Last Update 22 hours ago Total Questions : 385
The Securing Networks with Cisco Firepower (300-710 SNCF) content is now fully updated, with all current exam questions added 22 hours ago. Deciding to include 300-710 practice exam questions in your study plan goes far beyond basic test preparation.
You'll find that our 300-710 exam questions frequently feature detailed scenarios and practical problem-solving exercises that directly mirror industry challenges. Engaging with these 300-710 sample sets allows you to effectively manage your time and pace yourself, giving you the ability to finish any Securing Networks with Cisco Firepower (300-710 SNCF) practice test comfortably within the allotted time.
An engineermustconfigure a Cisco FMC dashboard in a multidomain deployment Which action must the engineer take to edit a report template from an ancestor domain?
What is the maximum bit size that Cisco FMC supports for HTTPS certificates?
The network administrator wants to enhance the network security posture by enabling machine learning tor malware detection due to a concern with suspicious Microsoft executable file types that were seen while creating monthly security reports for the CIO. Which feature must be enabled to accomplish this goal?
Which process should be checked when troubleshooting registration issues between Cisco FMC and managed devices to verify that secure communication is occurring?
A Cisco FTD device is running in transparent firewall mode with a VTEP bridge group member ingress interface What must be considered by an engineer tasked with specifying a destination MAC address for a packet trace?
An engineer is configuring Cisco FMC and wants to allow multiple physical interfaces to be part of the same VLAN. The managed devices must be able to perform Layer 2 switching between interfaces, including sub-interfaces. What must be configured to meet these requirements?
Refer to the exhibit.
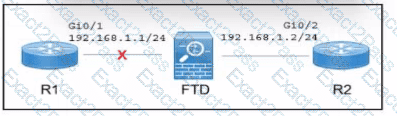
A Cisco Secure Firewall Threat Defense (FTD) device is deployed in inline mode with an inline set. The network engineer wants router R2 to remove the directly connected route M 68.1.0/24 from its routing table when the cable between routed R1 and the Secure FTD device Is disconnected. Which action must the engineer take?
1

