Last Update 10 hours ago Total Questions : 61
The Designing and Implementing Secure Cloud Access for Users and Endpoints (SCAZT) content is now fully updated, with all current exam questions added 10 hours ago. Deciding to include 300-740 practice exam questions in your study plan goes far beyond basic test preparation.
You'll find that our 300-740 exam questions frequently feature detailed scenarios and practical problem-solving exercises that directly mirror industry challenges. Engaging with these 300-740 sample sets allows you to effectively manage your time and pace yourself, giving you the ability to finish any Designing and Implementing Secure Cloud Access for Users and Endpoints (SCAZT) practice test comfortably within the allotted time.

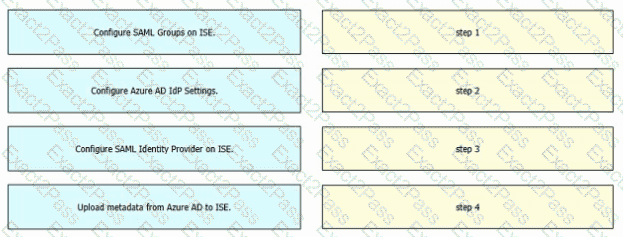
Refer to the exhibit. An engineer must configure SAML single sign-on in Cisco ISE to use Microsoft Azure AD as an identity provider. Drag and drop the steps from the left into the sequence on the right to configure Cisco ISE with SAML single sign-on.
According to Cisco Security Reference Architecture, which solution provides threat intelligence and malware analytics?
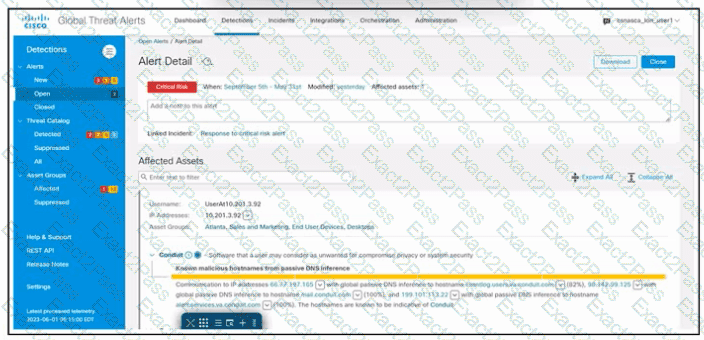
Refer to the exhibit. An engineer is investigating the critical alert received in Cisco Secure Network Analytics. The engineer confirms that the incident is valid. Which two actions must be taken? (Choose two.)
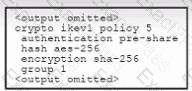
Refer to the exhibit. An engineer must configure a remote access IPsec/IKEv1 VPN that will use AES256 and SHA256 on a Cisco ASA firewall. The indicated configuration was applied to the firewall; however, the tunnel fails to establish. Which two IKEv1 policy commands must be run to meet the requirement? (Choose two.)
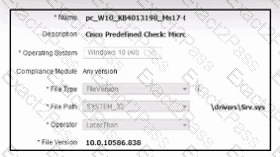
Refer to the exhibit. A security engineer must configure a posture policy in Cisco ISE to ensure that employee laptops have a critical patch for WannaCry installed before they can access the network. Which posture condition must the engineer configure?
Which types of algorithm does a web application firewall use for zero-day DDoS protection?
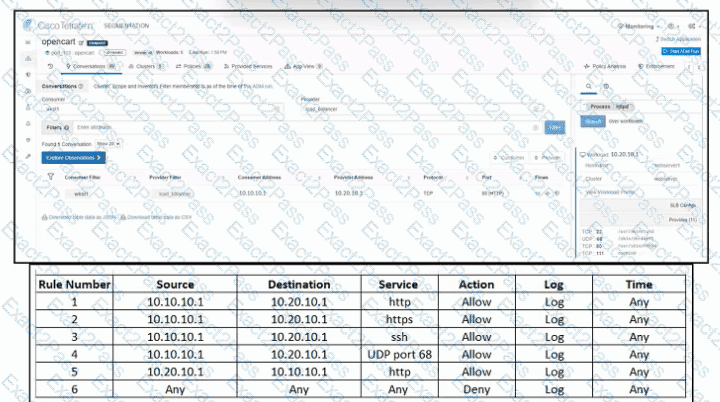
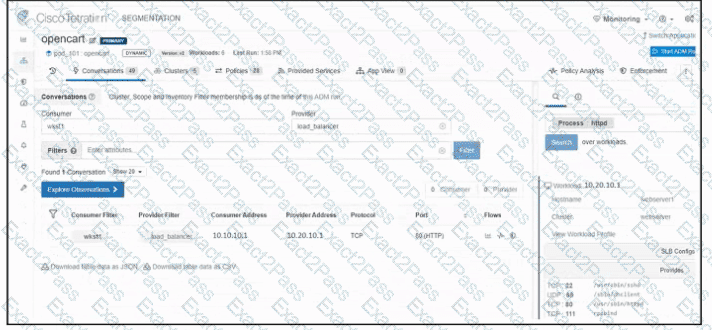
Refer to the exhibit. An engineer must create a firewall policy to allow web server communication only. The indicated firewall policy was applied; however, a recent audit requires that all firewall policies be optimized. Which set of rules must be deleted?

