Last Update 9 hours ago Total Questions : 98
The Security, Specialist (JNCIS-SEC) content is now fully updated, with all current exam questions added 9 hours ago. Deciding to include JN0-335 practice exam questions in your study plan goes far beyond basic test preparation.
You'll find that our JN0-335 exam questions frequently feature detailed scenarios and practical problem-solving exercises that directly mirror industry challenges. Engaging with these JN0-335 sample sets allows you to effectively manage your time and pace yourself, giving you the ability to finish any Security, Specialist (JNCIS-SEC) practice test comfortably within the allotted time.
Which two statements are true about the vSRX? (Choose two.)
Exhibit
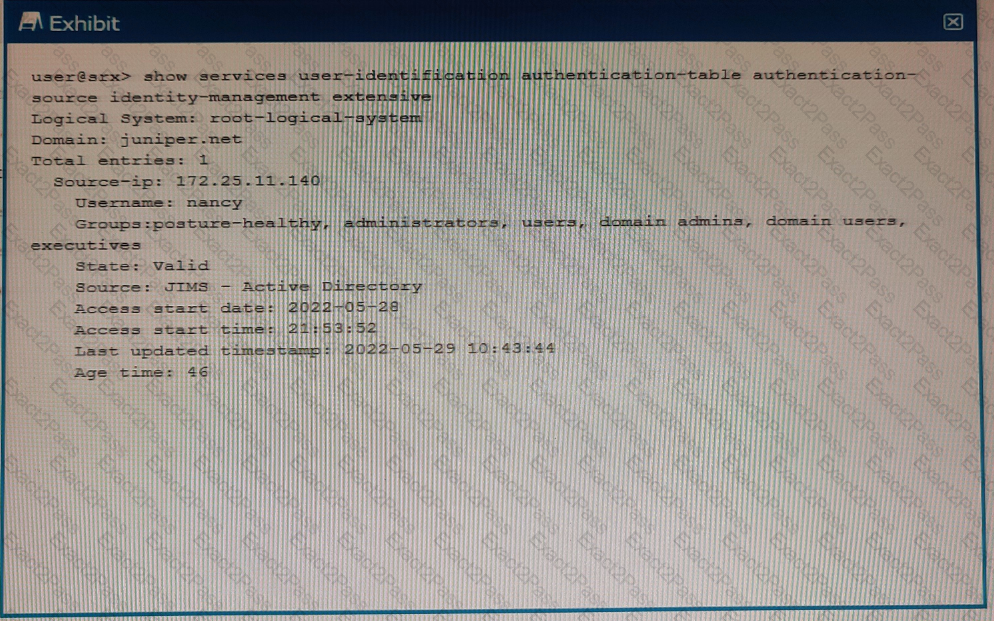
Referring to the exhibit, which two statements are true? (Choose two.)
When a security policy is deleted, which statement is correct about the default behavior of active sessions allowed by that policy?
When a security policy is modified, which statement is correct about the default behavior for active sessions allowed by that policy?
You are configuring logging for a security policy.
In this scenario, in which two situations would log entries be generated? (Choose two.)
Which two statements are correct about Juniper ATP Cloud? (Choose two.)
You have implemented a vSRX in your VMware environment. You want to implement a second vSRX Series device and enable chassis clustering.
Which two statements are correct in this scenario about the control-link settings? (Choose two.)

