Last Update 2 hours ago Total Questions : 156
The HCIP-Datacom-Advanced Routing & Switching Technology V1.0 content is now fully updated, with all current exam questions added 2 hours ago. Deciding to include H12-831_V1.0 practice exam questions in your study plan goes far beyond basic test preparation.
You'll find that our H12-831_V1.0 exam questions frequently feature detailed scenarios and practical problem-solving exercises that directly mirror industry challenges. Engaging with these H12-831_V1.0 sample sets allows you to effectively manage your time and pace yourself, giving you the ability to finish any HCIP-Datacom-Advanced Routing & Switching Technology V1.0 practice test comfortably within the allotted time.
On the OSPFv3 network shown in the figure, OSPFv3 is enabled on the interfaces connecting R1, R2, and R3. The router ID of each router is 10.0.X.X, where X is the number of the router.
If you check detailed information about an LSA on R3, the command output shows that R1 and R2 are DRs on the network.
Options:
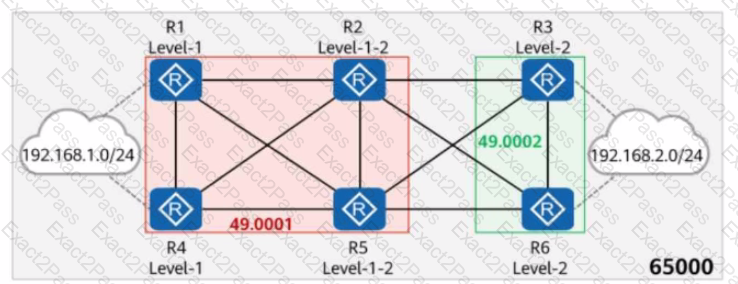
On the network shown in the figure, IS-IS runs on R1, R2, R4, and R5, and the area ID is 49.0001. IS-IS runs on R3 and R6, and the area ID is 49.0002. In AS 65000, R1, R3, R4, and R6 each establish iBGP peer relationships with R2 and R5. R2 and R5 are RRs (Route Reflectors), and R1, R4, R3, and R6 are clients. The iBGP peer relationships are established using Loopback0 on each router, and the router ID is 10.0.0.X/32, where X is the number of the router. R1 and R4 import the external route 192.168.1.0/24 to BGP through the import-route command, and R3 and R6 import the external route 192.168.2.0/24 to BGP through the import-route command. Which of the following statements are true?
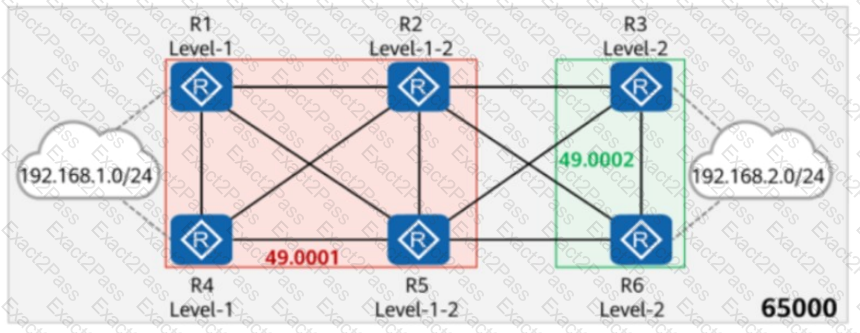
On the network shown in the figure, IS-IS runs on R1, R2, R4, and R5, and the area ID is 49.0001. IS-IS runs on R3 and R6, and the area ID is 49.0002. The import-route isis level-2 into level-1 command is configured on R2 and R5. In AS 65000, R1, R3, R4, and R6 each establish IBGP peer relationships with R2 and R5. R2 and R5 are RRs, and R1, R4, R3, and R6 are clients. The IBGP peer relationships are established using Loopback0. The IP address of Loopback0 on each router is 10.0.X.X/32, and the router ID is 10.0.X.X, where X is the number of the router. R1 and R4 import the external route 192.168.1.0/24 to BGP through the import-route command, and R3 and R6 import the external route 192.168.2.0/24 to BGP through the import-route command. Which of the following statements are true?
On the OSPFv3 network shown in the figure, area 1 is a common area. Which of the following statements are true?
In the figure, the company wants to ensure secure communication between the headquarters and branch, and isolate the R&D areas from non-R&D areas, without changing the current network deployment.
To meet this requirement, an administrator deploys BGP/MPLS IP VPN on the network.
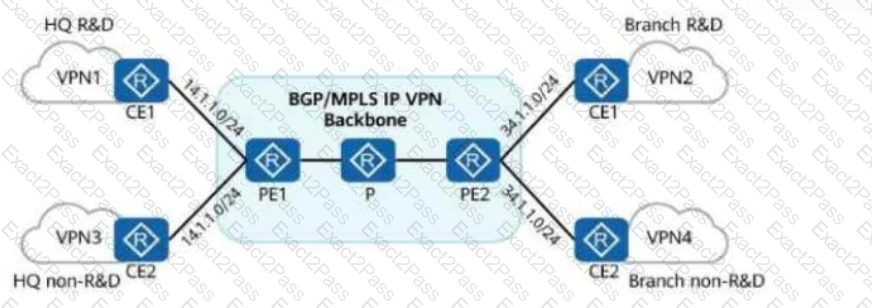
Which of the following statements are true?
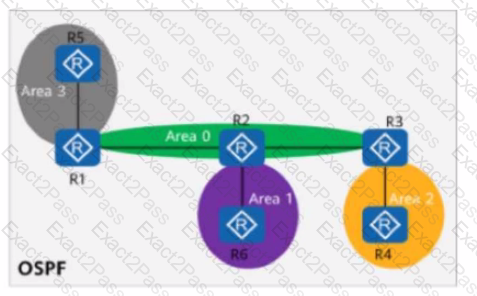
On the OSPF network shown in the figure, area 1 is an NSSA, area 2 is a stub area, and R4 imports an external route 10.0.4.4/32. The router ID of each router is 10.0.X.X, where X is the router number. The asbr-summary 10.0.4.0 255.255.255.0 command is configured in the OSPF processes of R1 and R3.
Match the following descriptions of routing tables with the corresponding routers:
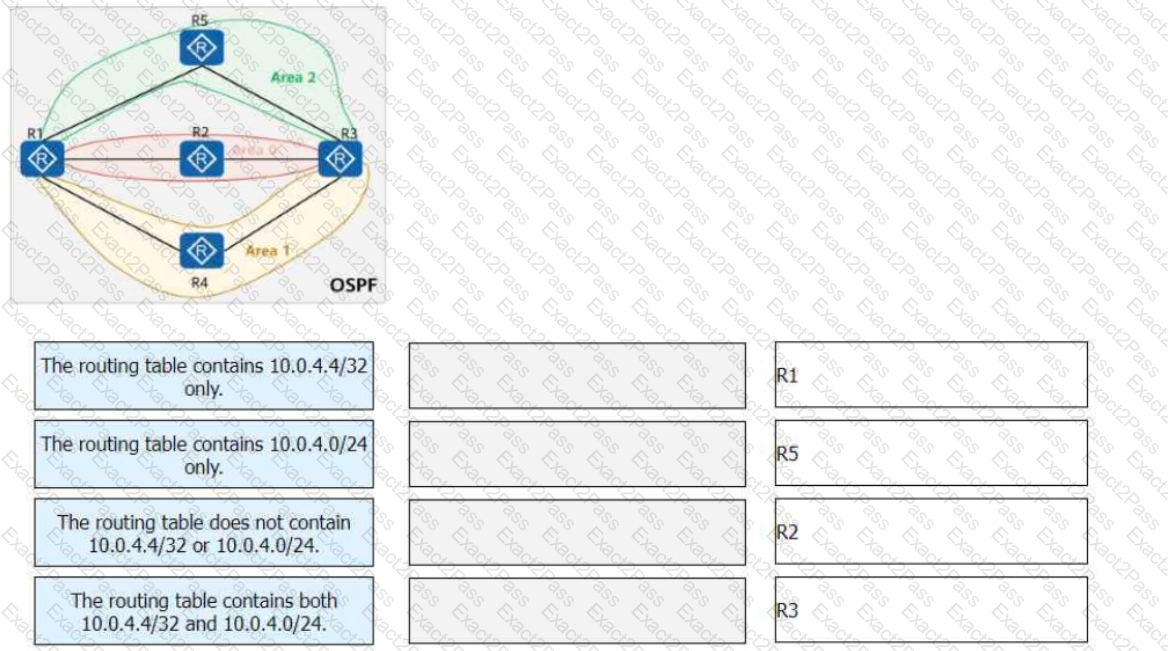
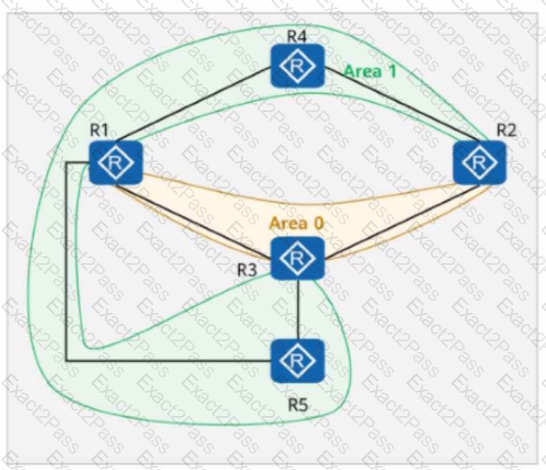
On the OSPF network shown in the figure, area 1 is a stub area, area 2 is a totally stub area, and area 3 is an NSSA. Which of the following LSAs does not exist in areas 1, 2, and 3?