Last Update 22 hours ago Total Questions : 441
The Implementing Cisco SD-WAN Solutions (300-415 ENSDWI) content is now fully updated, with all current exam questions added 22 hours ago. Deciding to include 300-415 practice exam questions in your study plan goes far beyond basic test preparation.
You'll find that our 300-415 exam questions frequently feature detailed scenarios and practical problem-solving exercises that directly mirror industry challenges. Engaging with these 300-415 sample sets allows you to effectively manage your time and pace yourself, giving you the ability to finish any Implementing Cisco SD-WAN Solutions (300-415 ENSDWI) practice test comfortably within the allotted time.
Which plane builds and maintains the network topology and makes decisions on traffic flows?
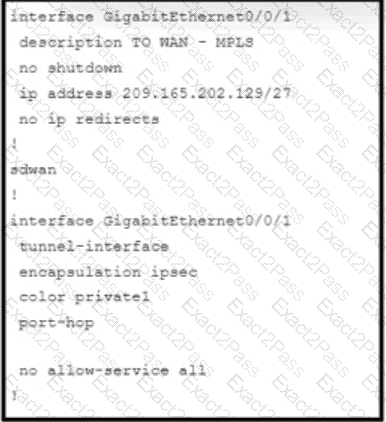
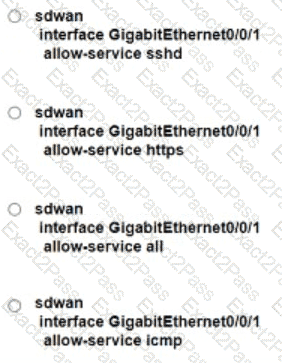
Refer to the exhibit. An engineer is enabling command line access via MPLS for in-band management. Which command completes the partial SD-WAN interface configuration with the highest degree of security?
Which website allows access to visualize the geography screen from vManager using the internet?
Which two products that perform lifecycle management for virtual instances are supported by WAN Edge cloud routers? (Choose two.)
An engineer configures an application-aware routing policy for a group of sites The locations depend on public and private transports The policy does not work as expected when one of the transports does not perform properly This policy is configured:

which configuration completes the policy so that it works for all locations?
A)
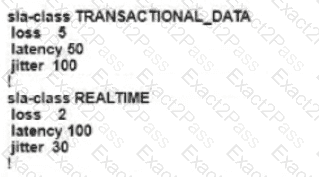
B)
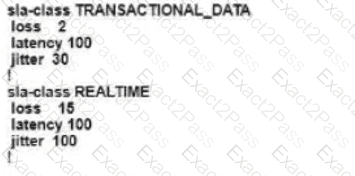
C)
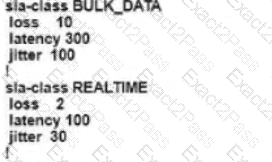
D)
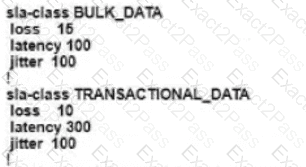
A network administrator is configuring VRRP to avoid a traffic black hole when the transport side of the network is down on the primary device. What must be configured to get the fastest failover to standby?
How many cloud gateway instance(s) can be created per region when provisioning Cloud OnRamp for Multicloud from AWS in a multiregion environment?

