Last Update 4 hours ago Total Questions : 69
The Fortinet NSE 7 - OT Security 7.2 content is now fully updated, with all current exam questions added 4 hours ago. Deciding to include NSE7_OTS-7.2 practice exam questions in your study plan goes far beyond basic test preparation.
You'll find that our NSE7_OTS-7.2 exam questions frequently feature detailed scenarios and practical problem-solving exercises that directly mirror industry challenges. Engaging with these NSE7_OTS-7.2 sample sets allows you to effectively manage your time and pace yourself, giving you the ability to finish any Fortinet NSE 7 - OT Security 7.2 practice test comfortably within the allotted time.
Operational technology (OT) network analysts run different levels of reports to identify failures that could put the network at risk Some of these reports may be related to device performance
Which FortiSIEM reporting method helps identify device failures?
An OT network consists of multiple FortiGate devices. The edge FortiGate device is deployed as the secure gateway and is only allowing remote operators to access the ICS networks on site.
Management hires a third-party company to conduct health and safety on site. The third-party company must have outbound access to external resources.
As the OT network administrator, what is the best scenario to provide external access to the third-party company while continuing to secure the ICS networks?
To increase security protection in an OT network, how does application control on ForliGate detect industrial traffic?
Refer to the exhibit.
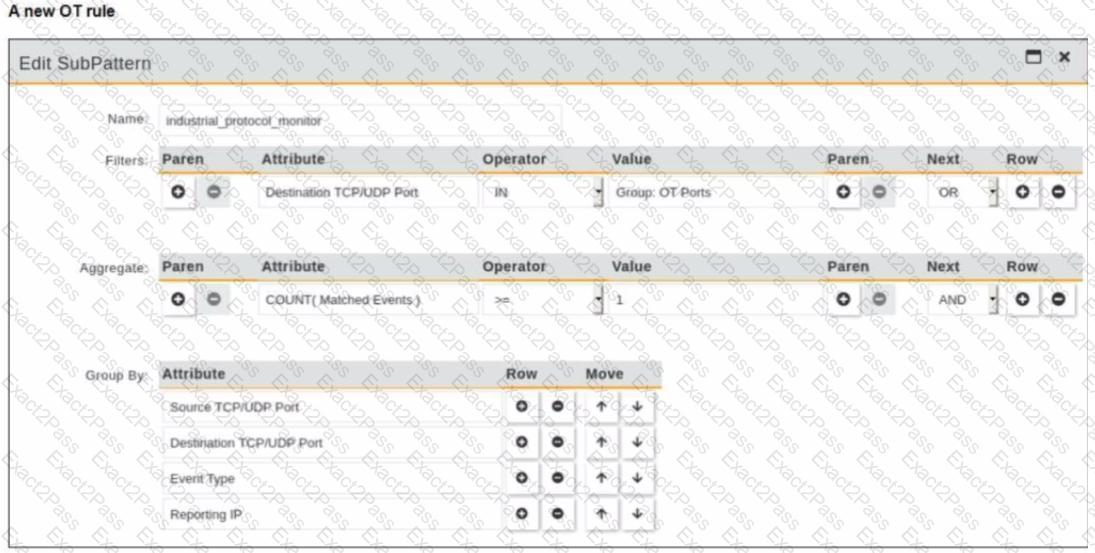
You are creating a new operational technology (OT) rule to monitor Modbus protocol traffic on FortiSIEM
Which action must you take to ensure that all Modbus messages on the network match the rule?
Refer to the exhibit.
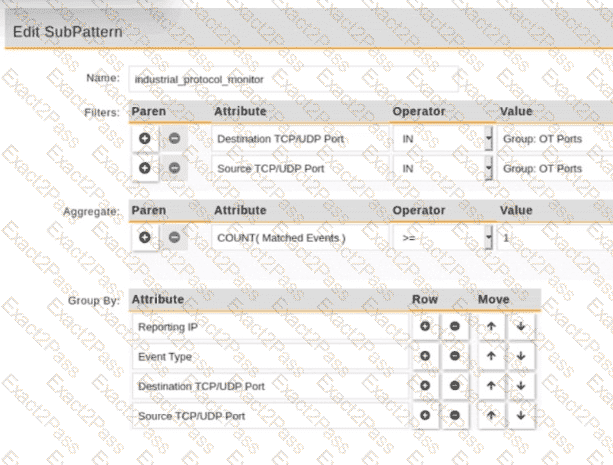
An operational technology rule is created and successfully activated to monitor the Modbus protocol on FortiSIEM. However, the rule does not trigger incidents despite Modbus traffic and application logs being received correctly by FortiSIEM.
Which statement correctly describes the issue on the rule configuration?
When you create a user or host profile, which three criteria can you use? (Choose three.)
Which statement about the IEC 104 protocol is true?

