Last Update 15 hours ago Total Questions : 208
The Microsoft Security Compliance and Identity Fundamentals content is now fully updated, with all current exam questions added 15 hours ago. Deciding to include SC-900 practice exam questions in your study plan goes far beyond basic test preparation.
You'll find that our SC-900 exam questions frequently feature detailed scenarios and practical problem-solving exercises that directly mirror industry challenges. Engaging with these SC-900 sample sets allows you to effectively manage your time and pace yourself, giving you the ability to finish any Microsoft Security Compliance and Identity Fundamentals practice test comfortably within the allotted time.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point
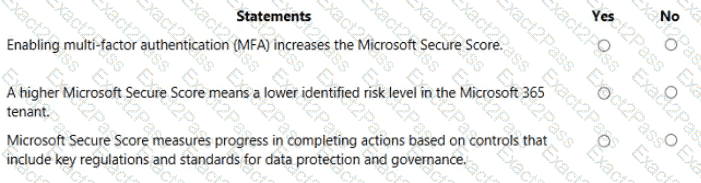
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

Select the answer that correctly completes the sentence.

Which Azure Active Directory (Azure AD) feature can you use to evaluate group membership and automatically remove users that no longer require membership in a group?
Which Microsoft 365 feature can you use to restrict users from sending email messages that contain lists of customers and their associated credit card numbers?
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.


