Last Update 6 hours ago Total Questions : 1237
The Implementing and Administering Cisco Solutions (200-301 CCNA) v1.1 content is now fully updated, with all current exam questions added 6 hours ago. Deciding to include 200-301 practice exam questions in your study plan goes far beyond basic test preparation.
You'll find that our 200-301 exam questions frequently feature detailed scenarios and practical problem-solving exercises that directly mirror industry challenges. Engaging with these 200-301 sample sets allows you to effectively manage your time and pace yourself, giving you the ability to finish any Implementing and Administering Cisco Solutions (200-301 CCNA) v1.1 practice test comfortably within the allotted time.
Which security element uses a combination of one-time passwords, a login name, and a personal smartphone?
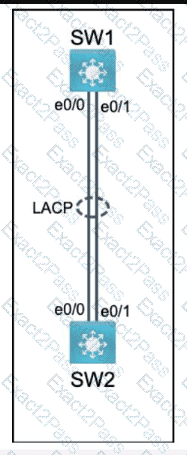
Physical connectivity is implemented between the two Layer 2 switches,
and the network connectivity between them must be configured.
I . Configure an LACP EtherChanneI and number it as 44; configure it
between switches SWI and SW2 using interfaces EthernetO/O and
Ethernet0/1 on both sides. The LACP mode must match on both ends.
2. Configure the EtherChanneI as a trunk link.
3. Configure the trunk link with 802. Iq tags.
4. Configure VLAN 'MONITORING' as the untagged VLAN of the
EtherChannel.
==================
Guidelines
This is a lab item in which tasks will be performed on virtual devices.
• Refer to the Tasks tab to view the tasks for this lab item.
• Refer to the Topology tab to access the device console(s) and perform the tasks.
• Console access is available for all required devices by clicking the device icon or using
the tab(s) above the console window.
• All necessary preconfigurations have been applied.
• Do not change the enable password or hostname for any device.
• Save your configurations to NVRAM before moving to the next item.
• Click Next at the bottom of the screen to submit this lab and move to the next question.
• When Next is clicked, the lab closes and cannot be reopened.
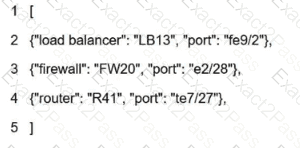
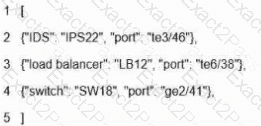
What is represented by the word "LB13" within this JSON schema?
What is a characteristic of a Layer 2 switch?
What is a reason to implement HSRP on a network?
Which level of severity must be set to get informational syslogs?
When configuring IPv6 on an interface, which two IPv6 multicast groups are joined? (Choose two)
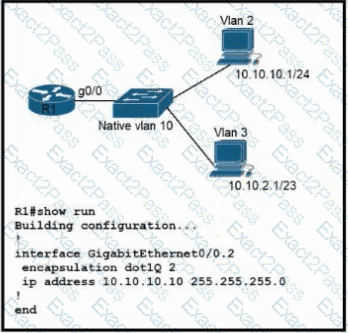
Refer to the exhibit. Configurations for the switch and PCs are complete.
Which configuration must be applied so that VLANs 2 and 3 communicate back and forth?
What is a characteristic of a Layer 2 switch?
Refer to the exhibit.
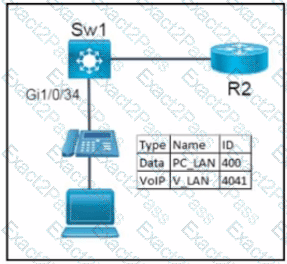
Network services must be enabled on interface Gil/0734. Which configuration meets the needs for this implementation?
A)
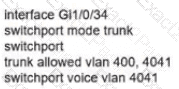
B)
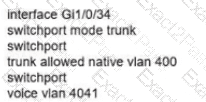
C)
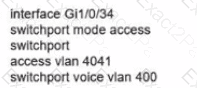
D)
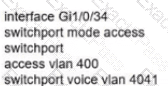
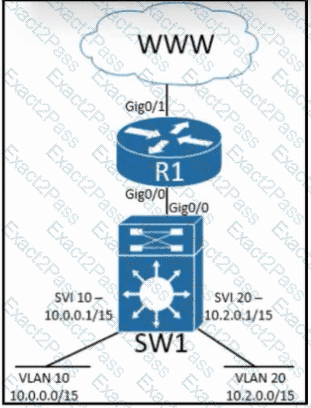
Refer to the exhibit. Inter-VLAN routing is configured on SW1. Client A is running Linux as an OS in VLAN 10 with a default gateway IP 10.0.0.1 but cannot ping client B in VLAN 20 running Windows. What action must be taken to verify that client A has the correct IP settings?

Refer to the exhibit. An LACP EtherChannel between two directly connected switches is in the configuration process.
Which command must be configured on switch SW2’s Gi0/1-2 interfaces to establish the channel to SW1?
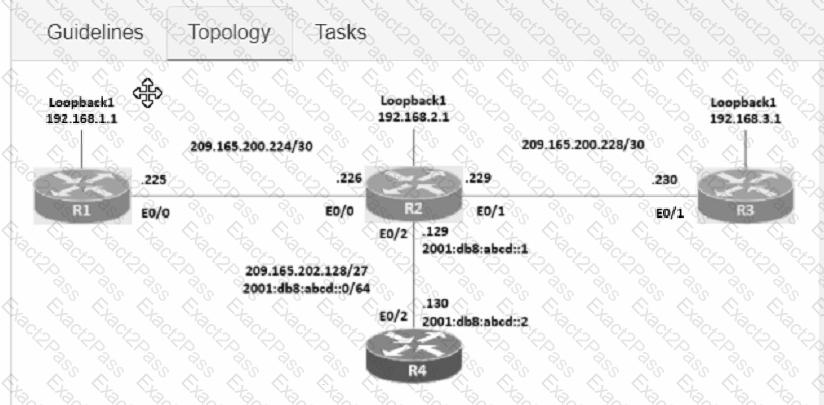
Connectivity between four routers has been established. IP connectivity must be configured in the order presented to complete the implementation. No dynamic routing protocols are included.
1. Configure static routing using host routes to establish connectivity from router R3 to the router R1 Loopback address using the source IP of 209.165.200.230.
2. Configure an IPv4 default route on router R2 destined for router R4.
3. Configure an IPv6 default router on router R2 destined for router R4.
Why would a network administrator implement the HSRP protocol?
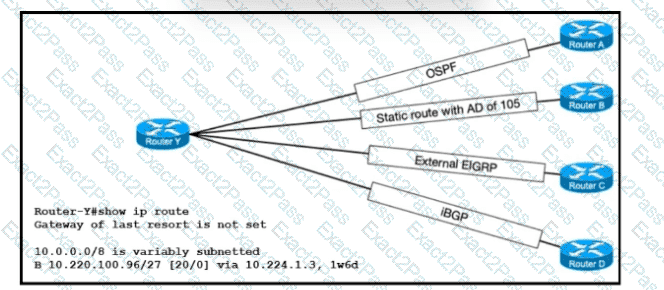
Refer to the exhibit. The route for 10.220.100.96/27 has been very unstable. The same route has four backups to routers A, B, C, and D via the respective methods. The routing protocol defaults for router Y have not been changed. When the current route for 10.220.100.96/27 becomes unavailable, which router will router Y use to route traffic to 10.220.100.96/27?
What is represented by the word "switch" within this JSON schema?
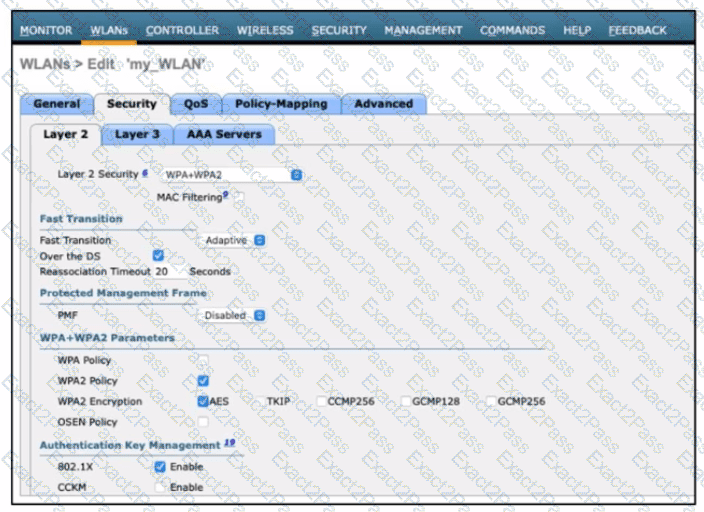
Refer to the exhibit. A network engineer is configuring a wireless LAN with Web Passthrough Layer 3 Web Policy. Which action must the engineer take to complete the configuration?
Which interface is used to send traffic to the destination network?
10.249.210.56/25 [90/6144] via G0/15
10.249.210.56/25 [90/45053] via G0/13
10.249.210.56/25 [110/3693] via G0/16
10.249.210.56/25 [110/360] via G0/12
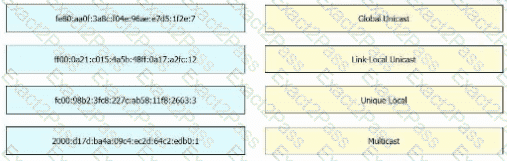
Drag and drop the IPv6 address from the left onto the type on the right.
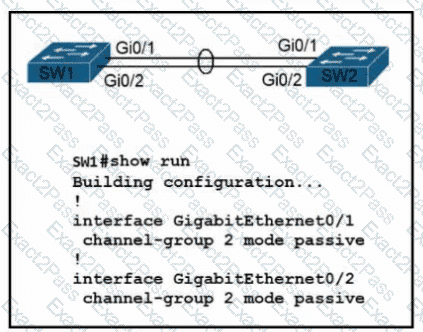
Refer to the exhibit. Which configuration enables SW2 to establish an LACP EtherChannel?
What is the default interface for in-band wireless network management on a WLC?
Which statement describes virtualization on containers?
Which fact must the engineer consider when implementing syslog on a new network?
What is the total number of users permitted to simultaneously browse the controller management pages when using the AireOS GUI?
Which role does AI play in monitoring network data flow?
Which interface is used to send traffic to the destination network?
O 10.76.170 161/26 |110/102] via FO/17
O 10.76.170 161/26[110/27e31] via FO/20
R 10.76.170.161/261120/15] via FO/8
R 10.76.170.161/26 [120/10] via FO/12
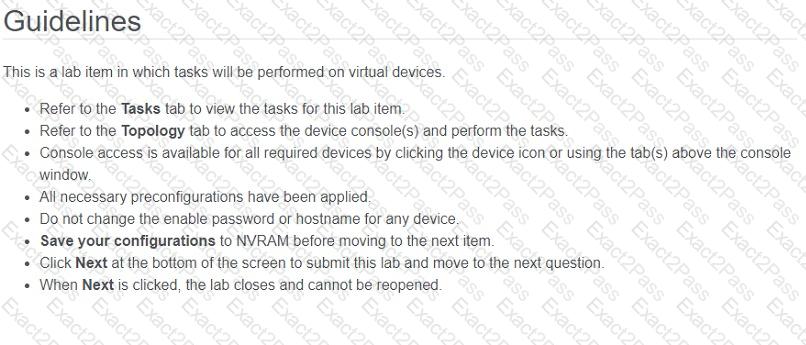
All physical cabling between the two switches is installed. Configure the network connectivity between the switches using the designated VLANs and interfaces.
1. Configure VLAN 100 named Compute and VLAN 200 named Telephony where required for each task.
2. Configure Ethernet0/1 on SW2 to use the existing VLAN named Available.
3. Configure the connection between the switches using access ports.
4. Configure Ethernet0/1 on SW1 using data and voice VLANs.
5. Configure Ethemet0/1 on SW2 so that the Cisco proprietary neighbor discovery protocol is turned off for the designated interface only.
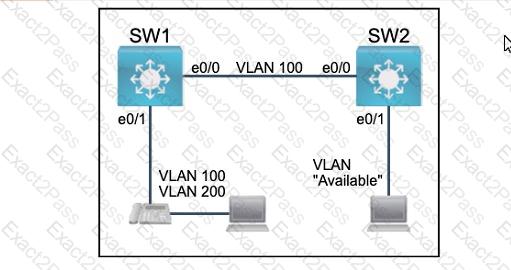
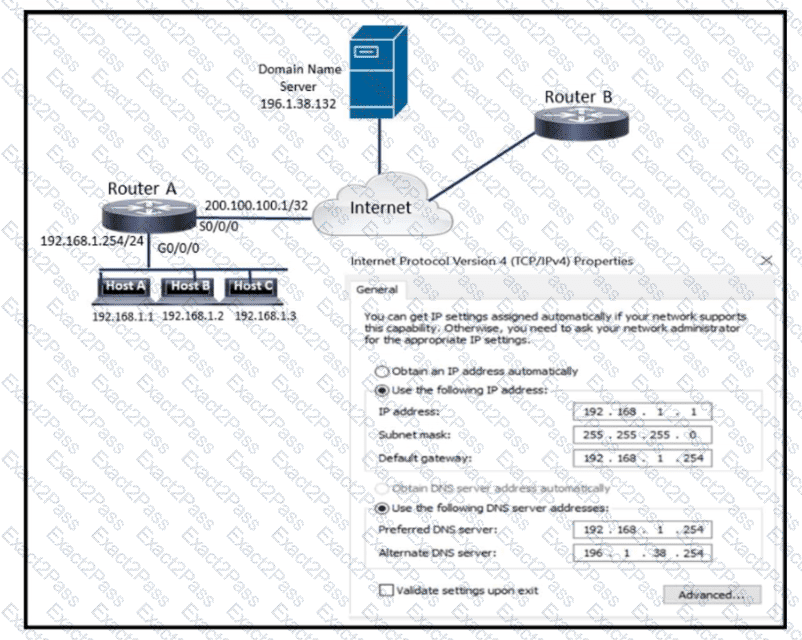
Refer to the exhibit. What is preventing host A from reaching the internet?
What is represented in line 3 within this JSON schema?
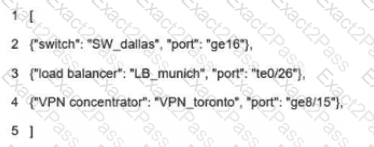
What is a characteristic of private IPv4 addressing?
Which technology allows multiple operating systems lo run a single physical server?
Refer to the exhibit.

What is occurring on this switch?
What is a characteristic of private IPv4 addressing?
How does automation leverage data models to reduce the operational complexity of a managed network?
Why are API keys used to enforce rate limiting?
Which header must be included in a REST request from an application that requires JSON-formatted content?
What differentiates the TCP and UDP protocols?
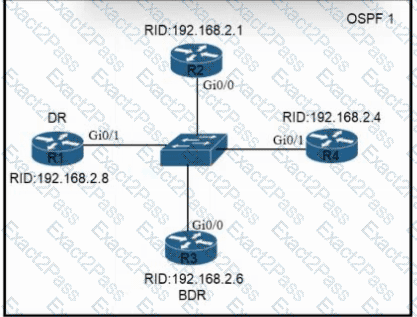
Refer to the exhibit. All routers In the network are configured. R2 must be the DR. After the engineer connected the devices, R1 was elected as the DR. Which command sequence must be configured on R2 to be elected as the DR in the network?

What is a function of Layer 3 switches?
An organization developed new security policies and decided to print the policies and distribute them to all personnel so that employees review and apply the policies. Which element of a security program is the organization implementing?
Which switch port configuration must be configured when connected to an AP running in FlexConnect mode, and the WLANs use flex local switching?
Which interface condition is occurring in this output?

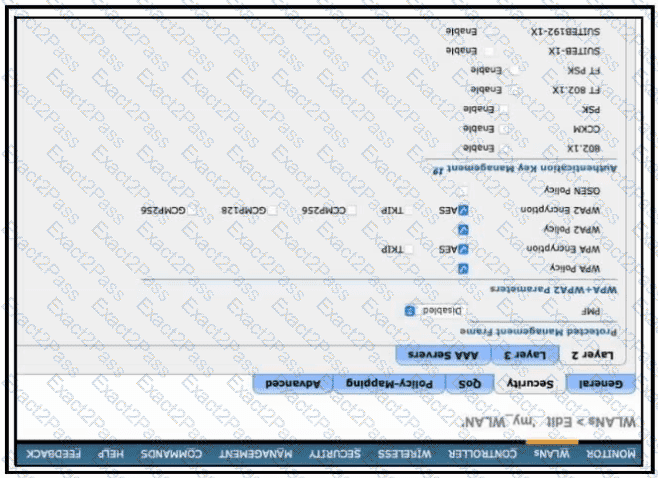
Refer to the exhibit.
Which configuration is needed to configure a WLAN with WPA2 only and with a password that is 63 characters long?
Refer to the exhibit.
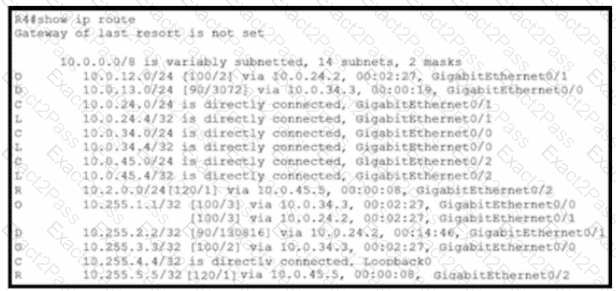
Of the routes learned with dynamic routing protocols, which has the least preferred metric?
What is the main capability of multifactor authentication?
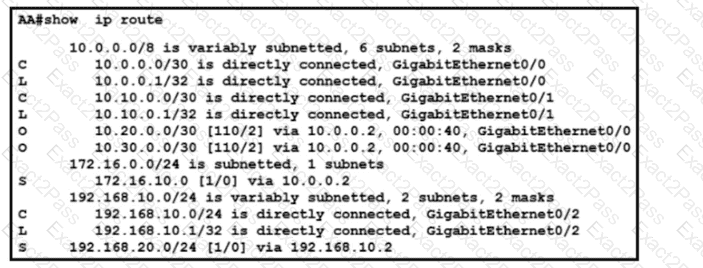
Refer to the exhibit. What is the administrative distance for the advertised prefix that includes the host IP address 192.168.20.1?
Which key function is provided by the data plane?

