Last Update 22 hours ago Total Questions : 84
The CompTIA CloudNetX Exam content is now fully updated, with all current exam questions added 22 hours ago. Deciding to include CNX-001 practice exam questions in your study plan goes far beyond basic test preparation.
You'll find that our CNX-001 exam questions frequently feature detailed scenarios and practical problem-solving exercises that directly mirror industry challenges. Engaging with these CNX-001 sample sets allows you to effectively manage your time and pace yourself, giving you the ability to finish any CompTIA CloudNetX Exam practice test comfortably within the allotted time.
A network architect must design a new branch network that meets the following requirements:
No single point of failure
Clients cannot be impacted by changes to the underlying medium
Clients must be able to communicate directly to preserve bandwidth
Which of the following network topologies should the architect use?
A network engineer is installing new switches in the data center to replace existing infrastructure. The previous network hardware had administrative interfaces that were plugged into the existing network along with all other server hardware on the same subnet. Which of the following should the engineer do to better secure these administrative interfaces?
As part of a project to modernize a sports stadium and improve the customer service experience for fans, the stadium owners want to implement a new wireless system. Currently, all tickets are electronic and managed by the stadium mobile application. The new solution is required to allow location tracking precision within 5ft (1.5m) of fans to deliver the following services:
Emergency/security assistance
Mobile food order
Event special effects
Raffle winner location displayed on the giant stadium screen
Which of the following technologies enables location tracking?
A network engineer at an e-commerce organization must improve the following dashboard due to a performance issue on the website:
(Refer to the image: Website performance monitoring dashboard showing metrics like network usage, CPU usage, memory usage, and disk usage over time.)
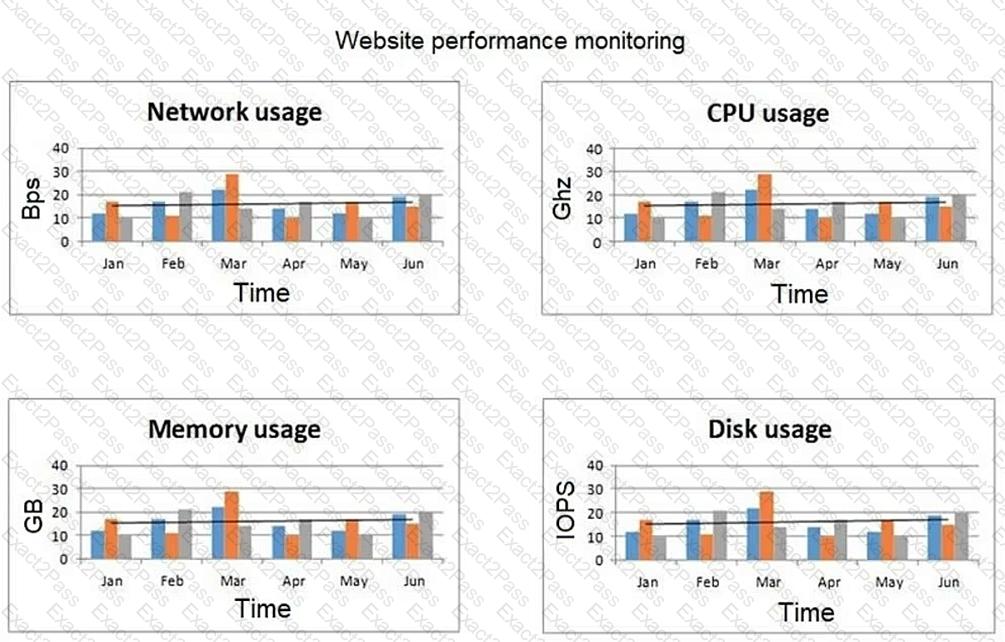
Which of the following is the most useful information to add to the dashboard for the operations team?
A company hosts a cloud-based e-commerce application and only wants the application accessed from certain locations. The network team configures a cloud firewall with WAF enabled, but users can access the application globally. Which of the following should the network team do?
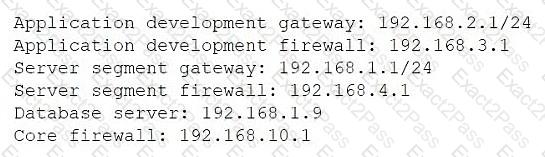
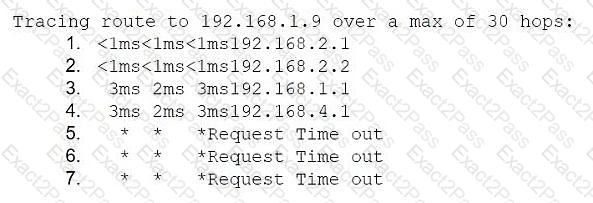
Application development team users are having issues accessing the database server within the cloud environment. All other users are able to use SSH to access this server without issues. The network architect reviews the following information to troubleshoot the issue:
Traceroute output from an application developer's machine with the assigned IP 192.168.2.7:
Application development gateway: 192.168.2.1/24
Server segment gateway: 192.168.1.1/24
Database server: 192.168.1.9
Application developer machine IP: 192.168.2.7
Traceroute ends at hop 4: 192.168.4.1 (server segment firewall), then times out
Which of the following is the most likely cause of the issue?
A network administrator recently deployed new Wi-Fi 6E access points in an office and enabled 6GHz coverage. Users report that when they are connected to the new 6GHz SSID, the performance is worse than the 5GHz SSID. The network administrator suspects that there is a source of 6GHz interference in the office. Using the troubleshooting methodology, which of the following actions should the network administrator do next?

