Last Update 17 hours ago Total Questions : 50
The Cisco Certified Support Technician (CCST) Cybersecurity content is now fully updated, with all current exam questions added 17 hours ago. Deciding to include 100-160 practice exam questions in your study plan goes far beyond basic test preparation.
You'll find that our 100-160 exam questions frequently feature detailed scenarios and practical problem-solving exercises that directly mirror industry challenges. Engaging with these 100-160 sample sets allows you to effectively manage your time and pace yourself, giving you the ability to finish any Cisco Certified Support Technician (CCST) Cybersecurity practice test comfortably within the allotted time.
An administrator wants to ensure that any files downloaded from the internet are automatically scanned for malicious code before execution. Which security control should be implemented?
What is the primary purpose of running a vulnerability scan on your network?
You are planning to work from home. Your company requires that you connect to the company network through a VPN.
Which three critical functions do VPNs provide to remote workers?(Choose 3.)
Which wireless security protocol provides the strongest protection for a home or small business network?
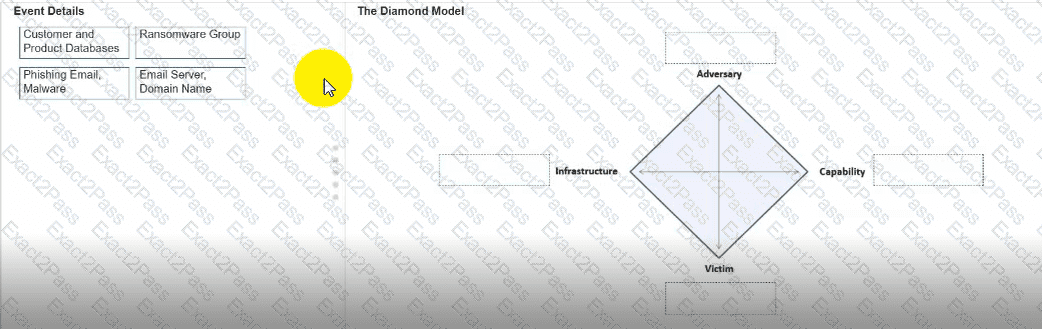
You need to diagram an intrusion event by using the Diamond Model.
Move each event detail from the list on the left to the correct location in the diagram on the right.
Note: You will receive partial credit for each correct response.
An employee accidentally sends an email containing sensitive corporate information to an external email address.
Which type of threat does this scenario describe?
During an incident response, the security team needs to isolate a compromised server from the rest of the network but still allow forensic analysis. Which action should they take?

