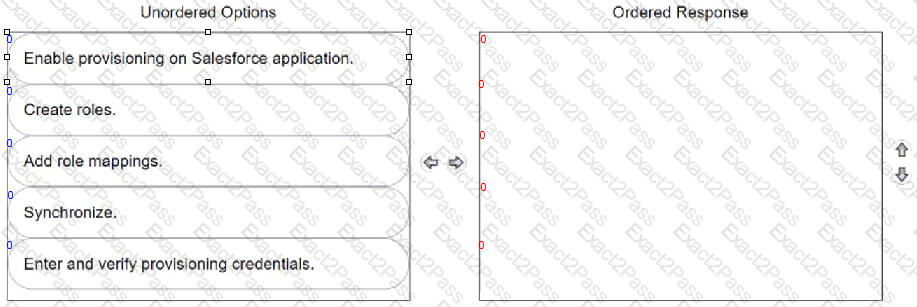
Your organization wants to automatically create user accounts with different Salesforce licenses (e.g., Salesforce, Identity, Chatter External).
In CyberArk Identity, arrange the steps to achieve this in the correct sequence.
What is the purpose of the Infinite Apps feature offered by CyberArk Identity?
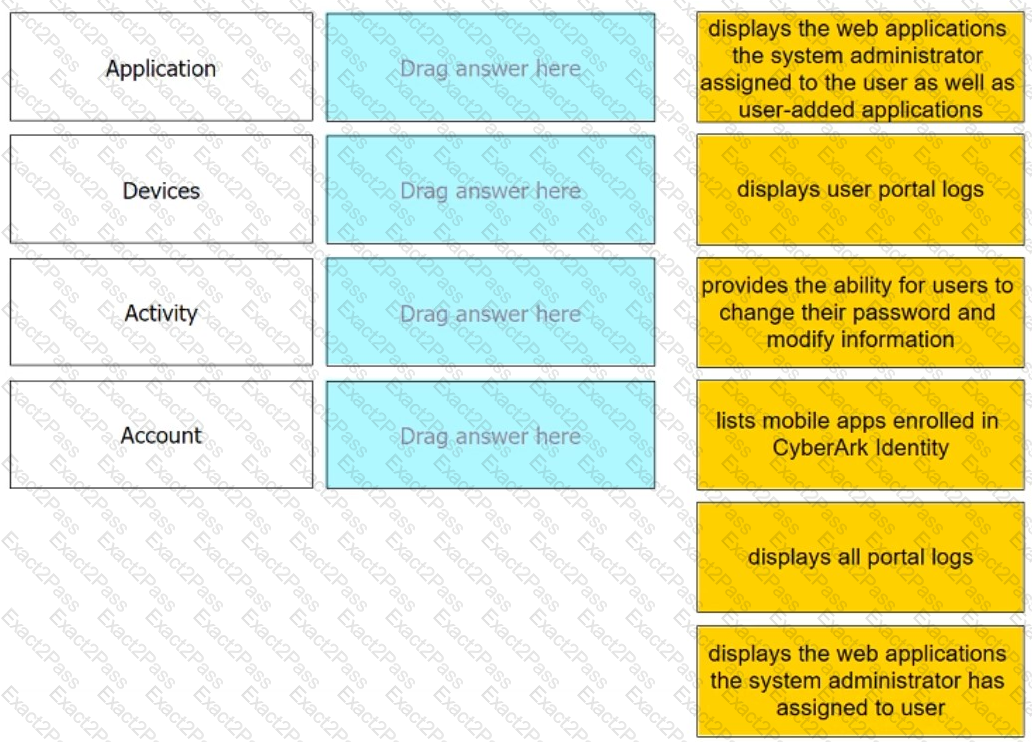
Match each User Portal tab to the correct description.
You want to find all events related to the user with the login ID of "ivan.helen@acme".
Which filter do you enter into the UBA portal data explorer?
What does the CyberArk Identity App Gateway work with? (Choose three.)

