Last Update 11 hours ago Total Questions : 97
The Service Provider Professional (JNCIP-SP) content is now fully updated, with all current exam questions added 11 hours ago. Deciding to include JN0-664 practice exam questions in your study plan goes far beyond basic test preparation.
You'll find that our JN0-664 exam questions frequently feature detailed scenarios and practical problem-solving exercises that directly mirror industry challenges. Engaging with these JN0-664 sample sets allows you to effectively manage your time and pace yourself, giving you the ability to finish any Service Provider Professional (JNCIP-SP) practice test comfortably within the allotted time.
Exhibit
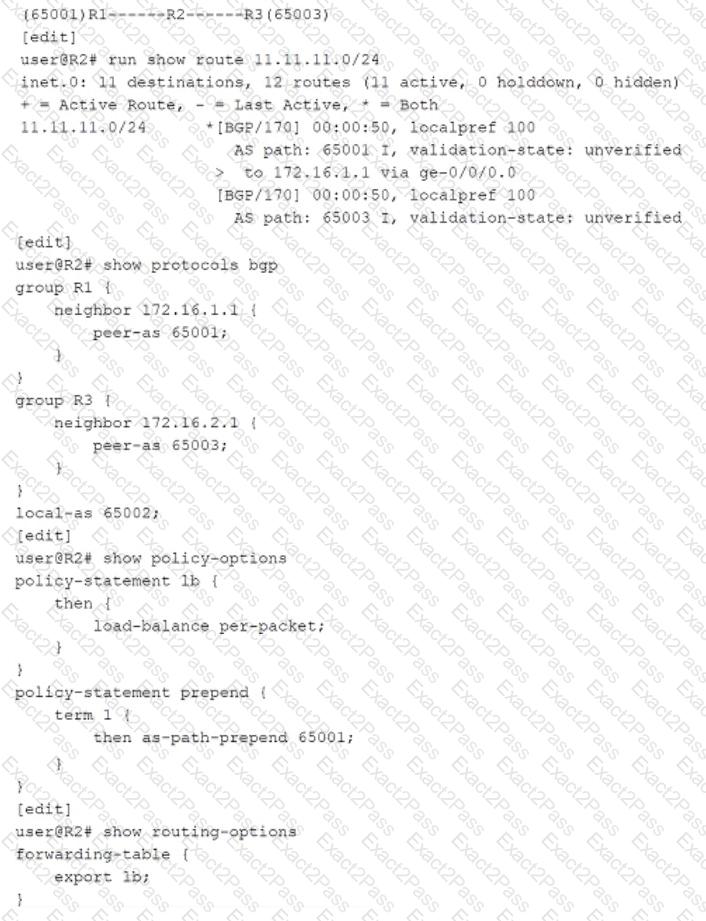
R2 is receiving the same route from R1 and R3. You must ensure that you can load balance traffic for that route.
Referring to the exhibit, which configuration change will allow load balancing?
Which two statements are correct about VPLS tunnels? (Choose two.)
Which two statements about IS-IS are correct? (Choose two.)
Exhibit
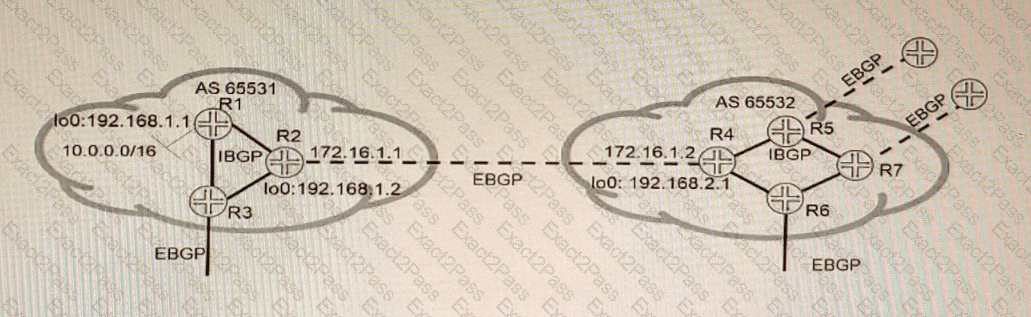
Referring to the exhibit, which three statements are correct about route 10 0 0.0/16 when using the default BGP advertisement rules'? (Choose three.)
Exhibit
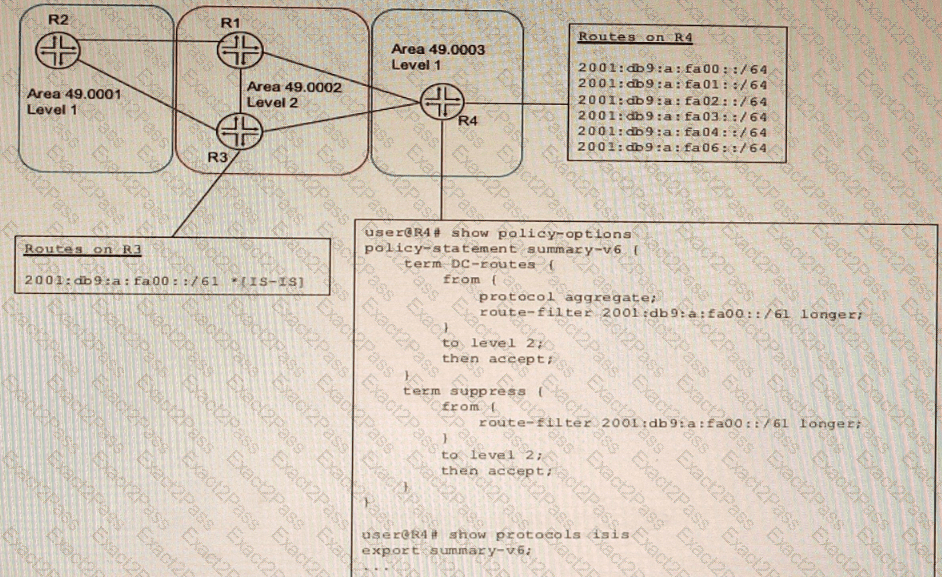
A network designer would like to create a summary route as shown in the exhibit, but the configuration is not working.
Which three configuration changes will create a summary route? (Choose three.)
Which two statements are correct about a sham link? (Choose two.)
Which origin code is preferred by BGP?

