Last Update 2 hours ago Total Questions : 152
The Architecting a Citrix Networking Solution content is now fully updated, with all current exam questions added 2 hours ago. Deciding to include 1Y0-440 practice exam questions in your study plan goes far beyond basic test preparation.
You'll find that our 1Y0-440 exam questions frequently feature detailed scenarios and practical problem-solving exercises that directly mirror industry challenges. Engaging with these 1Y0-440 sample sets allows you to effectively manage your time and pace yourself, giving you the ability to finish any Architecting a Citrix Networking Solution practice test comfortably within the allotted time.
Scenario: A Citrix Architect has set up NetScaler MPX devices in high availability mode with version 12.0. 53.13 nc. These are placed behind a Cisco ASA 5505 Firewall is configured to block traffic using access control lists. The network address translation (NAT) is also performed on the firewall.
The following requirements were captured by the architect during the discussion held as part of the NetScaler security implementation project with the customer’s security team:
The NetScaler device:
Which two security features should the architect configure to meet these requirements? (Choose two.)
Which three parameters must a Citrix Architect designate when creating a new session policy? (Choose three.)
Scenario: A Citrix Architect has configured two MPX devices in high availability mode with version 12.0.53.13 nc. After a discussion with the security team, the architect enabled the Application Firewall feature for additional protection.
In the initial deployment phase, the following security features were enabled:
After deployment in pre-production, the team identifies the following additional security features and changes as further requirements:
Click the Exhibit button to view an excerpt of the existing configuration.
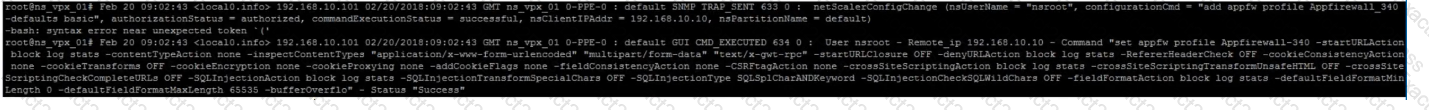
What should the architect do to meet these requirements?
Scenario: A Citrix Architect needs to design a NetScaler deployment in Microsoft Azure. An Active-Passive NetScaler VPX pair will provide load balancing for three distinct web applications. The architect has identified the following requirements:
For this deployment, the architect should configure each NetScaler VPX machine to have ______ network interface(s) and configure IP address by using ________. (Choose the correct option to complete the sentence).
Scenario: A Citrix Architect has deployed an authentication setup with a ShareFile load-balancing virtual server. The NetScaler is configured as the Service Provider and Portalguard server is utilized as the SAML Identity Provider. While performing the functional testing, the architect finds that after the users enter their credentials on the logon page provided by Portalguard, they get redirected back to the Netscaler Gateway page at uri /cgi/samlauth/ and receive the following error.

The events in the /var/log/ns.log at the time of this issue are as follows:
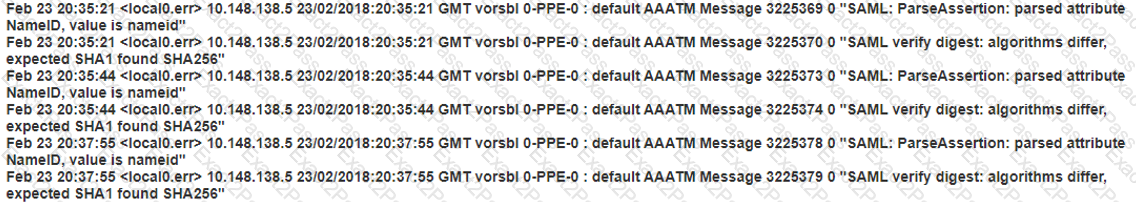
What should the architect change in the SAML action to resolve this issue?
Scenario: Based on a discussion between a Citrix Architect and a team of Workspacelab members, the MPX Logical layout for Workspacelab has been created across three (3) sites.
They captured the following requirements during the design discussion held for a Citrix ADC design project:
Which design decision must the architect make the design requirements above?
Scenario: A Citrix Architect needs to deploy SAML integration between NetScaler (Identity Provider) and ShareFile (Service Provider). The design requirements for SAML setup are as follows:
The verification environment details are as follows:
Which SAML IDP action will meet the design requirements?

