Last Update 21 hours ago Total Questions : 256
The CompTIA Cloud+ (2025) content is now fully updated, with all current exam questions added 21 hours ago. Deciding to include CV0-004 practice exam questions in your study plan goes far beyond basic test preparation.
You'll find that our CV0-004 exam questions frequently feature detailed scenarios and practical problem-solving exercises that directly mirror industry challenges. Engaging with these CV0-004 sample sets allows you to effectively manage your time and pace yourself, giving you the ability to finish any CompTIA Cloud+ (2025) practice test comfortably within the allotted time.
A company requests that its cloud administrator provision virtual desktops for every user. Given the following information:
• One hundred users are at the company.
• A maximum of 30 users work at the same time.
• Users cannot be interrupted while working on the desktop.
Which of the following strategies will reduce costs the most?
For compliance purposes, a cloud developer at an insurance company needs to save all customer policies for more than ten years. Which of the following options is the most cost-
efficient tier to save the data in the cloud?
A cloud engineer was deploying the company's payment processing application, but it failed with the following error log:
ERFOR:root: Transaction failed http 429 response, please try again Which of the following are the most likely causes for this error? (Select two).
A cloud consultant needs to modernize a legacy application that can no longer address user demand and is expensive to maintain. Which of the following is the best migration
strategy?
A company's content management system (CMS) service runs on an laaS cluster on a public cloud. The CMS service is frequently targeted by a malicious threat actor using DDoS.
Which of the following should a cloud engineer monitor to identify attacks?
A cloud engineer wants containers to run the latest version of a container base image to reduce the number of vulnerabilities. The applications in use requite Python 3.10 and ate not compatible with any other version. The containers' images are created every time a new version is released from the source image. Given the container Dockerfile below:

Which of the following actions will achieve the objectives with the least effort?
A cloud engineer wants to deploy a new application to the cloud and is writing the following script:
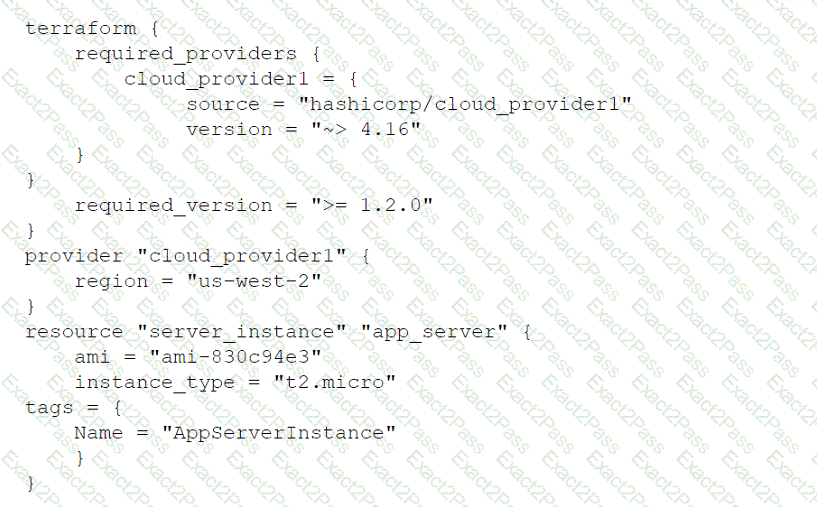
Which of the following actions will this script perform?

