Last Update 5 hours ago Total Questions : 60
The Conducting Threat Hunting and Defending using Cisco Technologies for Cybersecurity 300-220 CBRTHD content is now fully updated, with all current exam questions added 5 hours ago. Deciding to include 300-220 practice exam questions in your study plan goes far beyond basic test preparation.
You'll find that our 300-220 exam questions frequently feature detailed scenarios and practical problem-solving exercises that directly mirror industry challenges. Engaging with these 300-220 sample sets allows you to effectively manage your time and pace yourself, giving you the ability to finish any Conducting Threat Hunting and Defending using Cisco Technologies for Cybersecurity 300-220 CBRTHD practice test comfortably within the allotted time.
During multiple intrusions, analysts observe that attackers consistently perform internal reconnaissance before privilege escalation, avoid noisy exploitation, and limit actions to business hours of the victim’s region. Why is this observation important for attribution?
A threat hunter is performing a structured hunt usingCisco Secure Endpoint (AMP)telemetry to identify credential harvesting activity. Which data source is MOST critical during thedata collection and processing phaseof the hunt?
A structured threat hunt using Cisco Secure Network Analytics confirms abnormal internal SMB traffic consistent with lateral movement. Which action should occur NEXT to improve organizational security posture?
A threat hunter is usingCisco Secure Network Analytics (Stealthwatch)to investigate possible lateral movement inside the network. Which behavior would MOST strongly indicate lateral movement using valid credentials?
Refer to the exhibit.

A company went through several rounds of restructuring and the previous security team has been let go A new engineer joins and rediscovers all the tools thatthe previous team left behind.One of the tools Is a Bash script related to monitoring AWS accounts for threats What is the purpose of the script?
A security architect is designing a threat model for a multi-tier cloud application that includes public APIs, backend microservices, and an identity provider. The goal is to identify how an attacker could chain multiple weaknesses together to achieve account takeover and data exfiltration. Which threat modeling technique is MOST appropriate?
Refer to the exhibit.
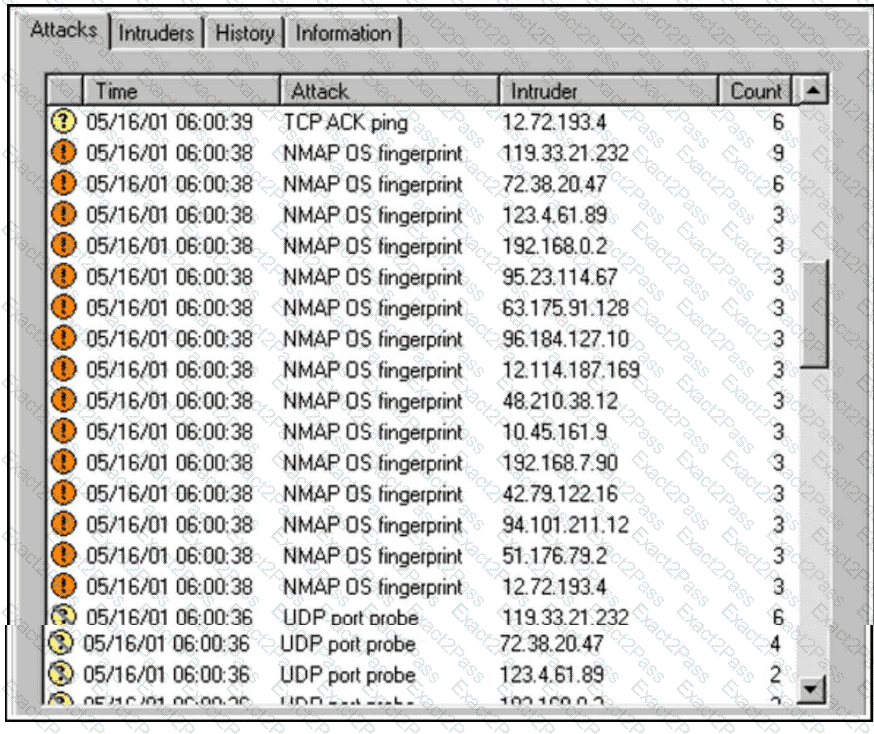
An increase in company traffic is observed by the SOC team. After they investigate the spike, it is concluded that the increase is due to ongoing scanning activity. Further analysis reveals that an adversary used Nmap for OS fingerprinting. Which type of indicators used by the adversary sits highest on the Pyramid of Pain?

