Last Update 13 hours ago Total Questions : 630
The Implementing Cisco Enterprise Advanced Routing and Services (300-410 ENARSI) content is now fully updated, with all current exam questions added 13 hours ago. Deciding to include 300-410 practice exam questions in your study plan goes far beyond basic test preparation.
You'll find that our 300-410 exam questions frequently feature detailed scenarios and practical problem-solving exercises that directly mirror industry challenges. Engaging with these 300-410 sample sets allows you to effectively manage your time and pace yourself, giving you the ability to finish any Implementing Cisco Enterprise Advanced Routing and Services (300-410 ENARSI) practice test comfortably within the allotted time.
Exhibit:
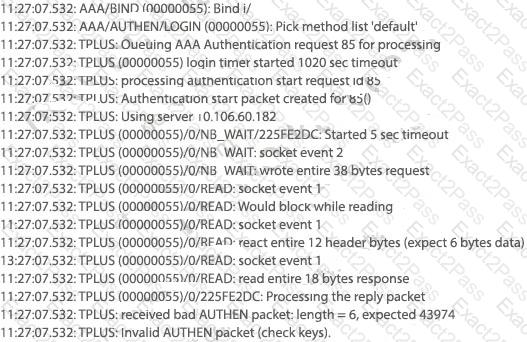
Which action resolves the authentication problem?
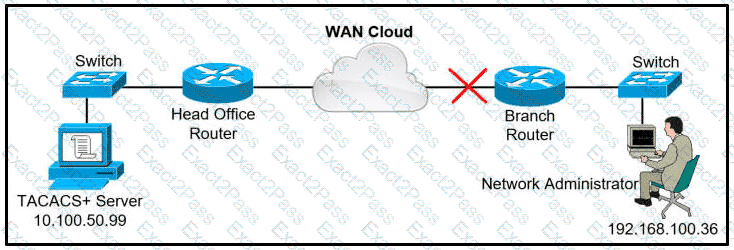
A network administrator is trying to access a branch router using TACACS+ username and password credentials, but the administrator cannot log in to the router because the WAN connectivity is down. The branch router has following AAA configuration:
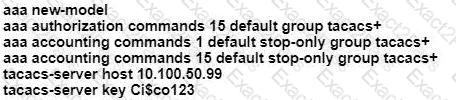
Which command will resolve this problem when WAN connectivity is down?
Refer to the exhibit.
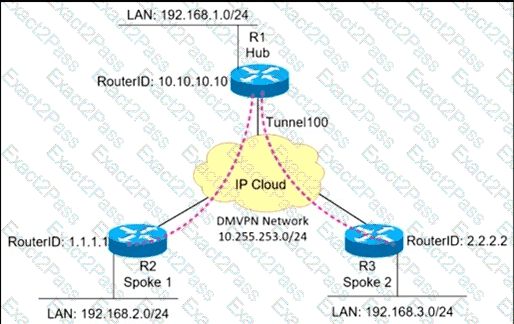
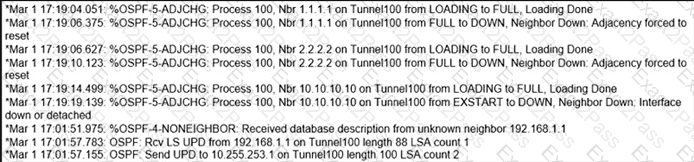
A network administrator sets up an OSPF routing protocol for a DMVPN network on the hub router. Which configuration required to establish a DMVPN tunnel with multiple spokes?
What are two MPLS label characteristics? (Choose two.)
Refer to the exhibit.
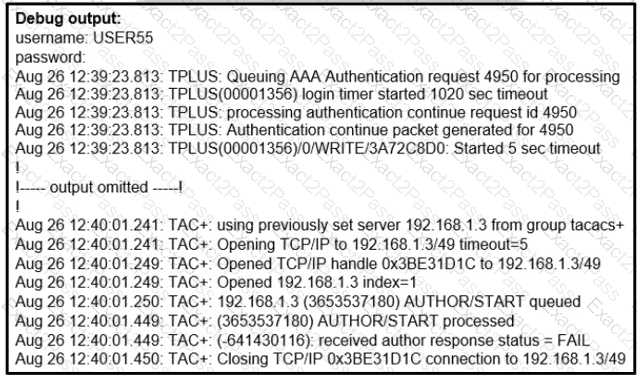
A network administrator logs into the router using TACACS+ username and password credentials, but the administrator cannot run any privileged commands Which action resolves the issue?
In a DMVPN network, the Spoke1 user observed that the voice traffic is coming to Spoke2 users via the hub router. Which command is required on both spoke routers to communicate directly to one another?
A DMVPN single hub topology is using IPsec + mGRE with OSPF. What should be configured on the hub to ensure it will be the designated router?
Refer to the exhibit.
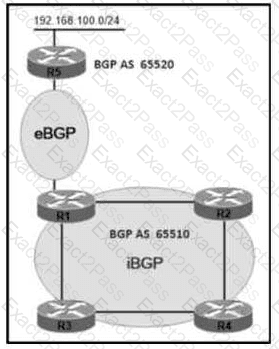
AS65510 iBGP is configured for directly connected neighbors. R4 cannot ping or traceroute network 192 168.100.0/24 Which action resolves this issue?
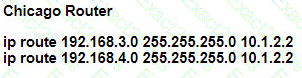
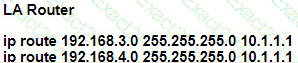
Refer to the exhibits.
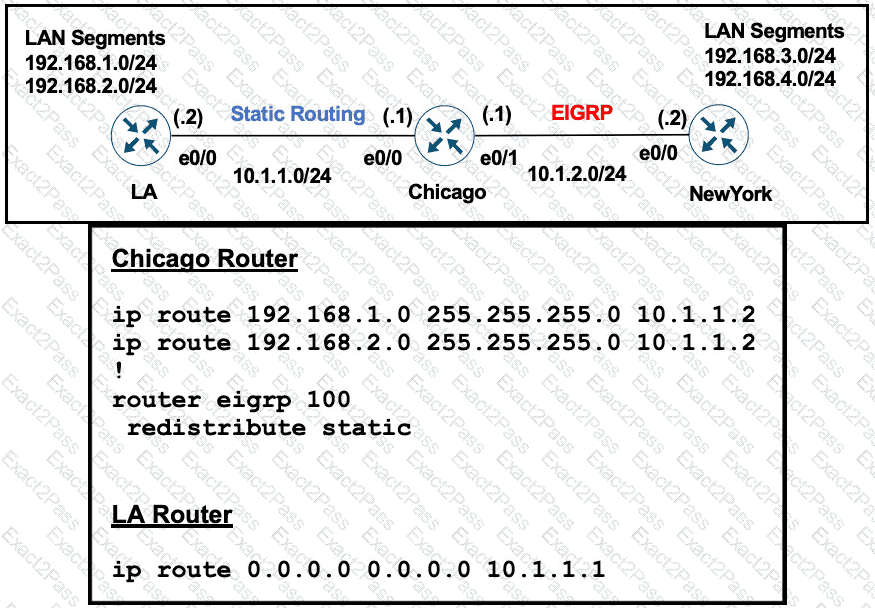
A user on the 192.168.1.0/24 network can successfully ping 192.168.3.1, but the administrator cannot ping 192.168.3.1 from the LA router. Which set of configurations fixes the issue?
A)
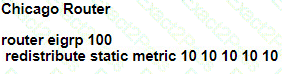
B)

C)
D)
Refer to the exhibit.
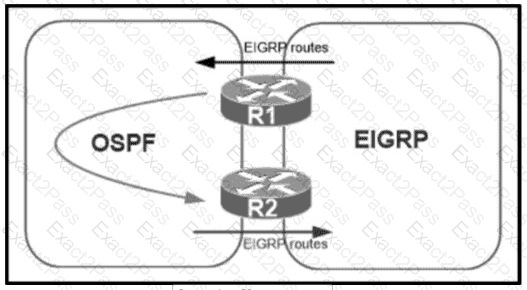
A network administrator configured mutual redistribution on R1 and R2 routers, which caused instability in the network. Which action resolves the issue?
An engineer must configure a Cisco router to initiate secure connections from the router to other devices in the network but kept failing. Which two actions resolve the issue? (Choose two.)
Refer to the exhibit.
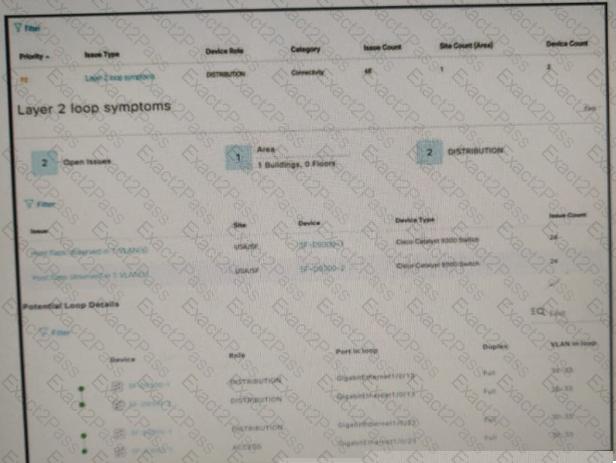
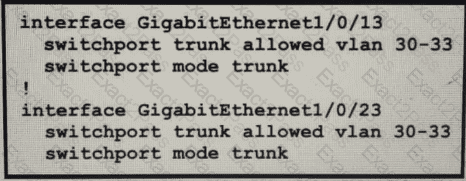
An engineer identifier a Layer 2 loop using DNAC. Which command fixes the problem in the SF-D9300-1 switch?

