Last Update 23 hours ago Total Questions : 131
The Conducting Forensic Analysis and Incident Response Using Cisco CyberOps Technologies (CBRFIR) content is now fully updated, with all current exam questions added 23 hours ago. Deciding to include 300-215 practice exam questions in your study plan goes far beyond basic test preparation.
You'll find that our 300-215 exam questions frequently feature detailed scenarios and practical problem-solving exercises that directly mirror industry challenges. Engaging with these 300-215 sample sets allows you to effectively manage your time and pace yourself, giving you the ability to finish any Conducting Forensic Analysis and Incident Response Using Cisco CyberOps Technologies (CBRFIR) practice test comfortably within the allotted time.
During a routine inspection of system logs, a security analyst notices an entry where Microsoft Word initiated a PowerShell command with encoded arguments. Given that the user's role does not involve scripting or advanced document processing, which action should the analyst take to analyze this output for potential indicators of compromise?
Snort detects traffic that is targeting vulnerabilities in files that belong to software in the Microsoft Office suite. On a SIEM tool, the SOC analyst sees an alert from Cisco FMC. Cisco FMC is implemented with Snort IDs. Which alert message is shown?
Refer to the exhibit.
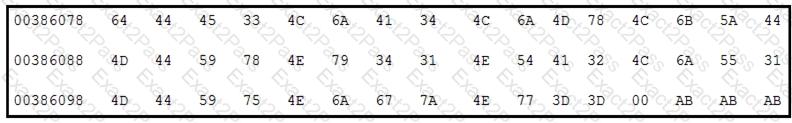
Which encoding technique is represented by this HEX string?
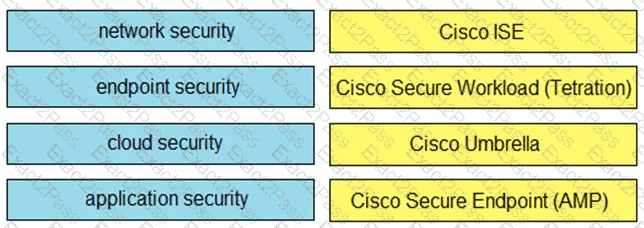
Drag and drop the capabilities on the left onto the Cisco security solutions on the right.
Refer to the exhibit.
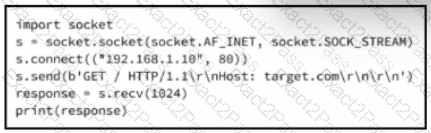
A cybersecurity analyst is presented with the snippet of code used by the threat actor and left behind during the latest incident and is asked to determine its type based on its structure and functionality. What is the type of code being examined?
Refer to the exhibit.
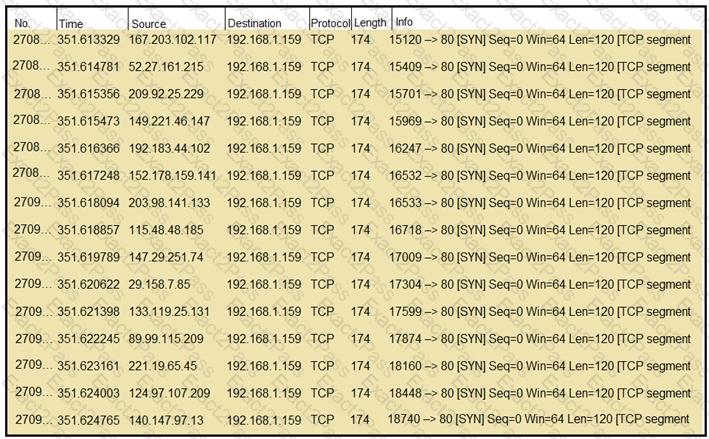
What should an engineer determine from this Wireshark capture of suspicious network traffic?
Rotor to the exhibit.
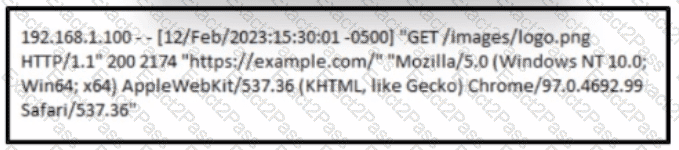
A cybersecurity analyst must analyst the logs from an Apache server for the client. The concern is that an offboarded employee home IP address was potentially used to access the company web server via a still active VPN connection Based on this log entry, what should an analyst conclude?

