Last Update 20 hours ago Total Questions : 65
The Design - Associate (JNCIA-Design) content is now fully updated, with all current exam questions added 20 hours ago. Deciding to include JN0-1103 practice exam questions in your study plan goes far beyond basic test preparation.
You'll find that our JN0-1103 exam questions frequently feature detailed scenarios and practical problem-solving exercises that directly mirror industry challenges. Engaging with these JN0-1103 sample sets allows you to effectively manage your time and pace yourself, giving you the ability to finish any Design - Associate (JNCIA-Design) practice test comfortably within the allotted time.
Which two statements are correct about using BGP as the underlay routing protocol in an IP fabric? (Choose two.)
What is an overlay solution that expands the Layer 2 network space across the WAN?
Click the Exhibit button.
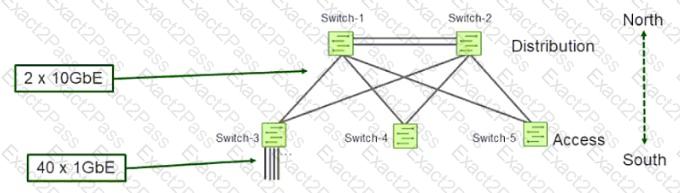
Referring to the exhibit, which oversubscription ratio applies to Switch-3?
What is a design consideration for using IBGP for the underlay in a Clos data center fabric?
You are a network engineer at a large university. The architecture team has recently chosen Mist to replace the existing controller-based system and has replaced all the access points (APs) throughout the campus. Since the migration, users have been complaining about VoIP calls being dropped while moving between buildings. You have already validated that the APs provide appropriate coverage.
Which change would help alleviate this issue?
You want to provide employees with controlled access to the corporate network with company devices, ensure secure access for printers and cameras, and enable employees to use their devices on the corporate network.
Which two methods satisfy the requirements? (Choose two.)
You are asked to design a branch WAN. The branch sites have limited bandwidth and it is imperative to limit overhead.
Which technology will satisfy the requirements?

