Last Update 22 hours ago Total Questions : 247
The Implementing Cisco Application Centric Infrastructure (300-620 DCACI) content is now fully updated, with all current exam questions added 22 hours ago. Deciding to include 300-620 practice exam questions in your study plan goes far beyond basic test preparation.
You'll find that our 300-620 exam questions frequently feature detailed scenarios and practical problem-solving exercises that directly mirror industry challenges. Engaging with these 300-620 sample sets allows you to effectively manage your time and pace yourself, giving you the ability to finish any Implementing Cisco Application Centric Infrastructure (300-620 DCACI) practice test comfortably within the allotted time.
Which two dynamic routing protocols are supported when using Cisco ACI to connect to an external Layer 3 network? (Choose two.)
What are two descriptions of ACI multi-site? (Choose two.)
Cisco ACI fabric must send a packet between two pods in a Cisco AC1 Multi-Pod topology where ARP flooding is disabled within the bridge domain. How does a Cisco ACI spine switch .. ARP messages from a leaf switch in POD1 to POD2?
All workloads in VLAN 1001 have been migrated into EPG-1001. The requirement is to move the gateway address for VLAN 1001 from the core outside the Cisco ACI fabric into the Cisco ACI fabric. The endpoints in EPG-1001 must route traffic to endpoints in other EPGs and minimize flooded traffic in the fabric. Which configuration set is needed on the bridge domain to meet these requirements?
Engineer must configure SNMP inside a Cisco ACI fabric. The engineer has created an SNMP Policy, called SNMP-policy and an SNMP Monitoring Group called SNMP-group1 that Contains five trap receivers. Which configuration set completes the configuration?
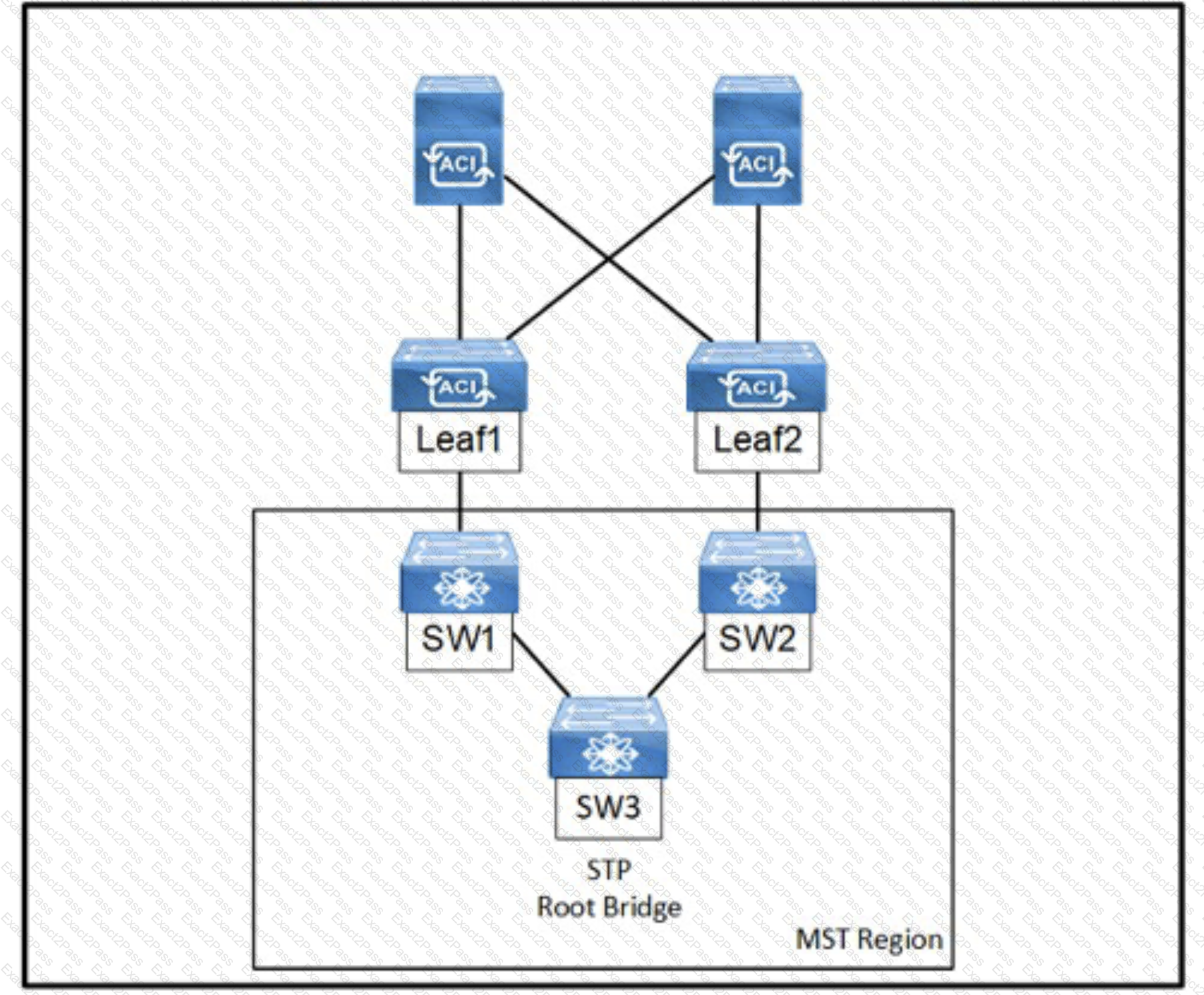
Refer to the exhibit, An engineer is deploying a Cisco ACI environment but experiences a STP loop between switch1 and switch2. Which configuration step is needed to break the STP loop?
Refer to the exhibit.
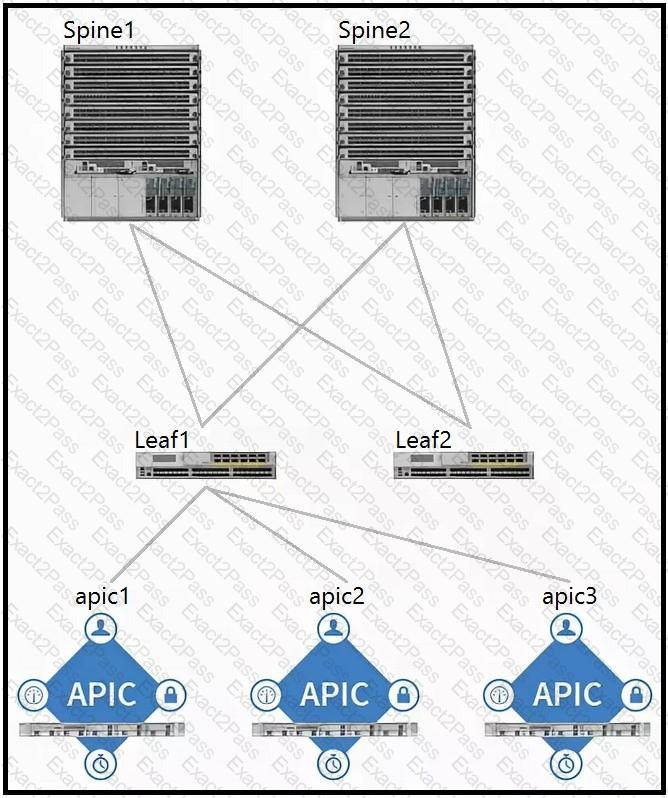
Which two components should be configured as route reflectors in the ACI fabric? (Choose two.)

