Last Update 21 hours ago Total Questions : 167
The Aruba Certified Network Security Associate Exam content is now fully updated, with all current exam questions added 21 hours ago. Deciding to include HPE6-A78 practice exam questions in your study plan goes far beyond basic test preparation.
You'll find that our HPE6-A78 exam questions frequently feature detailed scenarios and practical problem-solving exercises that directly mirror industry challenges. Engaging with these HPE6-A78 sample sets allows you to effectively manage your time and pace yourself, giving you the ability to finish any Aruba Certified Network Security Associate Exam practice test comfortably within the allotted time.
A company has HPE Aruba Networking Mobility Controllers (MCs), HPE Aruba Networking campus APs, and AOS-CX switches. The company plans to use HPE Aruba Networking ClearPass Policy Manager (CPPM) to classify endpoints by type. The company is contemplating the use of ClearPass's TCP fingerprinting capabilities.
What is a consideration for using those capabilities?
You are checking the Security Dashboard in the Web Ul for your ArubaOS solution and see that Wireless Intrusion Prevention (WIP) has discovered a rogue radio operating in ad hoc mode with open security. What correctly describes a threat that the radio could pose?
Refer to the exhibits.
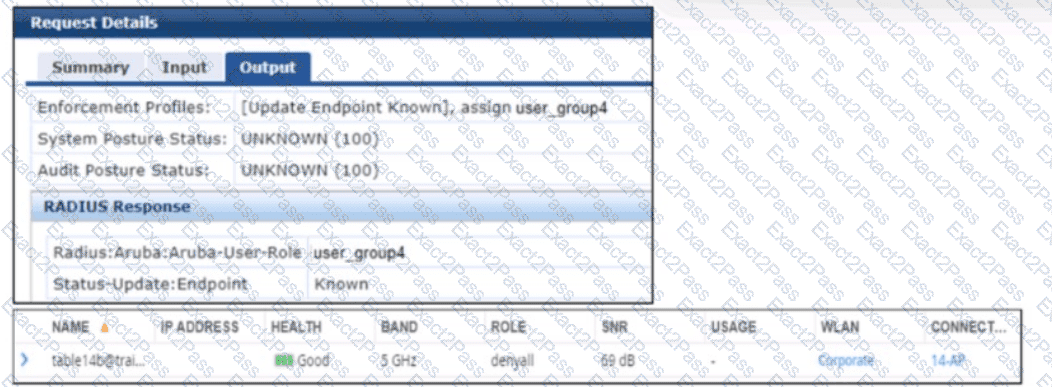
A company has added a new user group. Users in the group try to connect to the WLAN and receive errors that the connection has no Internet access. The users cannot reach any resources. The first exhibit shows the record for one of the users who cannot connect. The second exhibit shows the role to which the AOS device assigned the user’s client.
What is a likely problem?
Refer to the exhibit:
port-access role role1 vlan access 11
port-access role role2 vlan access 12
port-access role role3 vlan access 13
port-access role role4 vlan access 14
aaa authentication port-access dot1x authenticator
enable
interface 1/1/1
no shutdown
no routing
vlan access 1
aaa authentication port-access critical-role role1
aaa authentication port-access preauth-role role2
aaa authentication port-access auth-role role3
interface 1/1/2
no shutdown
no routing
vlan access 1
aaa authentication port-access critical-role role1
aaa authentication port-access preauth-role role2
aaa authentication port-access auth-role role3
The exhibit shows the configuration on an AOS-CX switch.
Client1 connects to port 1/1/1 and authenticates to HPE Aruba Networking ClearPass Policy Manager (CPPM). CPPM sends an Access-Accept with this VSA: Aruba-User-Role: role4.
Client2 connects to port 1/1/2 and does not attempt to authenticate.To which roles are the users assigned?
You configure an ArubaOS-Switch to enforce 802.1X authentication with ClearPass Policy Manager (CPPM) denned as the RADIUS server Clients cannot authenticate You check Aruba ClearPass Access Tracker and cannot find a record of the authentication attempt.
What are two possible problems that have this symptom? (Select two)
Your AOS solution has detected a rogue AP with Wireless Intrusion Prevention (WIP). Which information about the detected radio can best help you to locate the rogue device?
Device A is contacting https://arubapedia.arubanetworks.com. The web server sends a certificate chain. What does the browser do as part of validating the web server certificate?

