Last Update 22 hours ago Total Questions : 147
The Securing Email with Cisco Email Security Appliance (300-720 SESA) content is now fully updated, with all current exam questions added 22 hours ago. Deciding to include 300-720 practice exam questions in your study plan goes far beyond basic test preparation.
You'll find that our 300-720 exam questions frequently feature detailed scenarios and practical problem-solving exercises that directly mirror industry challenges. Engaging with these 300-720 sample sets allows you to effectively manage your time and pace yourself, giving you the ability to finish any Securing Email with Cisco Email Security Appliance (300-720 SESA) practice test comfortably within the allotted time.
What are two primary components of content filters? (Choose two.)
Which two features are applied to either incoming or outgoing mail policies? (Choose two.)
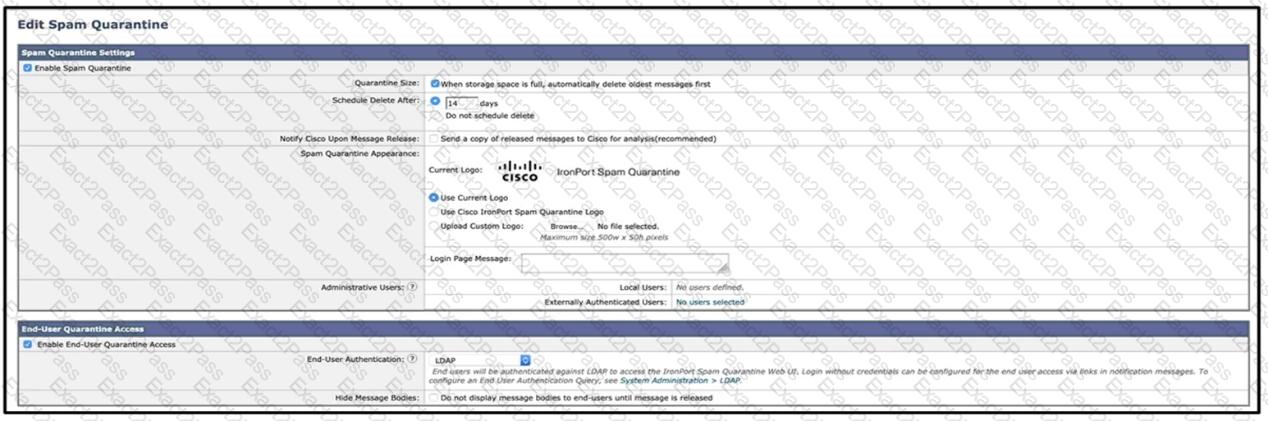

Refer to the exhibits. What must be done to enforce end user authentication before accessing quarantine?
Spammers routinely try to send emails with the recipient field filled with a list of all possible combinations of letters and numbers. These combinations, appended with a company domain name are malicious attempts at learning all possible valid email addresses. Which action must be taken on a Cisco Secure Email Gateway to prevent this from occurring?
What are organizations trying to address when implementing a SPAM quarantine?
Which two certificate authority lists are available in Cisco ESA? (Choose two.)
Which feature must be activated on a Cisco Secure Email Gateway to combat backscatter?

