Last Update 4 hours ago Total Questions : 72
The Engineering Cisco Meraki Solutions (ECMS) v2.2 content is now fully updated, with all current exam questions added 4 hours ago. Deciding to include 500-220 practice exam questions in your study plan goes far beyond basic test preparation.
You'll find that our 500-220 exam questions frequently feature detailed scenarios and practical problem-solving exercises that directly mirror industry challenges. Engaging with these 500-220 sample sets allows you to effectively manage your time and pace yourself, giving you the ability to finish any Engineering Cisco Meraki Solutions (ECMS) v2.2 practice test comfortably within the allotted time.
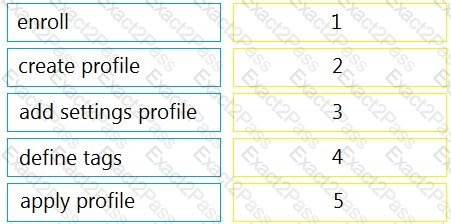
Drag and drop the steps from the left into the sequence on the right to manage device control, according to Cisco Meraki best practice.
What happens to an unsupervised iOS device when the “Meraki management” profile is removed?
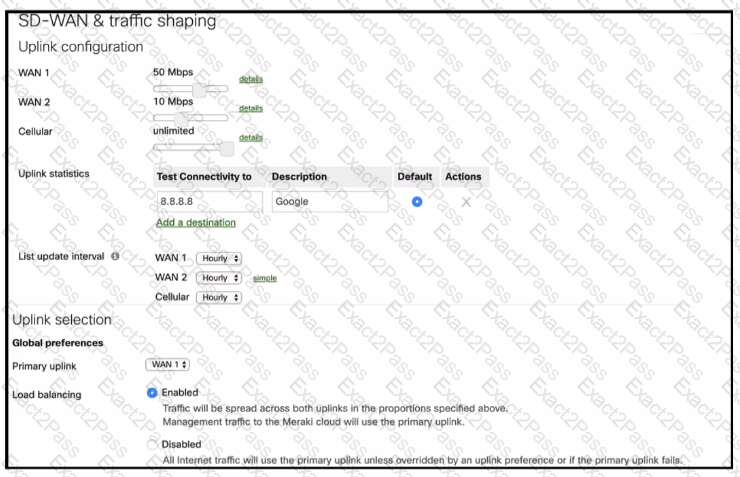
Refer to the exhibit. What Is the ratio of internet-bound flows that route via WAN 1 compared with WAN 2?
Which API endpoint clones a new Organization?
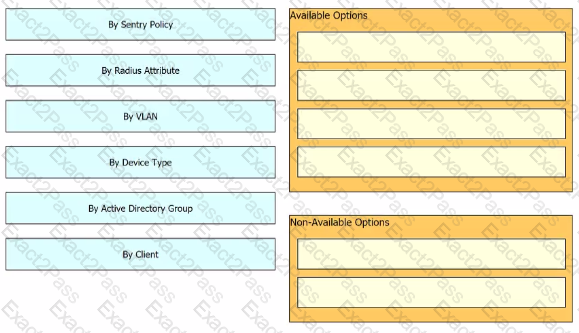
Drag and drop the settings from the left onto the available or non-available methods of applying a group policy to a Cisco Meraki MR access point on the right.
Which Meraki Dashboard menu section is accessed to enable Sentry enrollment on an SSID?
Air Marshal has contained a malicious SSID.
What are two effects on connectivity? (Choose two.)

