Last Update 23 hours ago Total Questions : 487
The CompTIA Linux+ Exam content is now fully updated, with all current exam questions added 23 hours ago. Deciding to include XK0-005 practice exam questions in your study plan goes far beyond basic test preparation.
You'll find that our XK0-005 exam questions frequently feature detailed scenarios and practical problem-solving exercises that directly mirror industry challenges. Engaging with these XK0-005 sample sets allows you to effectively manage your time and pace yourself, giving you the ability to finish any CompTIA Linux+ Exam practice test comfortably within the allotted time.
A newly hired junior administrator is studying the format of the /var/log/messages file. Which of the following commands should the administrator use to preserve the contents of the original file while also creating an identical file in the /home/admin directory?
A Linux administrator needs to restart a server and wants to see if any users are currently connected to it. Which of the following commands should the administrator run to find this information?
A DevOps engineer wants to work on a snapshot of the infrastructure as code configuration. Which of the following commands should the engineer use to accomplish this task?
A DevOps engineer wants to implement a new feature on the infrastructure as code configuration. Which of the following commands should the engineer use to accomplish this task?
An administrator set up a new user account called "test". However, the user is unable to change their password. Given the following output:
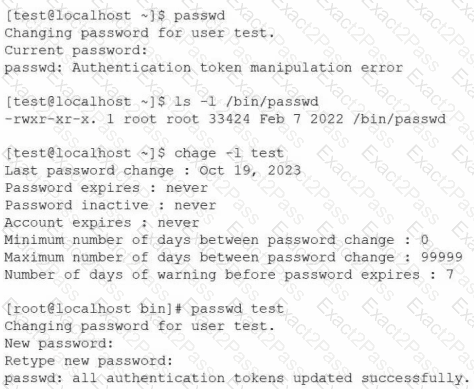
Which of the following is the most likely cause of this issue?
A Linux administrator recently downloaded a software package that is currently in a compressed file. Which of the following commands will extract the files?
A User on a Linux workstation needs to remotely start an application on a Linux server and then forward the graphical display of that application back to the Linux workstation. Which of the following would enable the user to perform this action?

