Last Update 22 hours ago Total Questions : 67
The FortiGate 7.6 Administrator FCP_FGT_AD-7.6 content is now fully updated, with all current exam questions added 22 hours ago. Deciding to include FCP_FGT_AD-7.6 practice exam questions in your study plan goes far beyond basic test preparation.
You'll find that our FCP_FGT_AD-7.6 exam questions frequently feature detailed scenarios and practical problem-solving exercises that directly mirror industry challenges. Engaging with these FCP_FGT_AD-7.6 sample sets allows you to effectively manage your time and pace yourself, giving you the ability to finish any FortiGate 7.6 Administrator FCP_FGT_AD-7.6 practice test comfortably within the allotted time.
What is the primary FortiGate election process when the HA override setting is enabled?
Which two statements are true about an HA cluster? (Choose two.)
You are analyzing connectivity problems caused by intermediate devices blocking traffic in SSL VPN environment.
In which two ways can you effectively resolve the problem? (Choose two.)
Which three statements about SD-WAN performance SLAs are true? (Choose three.)
You have configured the below commands on a FortiGate.
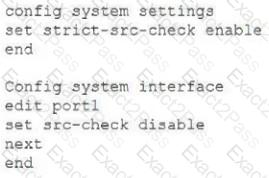
What would be the impact of this configuration on FortiGate?
An administrator suspects that the Collector Agent is not forwarding login events to FortiGate.
What is the most effective troubleshooting step?
Refer to the exhibit.
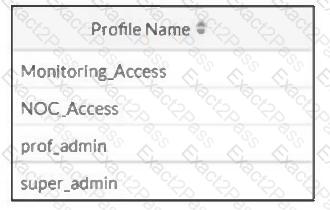
The NOC team connects to the FortiGate GUI with the NOC_Access admin profile. They request that their GUI sessions do not disconnect too early during inactivity.
What must the administrator configure to answer this specific request from the NOC team?

