Last Update 4 hours ago Total Questions : 54
The FCSS - FortiSASE 24 Administrator content is now fully updated, with all current exam questions added 4 hours ago. Deciding to include FCSS_SASE_AD-24 practice exam questions in your study plan goes far beyond basic test preparation.
You'll find that our FCSS_SASE_AD-24 exam questions frequently feature detailed scenarios and practical problem-solving exercises that directly mirror industry challenges. Engaging with these FCSS_SASE_AD-24 sample sets allows you to effectively manage your time and pace yourself, giving you the ability to finish any FCSS - FortiSASE 24 Administrator practice test comfortably within the allotted time.
Which statement describes the FortiGuard forensics analysis feature on FortiSASE?
When accessing the FortiSASE portal for the first time, an administrator must select data center locations for which three FortiSASE components? (Choose three.)
Refer to the exhibits.
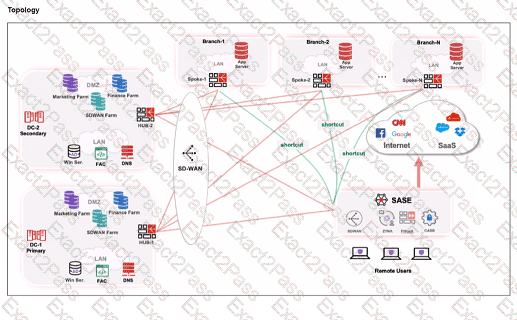
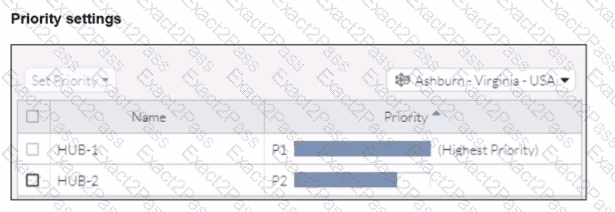
When remote users connected to FortiSASE require access to internal resources on Branch-2. how will traffic be routed?
When viewing the daily summary report generated by FortiSASE. the administrator notices that the report contains very little data. What is a possible explanation for this almost empty report?
Which two additional components does FortiSASE use for application control to act as an inline-CASB? (Choose two.)
Which secure internet access (SIA) use case minimizes individual endpoint configuration?
You are designing a new network for Company X and one of the new cybersecurity policy requirements is that all remote user endpoints must always be connected and protected Which FortiSASE component facilitates this always-on security measure?

