Last Update 22 hours ago Total Questions : 30
The FCP - Secure Wireless LAN 7.4 Administrator content is now fully updated, with all current exam questions added 22 hours ago. Deciding to include FCP_FWF_AD-7.4 practice exam questions in your study plan goes far beyond basic test preparation.
You'll find that our FCP_FWF_AD-7.4 exam questions frequently feature detailed scenarios and practical problem-solving exercises that directly mirror industry challenges. Engaging with these FCP_FWF_AD-7.4 sample sets allows you to effectively manage your time and pace yourself, giving you the ability to finish any FCP - Secure Wireless LAN 7.4 Administrator practice test comfortably within the allotted time.
Refer to the exhibit.
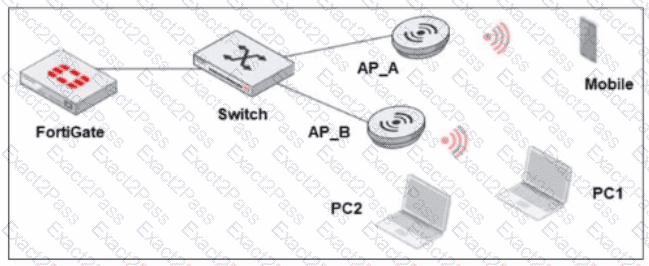
A new security policy is made by the IT department to prevent direct communication between wireless stations There is one SSID configured in bridge mode Which statement is correct as a plan of action to update the wireless network configuration?
Refer to the exhibit.

The wireless station with MAC address 5a:29:94:87:f7:b8 has made multiple attempts to connect to the CORP.DATA SSID Despite client-association-failure event logs the wireless station connects on the final attempt
Why did the wireless station fail to connect initially?
A wireless station has reported several connection issues with FortiAP that have not been resolved using standard troubleshooting tools As a wireless network administrator you are planning to perform additional advanced-level troubleshooting Which two steps must you take to analyze and troubleshoot the issue? (Choose two)
Refer to the exhibit.
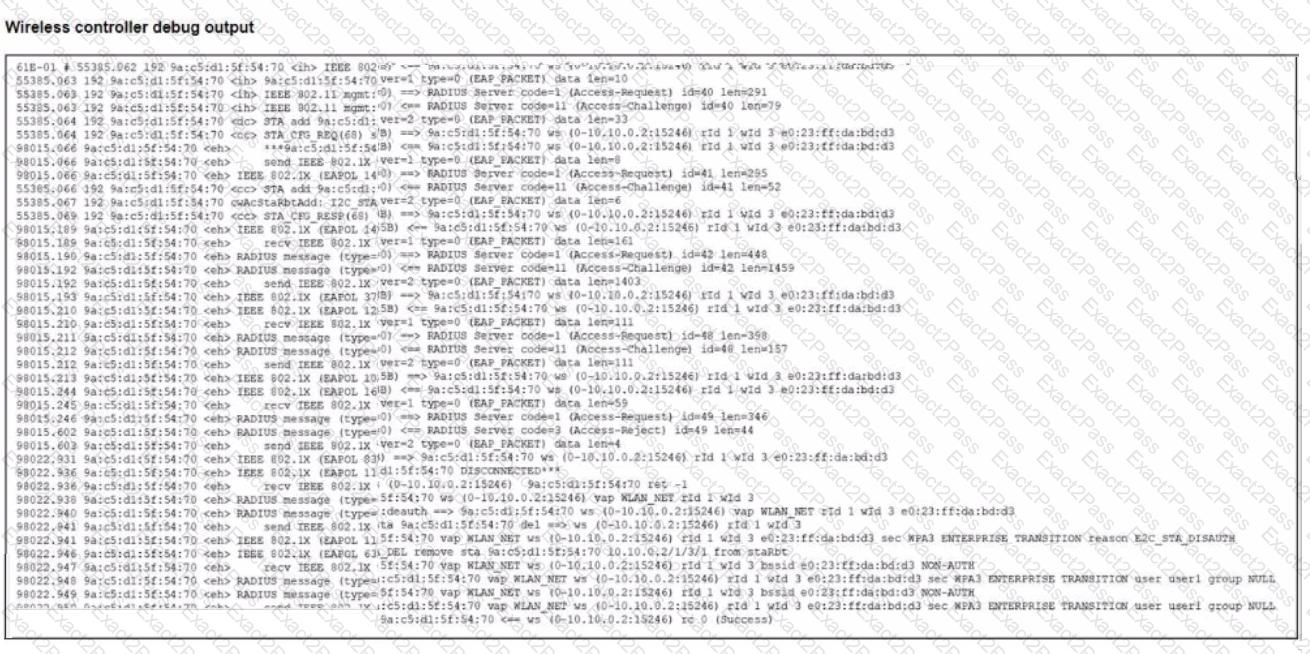
The wireless client connects to the wireless network on WLAN_NET tunnel mode interface The exhibit stows the client exchange communication with the wireless controller and the RADIUS server
Which two issues can you observe in the wireless station debug outputs (Choose two.)
An IT department must provide wireless security to employees connected over remote hortiAP devices who must access corporate resources at the mam office Which action must the IT department take to enforce security policies for all wireless stations accessing corporate resources across all remote locations?
Refer to the exhibit.
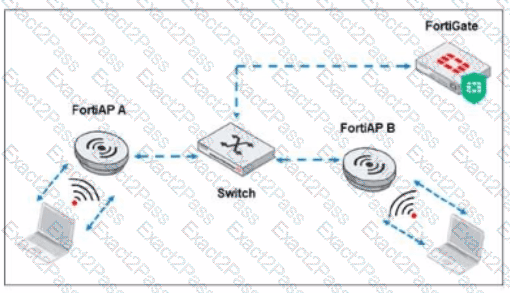
Which traffic is crucial between the FortiAP devices and FortiGate to support AP configuration updates and management services?

