Last Update 5 hours ago Total Questions : 347
The Implementing Cisco Data Center Core Technologies (350-601 DCCOR) content is now fully updated, with all current exam questions added 5 hours ago. Deciding to include 350-601 practice exam questions in your study plan goes far beyond basic test preparation.
You'll find that our 350-601 exam questions frequently feature detailed scenarios and practical problem-solving exercises that directly mirror industry challenges. Engaging with these 350-601 sample sets allows you to effectively manage your time and pace yourself, giving you the ability to finish any Implementing Cisco Data Center Core Technologies (350-601 DCCOR) practice test comfortably within the allotted time.
An engineer implements an Application Performance Monitoring (APM) solution. The solution runs in a vSphere infrastructure where the vSwitch support for promiscuous mode is disabled for security reasons. As a result, the final implementation must receive a copy of bidirectional traffic to a load balancer that is connected to a Cisco Nexus 93108 series switch. The APN solution GRE encapsulated traffic. Which configuration must be applied to the switch to meet this requirement?
What is the impact of upgrading the firmware of the Cisco UCS Manager?
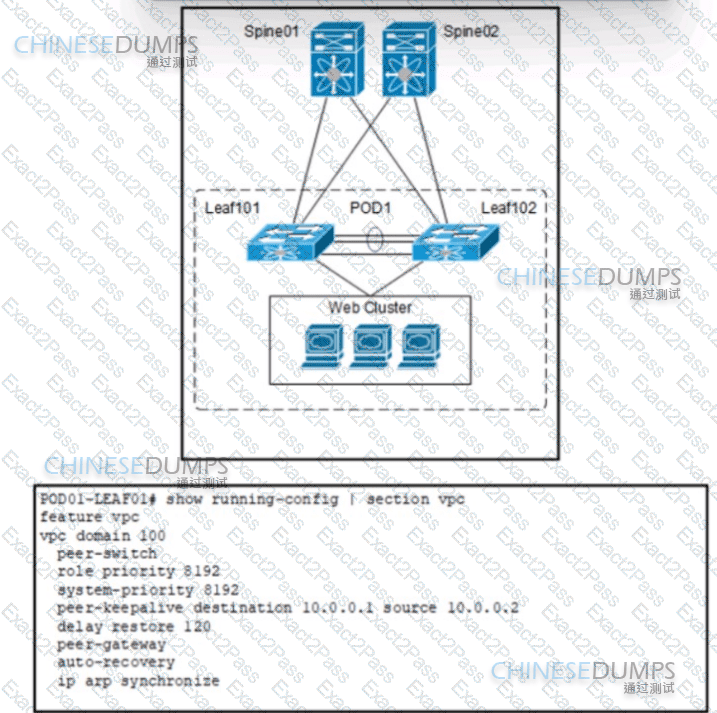
Refer to the exhibit. An engineer implements a VXLAN pod deployment with the vPC. During an upgrade of switches in POD1. Leaf 102 starts to rejoin the vPC pair. Also, traffic to and from the Web Cluster becomes intermittent for five minutes. Which additional command must be applied on both switches to resolve this issue?
What is a benefit of using the Cisco UCS Lightweight upgrade feature?
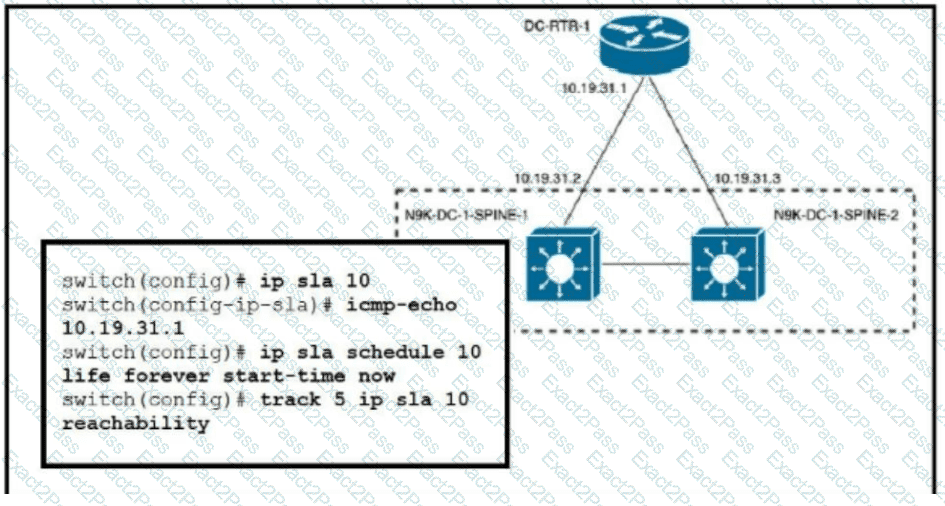
Refer to the exhibit. An engineer must invoke a Python script that alerts the operations team when the router DC-RTR-1 becomes unreachable. Which configuration set accomplishes this task?
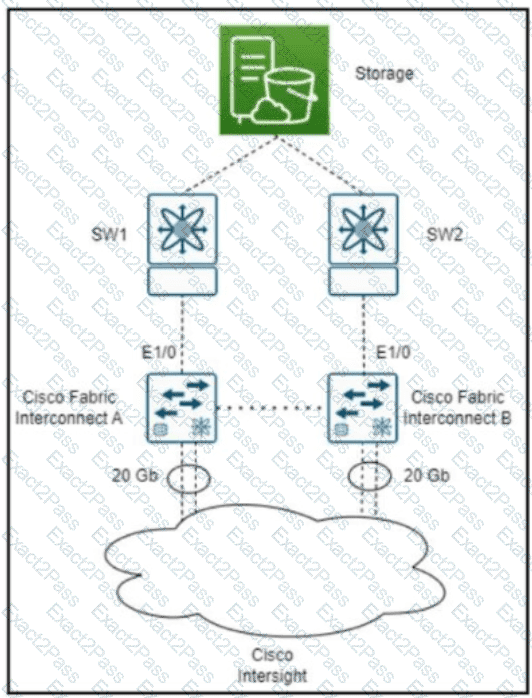
Refer to the exhibit. An engineer must configure infrastructure monitoring in a Cisco UCS domain to monitor traffic on the Cisco fabric interconnect A and Cisco fabric interconnect B port links connected to Cisco MDS switches SW1 and SW2. The monitored traffic must be sent to Cisco Intersight at 20 Gbps for further analysis. Which command must be run on a UCS device after the create eth-mon-eession EthMonitor1/0 command is run?
A network engineer deploys a cloud service for a customer The customer wants complete control over the underlying operating system data and application Which cloud service model must be used to accomplish this goal?

