Last Update 12 hours ago Total Questions : 175
The Implementing Secure Solutions with Virtual Private Networks (SVPN) content is now fully updated, with all current exam questions added 12 hours ago. Deciding to include 300-730 practice exam questions in your study plan goes far beyond basic test preparation.
You'll find that our 300-730 exam questions frequently feature detailed scenarios and practical problem-solving exercises that directly mirror industry challenges. Engaging with these 300-730 sample sets allows you to effectively manage your time and pace yourself, giving you the ability to finish any Implementing Secure Solutions with Virtual Private Networks (SVPN) practice test comfortably within the allotted time.
A Cisco AnyConnect client establishes a SSL VPN connection with an ASA at the corporate office. An engineer must ensure that the client computer meets the enterprise security policy. Which feature can update the client to meet an enterprise security policy?
Refer to the exhibit.
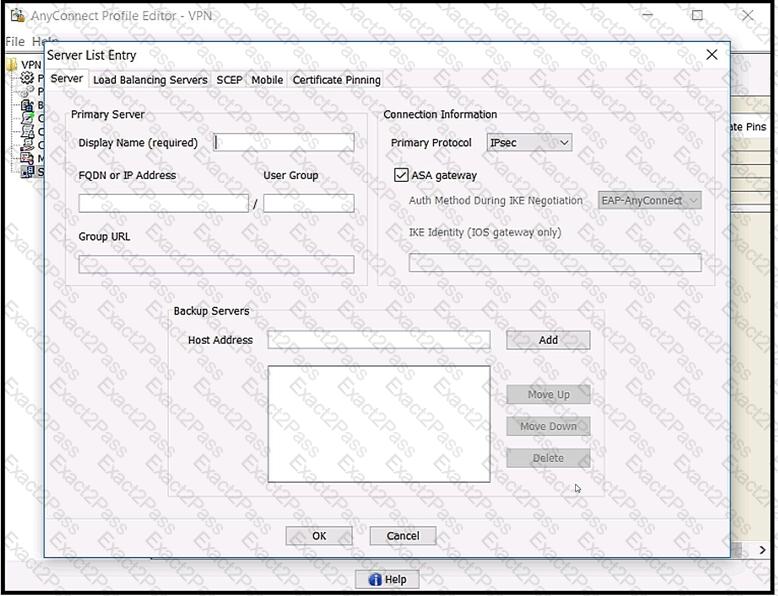
Which value must be configured in the User Group field when the Cisco AnyConnect Profile is created to connect to an ASA headend with IPsec as the primary protocol?
Which two types of web resources or protocols are enabled by default on the Cisco ASA Clientless SSL VPN portal? (Choose two.)
Which two statements about the Cisco ASA Clientless SSL VPN solution are true? (Choose two.)
Which feature allows the ASA to handle nonstandard applications and web resources so that they display correctly over a clientless SSL VPN connection?
Refer to the exhibit.
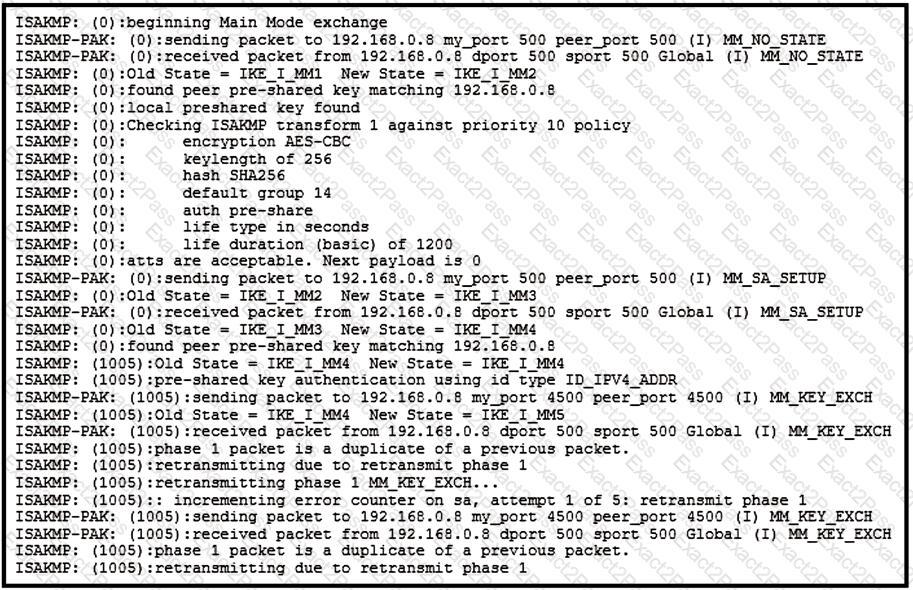
A site-to-site tunnel between two sites is not coming up. Based on the debugs, what is the cause of this issue?
Refer to the exhibit.
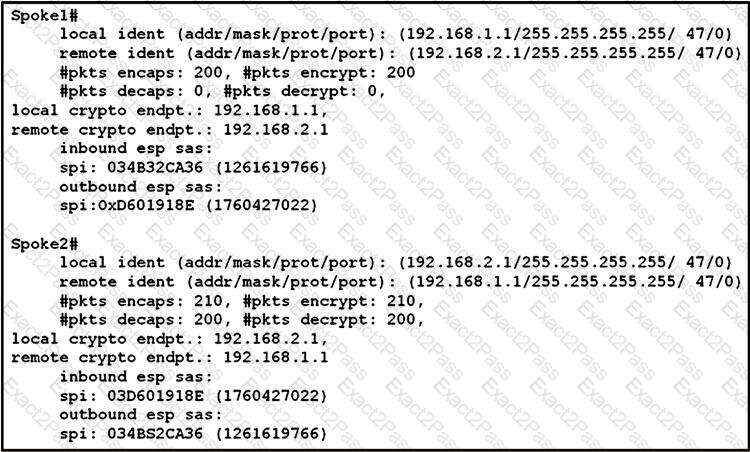
An engineer is troubleshooting a new GRE over IPsec tunnel. The tunnel is established but the engineer cannot ping from spoke 1 to spoke 2. Which type of traffic is being blocked?

