Last Update 22 hours ago Total Questions : 47
The Fortinet NSE 6 - FortiNAC 9.1 content is now fully updated, with all current exam questions added 22 hours ago. Deciding to include NSE6_FNC-9.1 practice exam questions in your study plan goes far beyond basic test preparation.
You'll find that our NSE6_FNC-9.1 exam questions frequently feature detailed scenarios and practical problem-solving exercises that directly mirror industry challenges. Engaging with these NSE6_FNC-9.1 sample sets allows you to effectively manage your time and pace yourself, giving you the ability to finish any Fortinet NSE 6 - FortiNAC 9.1 practice test comfortably within the allotted time.
What capability do logical networks provide?
By default, if more than 20 hosts are seen connected on a single port simultaneously, what will happen to the port?
What would occur if both an unknown (rogue) device and a known (trusted) device simultaneously appeared on a port that is a member of the Forced Registration port group?
What agent is required in order to detect an added USB drive?
Which three circumstances trigger Layer 2 polling of infrastructure devices? (Choose three.)
View the command and output shown in the exhibit.
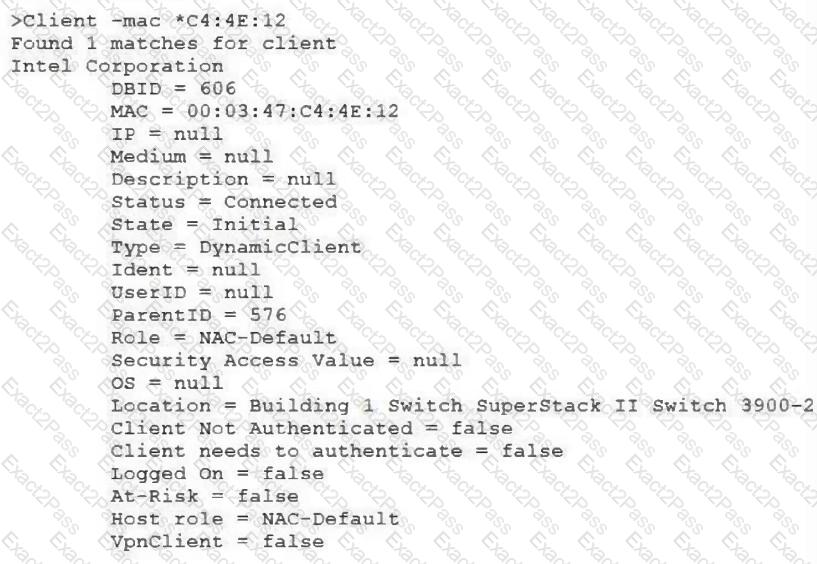
What is the current state of this host?
Where do you look to determine when and why the FortiNAC made an automated network access change?

